Shifting left is a development principle, clearly stating that security will move from the right (or end) of the software programming life cycle (SDLC) to the left (start). In other words, security should be designed and integrated into all stages during development. This new change requires developers to own security and understand security principles. Good news is that there are many tools available to help developers in this process.
| Join the channel Telegram belong to Anonyviet 👉 Link 👈 |
In this article, we will divide the application security into the main fields and learn some free open source solutions to help developers and organizations ensure all stages of SLDC, these changes help them improve their overall software quality and security.
Shifting Left is like adding additional work to developers’ software, but in reality, it allows developers to learn more about security practices, help reduce the time of defective milk and take a little more time to build great applications.
Application security in software programming process
The most important thing is that you have to realize that all application security holes cannot be repaired by a single software. Successful security requires multiple classes with many defense routes for different stages of SDLC.
The tools we will learn include:
- SAST – Static Application Security Testing (Static application security check)
- DAST – Dynamic Application Security Testing
- IAST – Integrated application Security Testing (Integrated application security test)
- Rasp -Run-time Application Self Protection (self-protection application during running time)
- Dependency Scanning
- Secrets detection
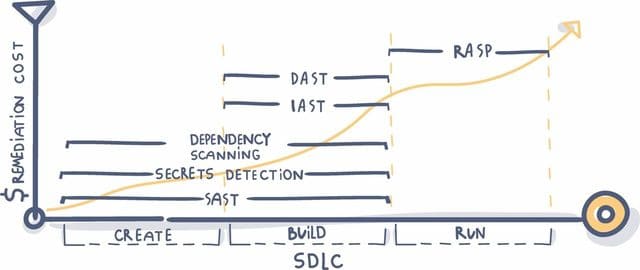
Although the truth is that the holes are chosen to check early will be cheaper and easier to overcome, you cannot search for all holes in the early stages of the development process. Security needs to spread evenly and be concerned in the entire SDLC process.
SAST
Static application system testing – Also known as “White Box Testing”, the earliest appears and is the most common type of automatic application security. Sast scan the source code of the application to find all known gaps. Because SAST does not require a compilation application or running when looking for a hole (unlike Dast), it is deployed very early in SDLC.
It also performs coding instructions and standards without basic code execution. This application test portfolio has a lot of solutions available, so when deciding to use a solution, make sure that solution is supported and regularly updated. Here are some of the best free Sast tools.
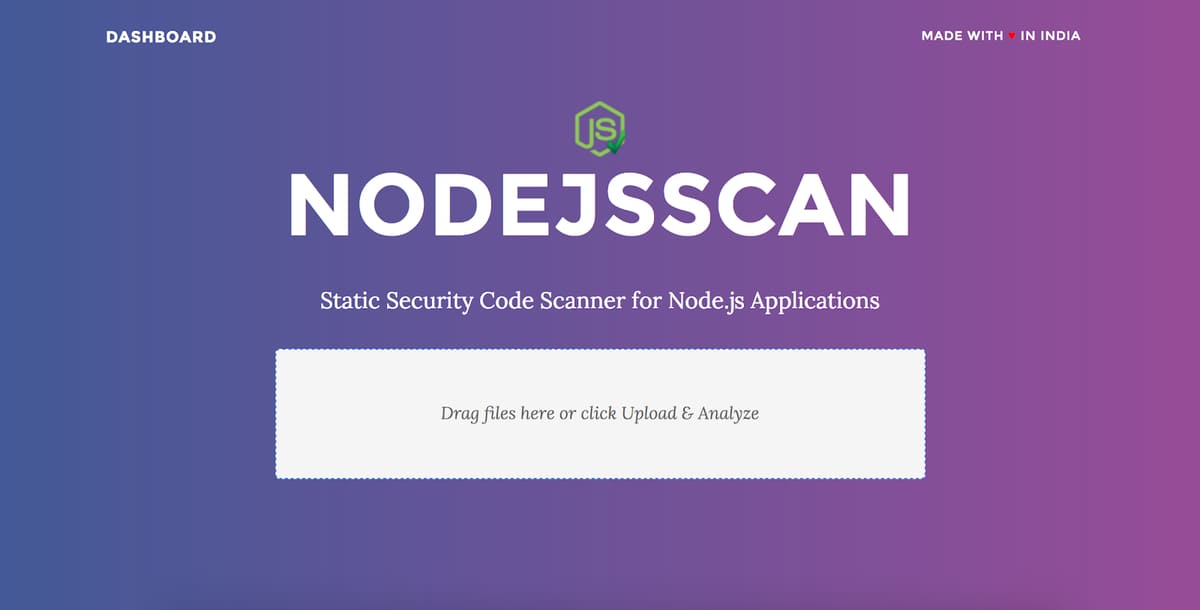
Nodejsscan
Nodejsscan has command line interface to easily integrate with Devsecops CI/CD Pipelines and produce results in JSON.
