This is a summary of some account hijacking methods that Hackers often use to attack you. Learn how to identify and prevent data loss. Your writing Truong Hieu Posted on J2Team.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
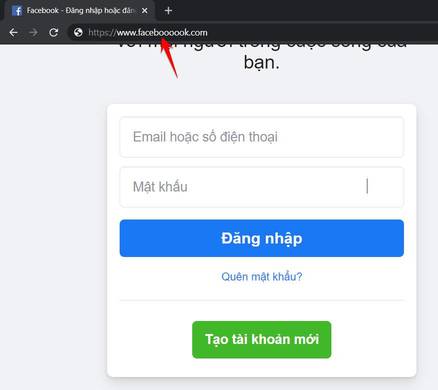
Phishing – fake login page
Phishing is a type of fake login page. You guys just walk around the groups or fanpage and see comments sharing xxx links or hot videos. Click on the new Facebook login to see that 100% of it is a fake website to take over your account. This is the way that trickers in Vietnam use quite commonly to drive chickens. To avoid Phishing you can use Anti-Phishing utility by HieuPC.
Sniffing – capture packets
Sniffing is also known as packet theft. Somehow Hacker access to your wifi network, internet. Then use packet capture software such as Wireshark, Ettercap … to view the packet transmitted from your PC, mobile and retrieve the cookie site you have logged in to, or when you enter the password, it takes the packet that you declare. report username, password (in case the website does not use SSL – no https).
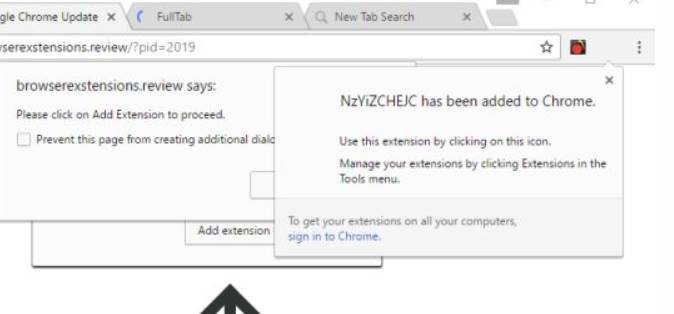
Injection – attach malicious code
This is how they advertise applications, extensions on chrome, or js code to get like fanpage, change Facebook interface, get tokens, even cookies…. After you install malicious extensions on your computer, they will get Cookies and send them to hackers or even login account information.
So do not install extensions if you do not know the source and are underrated.
Trojans, malware, keyloggers – malicious code
Let’s call it Virus for quick. This way is roughly attaching a virus to tools, tools, software, document files: Open it and you will be infected with the virus immediately. This virus can have many different tasks depending on the intentions of the creator. It could be encrypting all your documents and blackmailing (eg wannacry virus), creating a botnet to ddos a certain website, or simply recording keystrokes, taking screenshots, sending user logs. -pass when you log into certain sites.
This method is new but old. The old here is the current 4.0 technology, so the anti-virus software is very good, can scan more than 90% of viruses and trojans. New here is that there are still highly qualified hackers, creating viruses that virus scanning software has not detected yet. In my opinion, if this method is used, it interferes deeply with your computer system, so hackers can do a lot of things, this way is the most dangerous. So always be careful when opening a program or a file of unknown origin
Brute Force Attack, Dictionary Attack – detect Password
In addition to the above ways, there are also some tricks to take over your account. Eg Brute Force Also known as password discovery, password guessing software is used. They will have a database of common passwords and then run until they are correct. This way, some large sites such as Facebook, Google, banking websites, etc. can no longer be used because they enter too many times to allow eating capcha fruits to check if they are real users, or forbid login in an account. specific time, or lock your account for your protection.
Hack Database – Server Attack
This way does not need to be discussed anymore, this is how Hackers can see all the Database information that you are using to save data, this way is usually an attack without specific personal or organizational goals. Simply, any website or application that fails can be hacked by a Local Hacker (hacking both hosting or server) or by SQL Injection to exploit all database data. Usually the password stored on the Database is in the form of MD5 or encrypted according to a certain standard, hacking the database and decrypting the password is another matter.
Some problems with Facebook account hijacking
Your account was hacked to do: These accounts taken to hackers will change emails, change phone numbers and sell them to people who need to use them. For example, used to run ads, seeding (create fake interactions), used for use (clone/via). Spam group, or as a lure to hack other facebooks by phishing.
Is it dangerous to get a cookie: Once they get your cookie, Hacker will manipulate almost 90% of what you do. However, in some operations such as adding email, kicking number or updating password, turning on 2fa, operations to change account information, they still need a password. Nowadays, some young people including myself have a way to just need a cookie, add an email to Facebook and set that new email as the main email without a password, then use the reset password function to send it to that new email. As a result, you will lose your account.
What are Facebook tokens: Token is a piece of code generated by Facebook to verify the user with the Facebook API. When you request something, you need this code. If your Facebook token is stolen, it can do a few things: seeding, spamming, sharing links, crawling data, managing ads accounts …. Some other functions such as token can see your messages, but as far as I remember, Facebook has already locked that API.
How to secure your account: Add extra email, extra phone number. Turn on 2fa (2-step verification by sms or Google Authenticator..), avoid opening files, avoid installing applications, extensions of unknown origin. Do not login on sites that do not match the official domain…
Above are the ways I know, limited knowledge, hope you know it, read it for fun. If you don’t know, avoid it.