By stream of events:
A group of hackers called Shadow Brokers hacked into the NSA’s systems and pulled out a bunch of data from an NSA-run organization called the Equation Group. In this data, there are many 0-day exploits used by the NSA to attack, spy and steal data of many users, organizations, and governments around the world to serve the public. activityintelligence agency.
| Join the channel Telegram belong to AnonyViet 👉 Link 👈 |
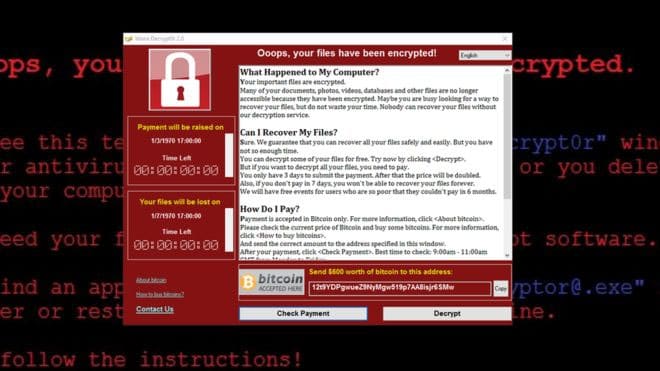
Among them, there is a particularly dangerous 0-day that was publicized last April targeting all versions from XP to Windows 10. This bug targets the Windows SMB (file sharing) service that allows attackers to execute. remote execution, roughly speaking, an attacker can control a remote computer, such as calling up a cmd with SYSTEM privileges, and manipulate it there without the user’s knowledge.
WannaCry takes advantage of this exploit, when it infects one machine, it scans other machines on the same LAN, and executes the exploit. Once the exploitdc is messed up, no has control and operation on the new machine, it will automatically copy itself to the new machine it can control and run -> continue to execute to all the remaining machines.
The most dangerous point leading to possible attacks from outside the LAN is that the machines do not turn on the Firewall, block port 445 of smb or disable the File sharing service. Attacker can create a system that automatically scans the public ip range to find machines that open port 445 to perform exploits.
Or the attacker can use phising email to trick the user into clicking on the link, or open an attachment containing a dropper, this dropper downloads the exploit code and runs it to create a backdoor, from which the attacker can enter, or simpler. it always download WannaCry and run.