A configuration file is available for each language that can be modified for searching. Overview of files, as well as the entire code facility, can be displayed through statistics and circular charts. The program may detect cushion and error spill in Java code that may contain Owasp security risk.
Sonarqube
Considered one of the best automatic code evaluation tools available on the market. Sonarqube has thousands of static code analysis rules. Sonarqube also supports 27 modern and outdated languages (outdated, but there are still very valuable valuable) so that Sonarqube can cover your entire project and its development.
Dynamic Application Security Testing – Also known as “Black Box Testing”. This technique does not find a vulnerability in the source like Sast, but is to find a hole while the application is running. It does this using the Injection techniques on the application. Dast can identify common security holes, such as SQL Injection and XSS. Dast also pays attention to issues such as running time cannot be determined by static analysis, authentication issues and server configuration, as well as holes displayed only when users have logged in.
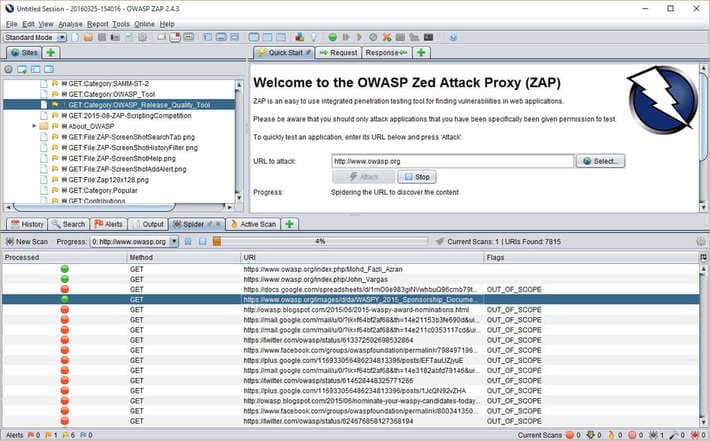
Owasp Zap
Owasp Zap is an open, free DAST tool that is fully equipped with features, including automatic sweeping holes and tools to support the manual web-app-app. Zap has a large list of holes that it can exploit or determine.
Interactive application Security testing – Also known as “Gray Box Testing”, is the combined technology of the elements of both Sast and Dast. It is often deployed as an agent during the testing period (for example, the device for Java virtual machine[JVM] or .NET CLR) to observe the activity or attacks and identify holes.
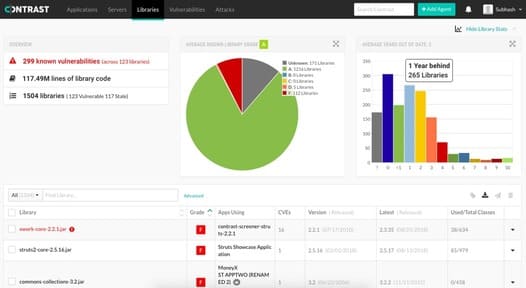
Contrast is the first product for developers who have the ability to learn more deeply into the gaps without knowing the context of the application time of the application such as controllers, application logic, data layer, viewing mode, user library, components of the source code and the server of the application.
Runtime Application Self Protection – Configured on a server and will boot when the application runs. It is designed to detect attacks on an application in real time. When the application starts to run, Rasp can protect the application from input or toxic behaviors by analyzing both the behavior of the application and the context of that behavior. By using the application to constantly monitor its own behavior, attacks can be identified and minimized immediately without human intervention.
Sqreen
SQreen Runtime Application Self-Protection identifies public attacks in the product by taking full advantage of the context of the requirements.
