In this article, we will learn about the Browser In The Browser (BITB) phishing technique, which simulates a browser window in the browser to fake a legitimate domain.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
Introduce
For security professionals, the URL is often the most trusted part of the domain. But attacks like IDN Homograph and DNS Hijacking can reduce the trustworthiness of the URL, but not to the extent that it makes the URL untrustworthy.
All of this finally got me thinking, is it possible to make the “Check URL” advice less reliable? After a week of brainstorming, I decided that the answer was yes.

Pop-up login window
Quite often when we authenticate a website through Google, Microsoft, Apple, etc. we are presented with a pop-up asking us to authenticate. The image below shows the pop-up that appears when someone tries to sign in to Canva with their Google account.
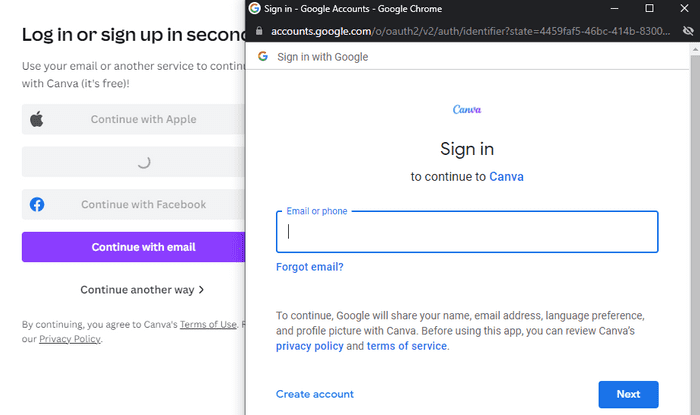
Window scaling
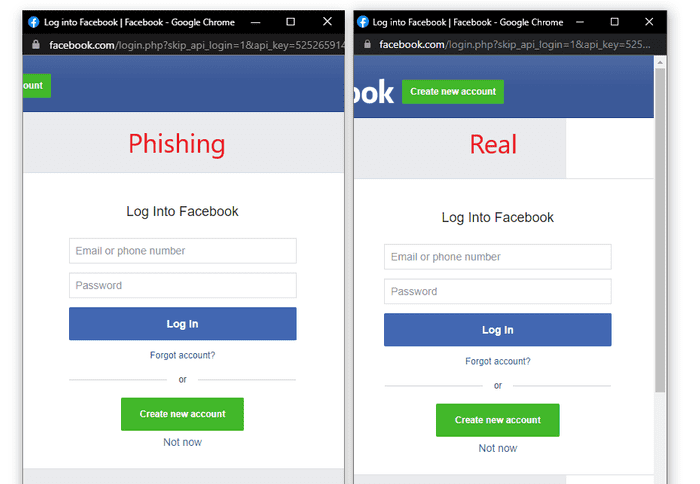
Creating a popup with basic HTML/CSS is pretty straightforward. Combine a window design with an iframe that points to a malicious server hosting a phishing page and is essentially indistinguishable. The image below shows the fake window compared to the real one. Few people will notice the slight difference between these two windows.
JavaScript can easily be used to make a window appear on a link or button click, on page load, etc. And of course you can make the window appear visually appealing through the animations available in libraries like JQuery.
Demo

Customize URL on hover
Hovering over a URL to determine if it’s valid, isn’t very efficient when JavaScript is allowed. HTML with a link usually looks like this:
<a href="https://gmail.com">Google</a>If the onclick event returning false is added, then hovering over the link will continue to show the web page in the href attribute but when the link is clicked the href attribute is ignored. We can use this knowledge to make the popup look more realistic.
<a href="https://gmail.com" onclick="return launchWindow();">Google</a>
function launchWindow(){
// Bật cửa sổ giả
return false; // Đảm bảo thuộc tính href bị bỏ qua
}Samples are available
The author has created 2 templates for the following operating systems and browsers:
- Windows – Chrome (Light & Dark Mode)
- Mac OSX – Chrome (Light & Dark Mode)
These templates are available on Github here.
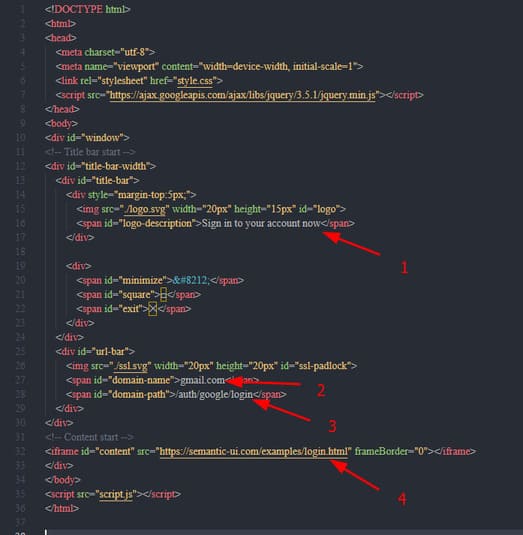
When downloading the source code, you open the index.html file and change some places as follows:
- XX-TITLE-XX – Display title for the page (e.g. Sign in to your account now)
- XX-DOMAIN-NAME-XX – The domain name you are spoofing. (eg: gmail.com)
- XX-DOMAIN-PATH-XX – Domain name path (e.g. /auth/google/login)
- XX-PHISHING-LINK-XX – Phishing link will be embedded in the iFrame (example: https://example.com)
And this is the result. Also, if you’re using a Windows template, you should update the logo.svg file, the icon of the website you’re faking. The default logo is Microsoft’s.
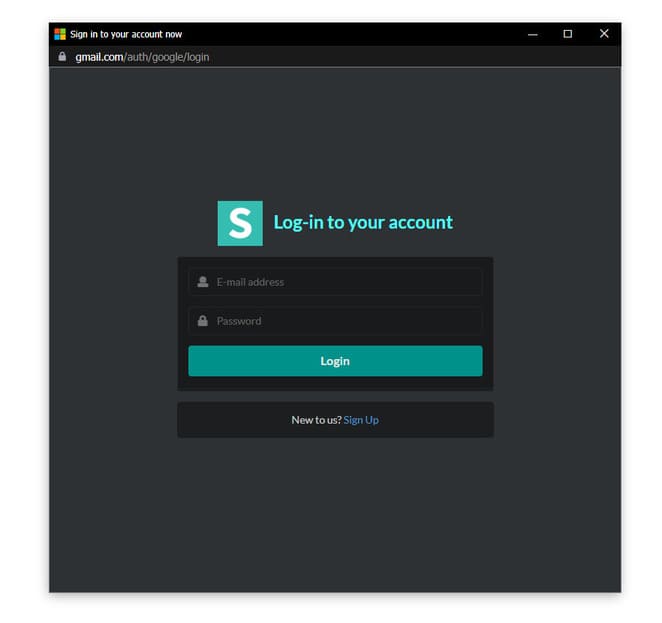
The Windows-DarkMode-Delay folder uses jQuery’s fadeIn() function to add a small delay to the popup when it appears.
Conclusion
With this technique we can now improve our cheat games. The target user still needs to visit your website for the popup to be displayed. But once on the website owned by the attacker, users will feel comfortable when they enter their credentials because the URL looks very trustworthy.