The difference that makes WannaCry dangerous is that it uses an exploit to expand the infection range, and it should be emphasized that this exploit can create a backdoor with SYSTEM permissions (equivalent to root in Linux) so it has all rights to the system, from disabling AV, disabling Firewall, modifying or deleting system files, disabling protection mechanisms altogether.
Just one infected node is all the machines in the same network if not updated will stick. It is even more dangerous in Vietnam when users use illegal Win, do not update, disable Firewall, and old windows like XP (MS has stopped supporting XP, but this time still have to release a patch to fix this error). XP)
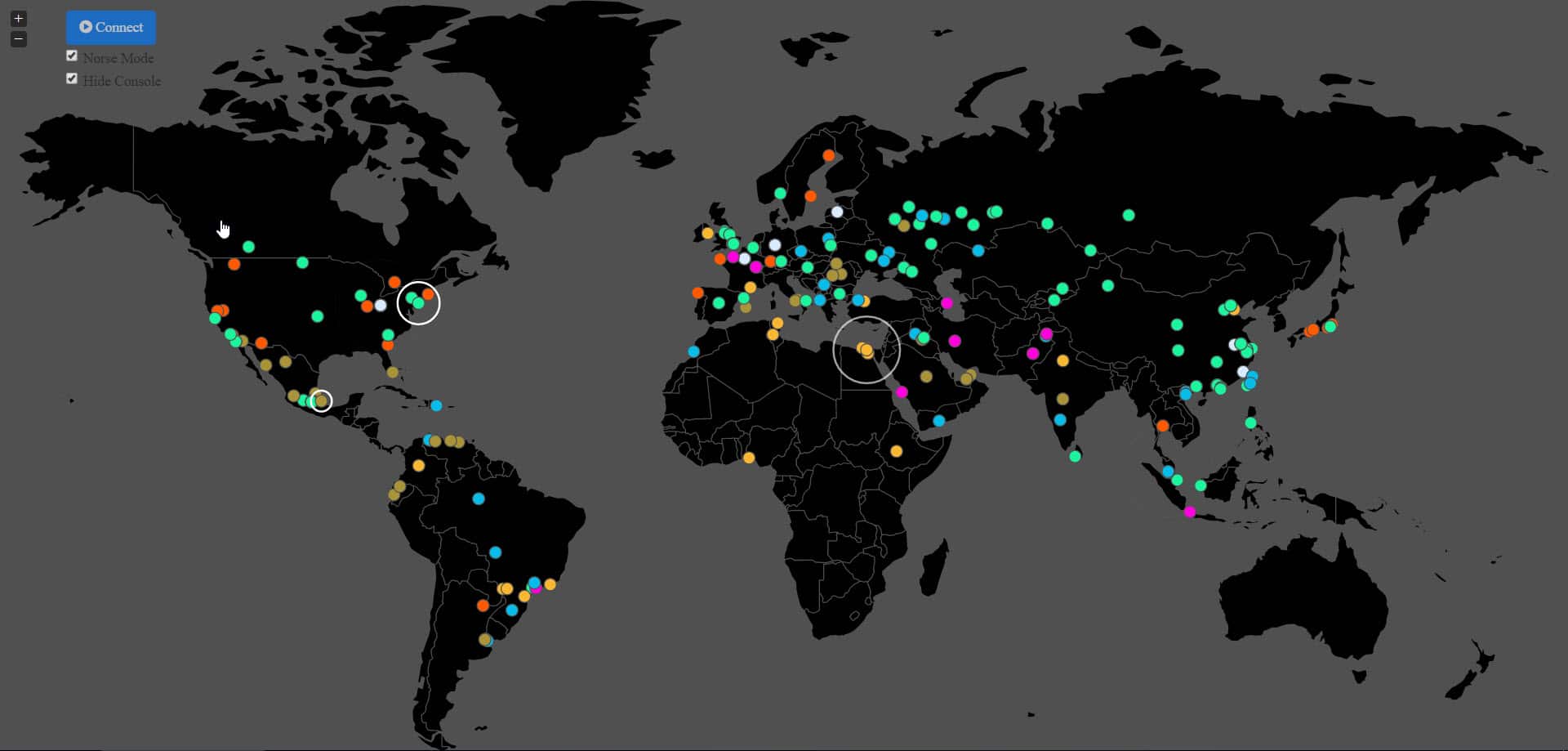
Watch live cyber attacks around the world
Instructions on how to prevent Ransomware WannaCry
Note:
Do not download, do not open any files of unknown origin, especially files: exe, pdf
Method 1: Update Windows
The most important thing is that you must Update Windows to update to the latest Microsoft patch. Do it now, don’t wait any longer.
Method 2: Use the tool RansomFree
Recently, the company Cybereason just released the RansomeFree tool to help you detect and destroy WannaCry as soon as it appears on your computer.
If your computer is infected with WannaCry Ransomware, then RansomeFree will also help you limit the spread of other files, avoiding all data encryption.
Please note: Depending on the location, some files may still be encrypted by the WannaCry ransomware. However, as shown in this video, most of the files are protected, and the ransomware is no longer spreading.