SQreen includes all top 10 leading security holes of Owasp such as SQL Injection, XSS and SSRF. What makes SQreen so strong is the ability to take advantage of the execution logic of the requirements to block attacks with a much lower level of failure than other existing solutions. SQreen may also adapt to the specific application of the application, so you do not need to be deployed and configured while your application is still simple and fast.
Denpendency Scanning Help you automatically find security holes while you are developing and checking your application, for example when your application is using the vulnerable Open Source.
Snyk
SYNK is the first developer’s organization with open source solutions that are best maintained for developers. Symn provides effective business solutions available to larger organizations.
Snyk has a series of excellent features that help turn security into part of the development process such as the ability to detect holes from within your IDE and scan the Navtive Git to check the projects in your storage. Snyk also provides a security port to prevent new holes from going through the construction process and product environment to check your running environment to ensure no existing holes.
Whitesource Bolt for github
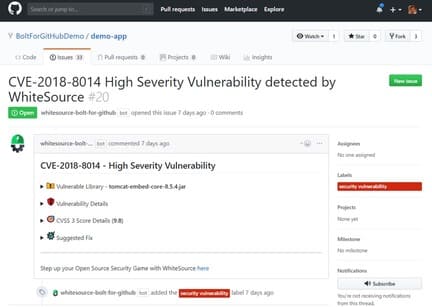
Whitesource is like Snyk, there are also some great free tools for developers as well as corporate solutions for large organizations. Whitesource Bolt for Github is a free application, it constantly scans your repos, detect holes of components in the source code and provide errors. It supports its own warehouse and public warehouse.
More than 200 programming languages are supported and monitored continuously from many open source coded databases as NVD.
Secrets such as key API, database information and security certificates are the gems of organizations because it can provide access to sensitive systems.Secrets detection can scan source codes, logs and other files to continue looking for other secrets. This is a special service because most of the secrets are always high Entropy chains (the chains are designed to appear randomly), but most of high entropy strings are not secrets, so they are difficult to be detected. It requires advanced classification algorithms to detect secrets with high levels and high recalling levels.
Secrets detection is often confused with Sast because both of them scan the source. But unlike Sast, only related to the current version of the application, Secrets Detection involves all versions of the project. Version control systems like Git, will monitor and store all changes to a project. If the previous versions of the source codes contain hard -encrypted secrets, have been deleted in the final stage, the code evaluation and tools like Sast will miss these secrets, so it can be in Git warehouse and are infringed. This is why Secrets Detection is different from Sast.
Gitguardian
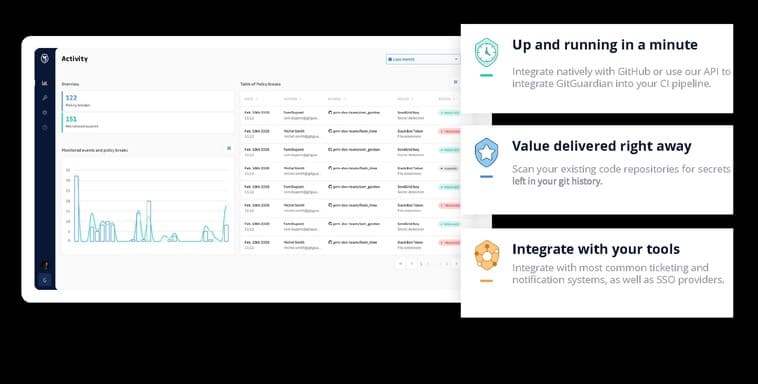
GitGuardian’s technology works by scanning developers’ storage to find evidence of sensitive data.
GitGuardian includes more than 300 different sensitive data from the Database connection key, SSL certificate, to username and password. These data are detected through a combination of algorithms, including sophisticated Pattern Matching techniques. GitGuardian can be integrated with your GitHub account and are configured for a few minutes, so developers can use GitGuardian API to detect data in any service, including in the folder, email application or Slack channel.
Summary
With so many solutions available, you may find it difficult to decide which tools to choose in the article. But remember, always consider the use of each tool in accordance with your current work process because even great tools can become useless if they are too difficult to use.
Each application is different and the tools mentioned above should be considered a minimum protection level, if you and your organization may not need more detailed solutions. Security is one of the most appreciated skills of developers, although security seems to be considered a difficult task, it is a valuable investment to understand and implement these systems in the entire life cycle of the application.