Or install and update the latest AntiVirus software such as Kaspersky, Avast, Avira…
Method 3: Block Port
Use Firewall available on Windows, or the Firewall of antivirus programs blocks the following ports:
- TCP ports 137, 139, and 445
- UDP ports 137 and 138
Use the PowerShell command
Go to Run: type Powershell and paste the following command
netsh advfirewall firewall add rule name="Disable SMB" dir=in action=block protocol=TCP localport=139 netsh advfirewall firewall add rule name="Disable SMB" dir=in action=block protocol=TCP localport=445 netsh advfirewall firewall add rule name="Disable SMB2" dir=in action=block protocol=udp localport=445 netsh advfirewall firewall add rule name="Disable RDC" dir=in action=block protocol=TCP localport=3389 netsh advfirewall firewall add rule name="Disable 137" dir=in action=block protocol=TCP localport=137 netsh advfirewall firewall add rule name="Disable 138" dir=in action=block protocol=TCP localport=138
Use on the interface
How to use Firewall on Windows:
Enter Control Panel –> Firewall
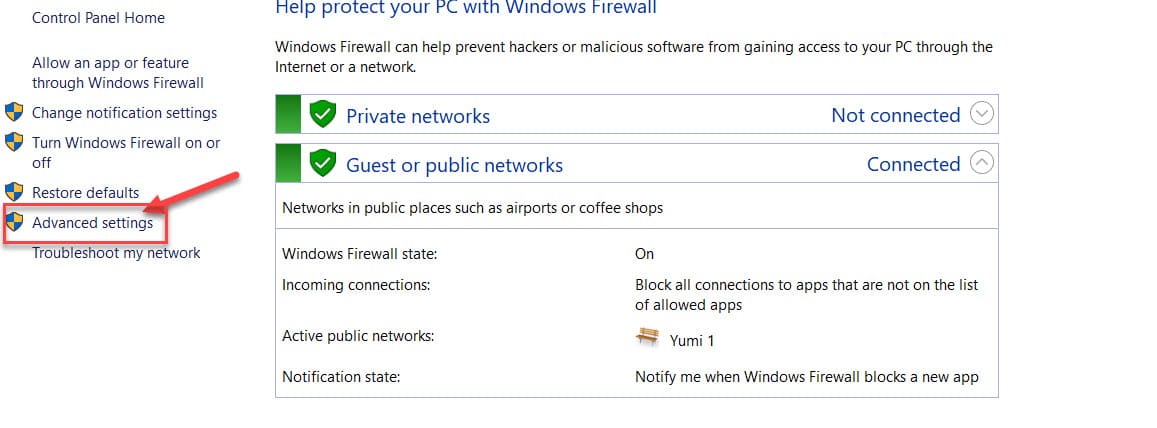
Repeat for both
Inbound Rules and Outbound Rules
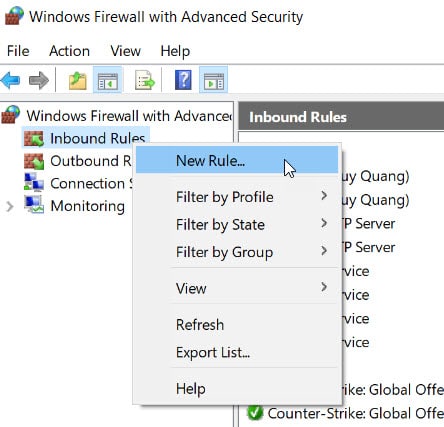
Right click Inbound Rules, select New Rule…
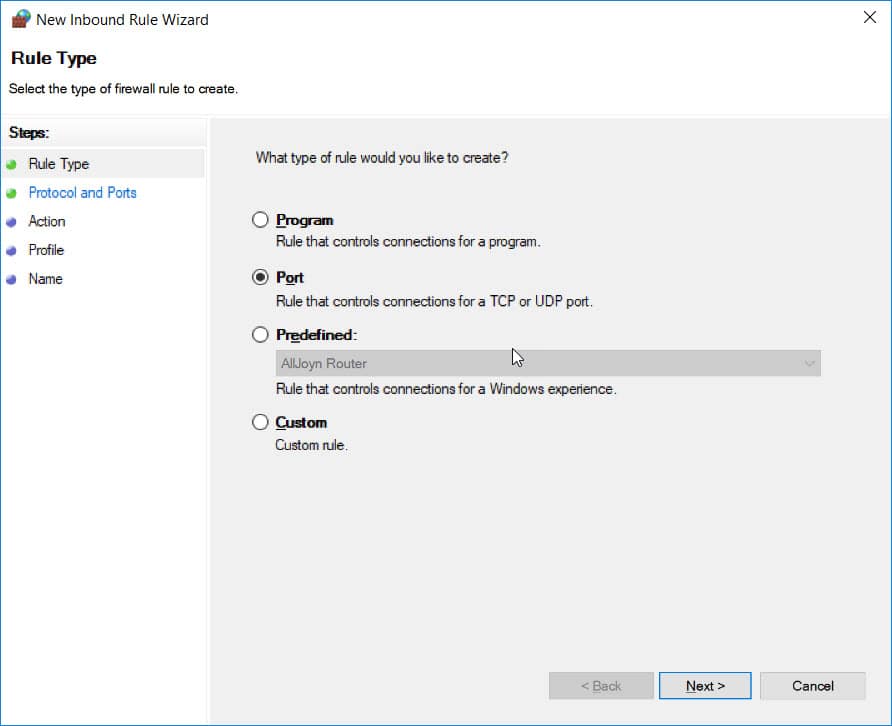
Check box Port then press next
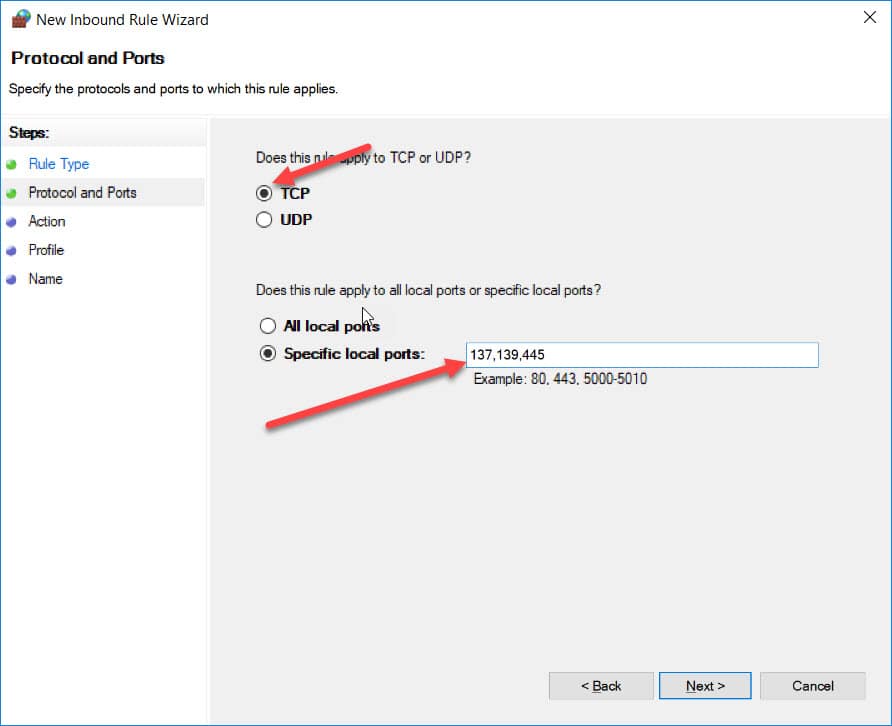
Continue to select TCP, under Specific local ports: 137,139,445
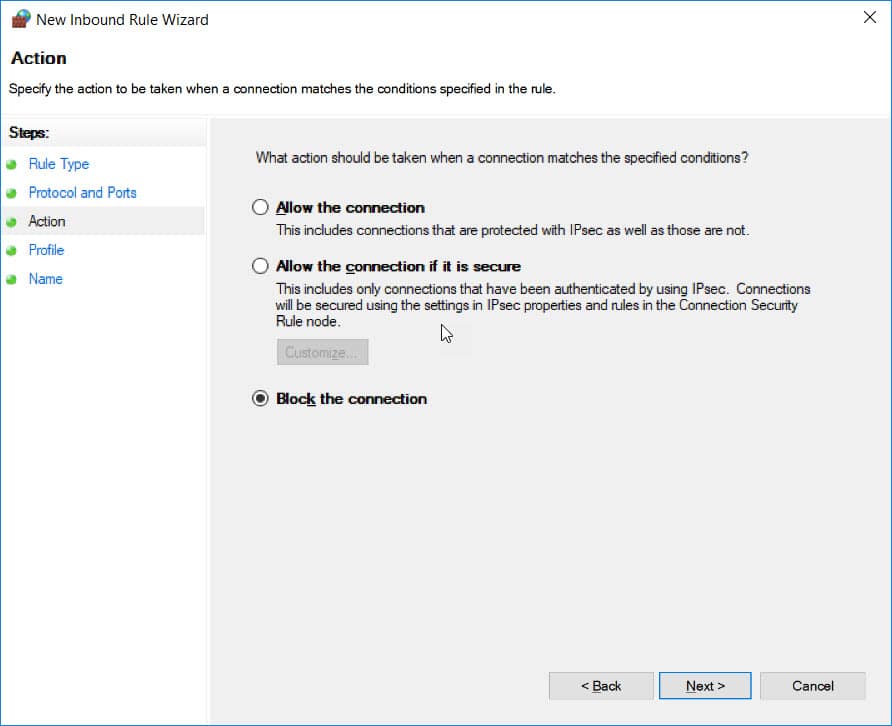
Select Block Connection
Continue to click Next,
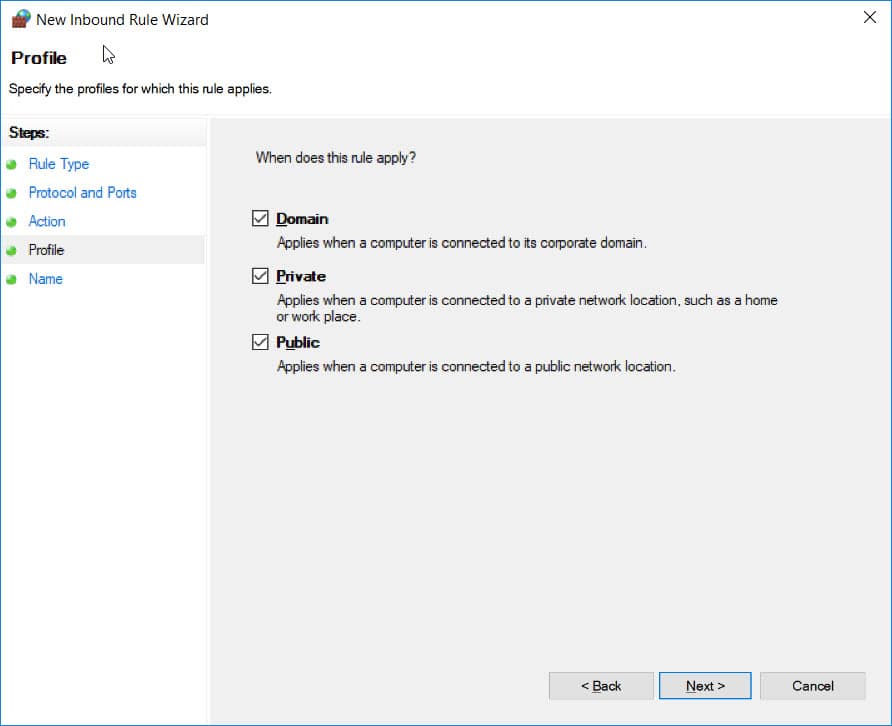 Go to Name You can order anything.
Go to Name You can order anything.
Then repeat Step 1 in the same way, block port UDP: 137,138
Then to Outbound Rulesexecute as Inboud Rules
Method 4: Turn off SMB mode
You need to start the Power Shell, go to run and type the PowerShell command
Personal computer using Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8, and Windows Server 2012
Copy the command below into PowerShell
sc.exe config lanmanworkstation depend= bowser/mrxsmb20/nsi sc.exe config mrxsmb10 start= disabled sc.exe config lanmanworkstation depend= bowser/mrxsmb10/nsi sc.exe config mrxsmb20 start= disabled Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol
If there is an error, just ignore it, copy it and press Enter
Server using Windows 8 and Windows Server 2012
Copy the command below into PowerShell
Set-SmbServerConfiguration -EnableSMB1Protocol $false
Set-SmbServerConfiguration -EnableSMB2Protocol $false
Server use Windows 7, Windows Server 2008 R2, Windows Vista, and Windows Server 2008
Copy the command below into PowerShell
- Disable SMBv1
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Type DWORD -Value 0 -Force
- Disable SMBv2
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB2 -Type DWORD -Value 0 -Force
You need to restart computer to finish
Remove SMB v1 in Windows 8.1, Windows 10, Windows 2012 R2, and Windows Server 2016 using the interface
Windows Servers: Go to Server Manager
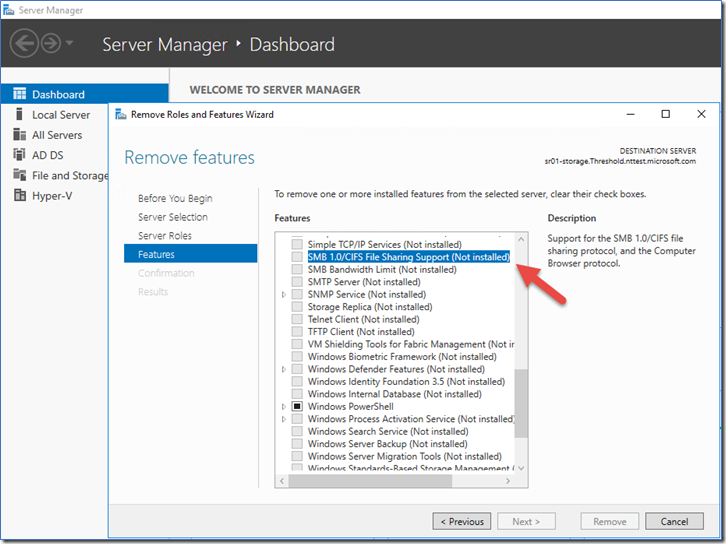
Windows Servers: Using PowerShell
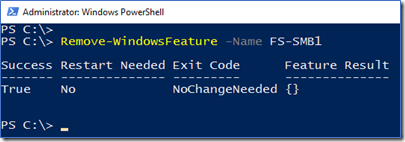
Remove-WindowsFeature FS-SMB1
Personal computer: Go to Control Panel and select Add or Remove Programs
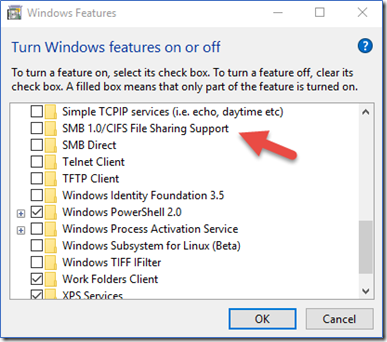
Personal computer:
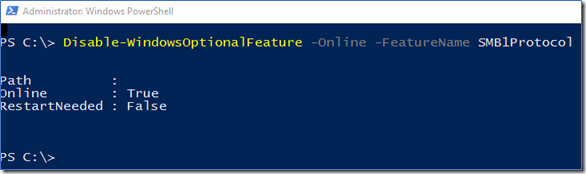
Use PowerShell
Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol
What if I get infected with WannaCry Ransomware?
– Immediately disconnect the internet wifi network and the internal LAN to not infect other computers in the network
– Immediately install RansomFree (in Method 2) to avoid infection