In this article, we will learn about network protocols and services. At the heart of the Internet, every ethical hacker must understand common network protocols to be able to understand the architecture of computers.
| Join the channel Telegram belong to AnonyViet 👉 Link 👈 |
One of the most important skills to become an ethical hacker is the skill of networking. A computer cannot be without a connection, so hackers are also important. It is important to have network knowledge to get used to the new architecture.
Knowledge of network protocols and services
SMTP
SMTP, short for (simple message transfer protocol), is an email protocol used to send email messages. Defined as RFC 5321, it is the heart of the mail connection. SMTP is much older than HTTP, but it is still used by ordinary users. To support email services, a pair of protocols is required, including SMTP and POP/IMAP.
SMTP uses three basic functions:
- It verifies who is sending emails through the SMTP server.
- It also sends out emails.
- When a message cannot be delivered to the recipient, the message will be sent back to the sender.
POP/IMAP
POP, or “Post Office Protocol” and IMAP, “Internet Message Access Protocol”. These protocols are very important, to send a message to the recipient, it uses IMAP which is responsible for transferring emails between the server and the client.
The main difference between POP and IMAP, POP is a simple approach to downloading messages in the inbox. Where IMAP will sync the current inbox, with new messages on the server, downloading anything new.
How does SMTP work?
Once an SMTP server is set up, email applications can connect and communicate with it. When the user presses “send” on an email, the email client opens an SMTP connection to the server so it can send. The role of the SMTP server in this service, is to act as sorting office, email (mail) is picked up and sent to this server, and then delivers it to the recipient.
SMTP operates in an application layer protocol (Application).
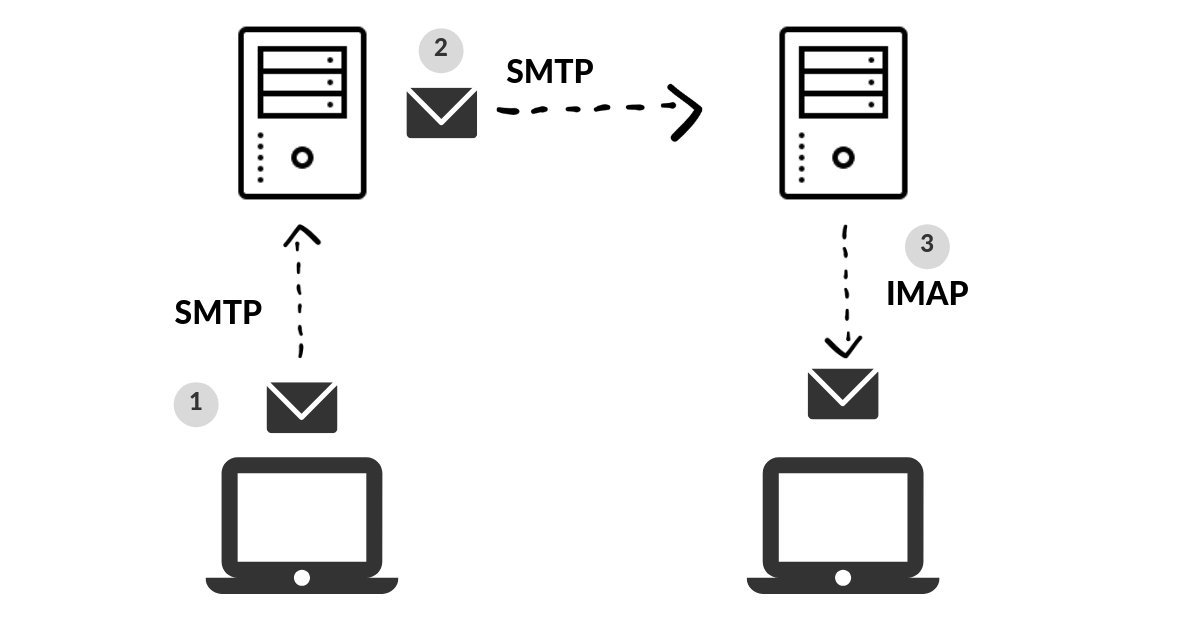
SMB
SMB, abbreviation for (server message block protocol). This protocol is a client-server protocol used to share and transfer data as well as access files.
The server can be accessed to view files, APIs, printers, and other resources.
This protocol is also known as request-response protocol which means it transmits data/messages between the client and the server.
SMB works in class Application or class Presentation.
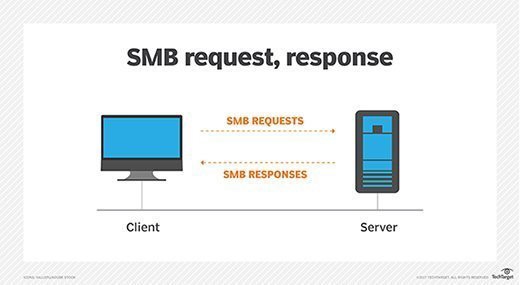
Once you have established a connection with the SMB protocol, you can view, transfer, and get resources from that server.
It also asks for login information, if the user has set a password on it.
The birth of SMB
Since the introduction of Windows 95 Operating Systems in early 1995, they have included support for the client and server SMB protocol known as “SAMBA”. It runs on UNIX systems.
SMB works in class Application or class Presentation.
TELNET
Telnet, short for (teletype network protocol) insecure version of SSH, telnet is a protocol that allows you to make a connection to a server and execute commands, which is the telnet host. When you establish a connection to Telnet, the client then becomes a virtual terminal – allowing you to interact with the remote server.
Telnet is replaced
Telnet is rarely used by companies, for security reasons. Most companies have been using SSH (secure shell host) because it shows up when you enter your login information. It has now been replaced by SSH.
How does Telnet work?
Connecting to a Telnet server is easy. “Telnet [ip] [port]” is enough to be able to connect to the Telnet server.
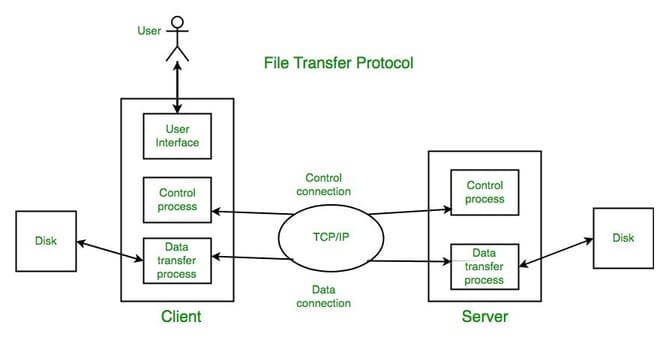
FTP
FTP, short for (file transfer protocol), it allows you to transfer files to this service remotely. It uses a client-server model.
How does FTP work?
FTP works in two ways:
- Command channel
- Data channel.
Command channel → Command channel is used to transmit commands as well as respond to those commands
Data channel → data channel is used to transmit data.
Security researchers always recommend not using port 21 (FTP) for security reasons.
Once the service is open, you can create a connection between the client and the server.
Active/Passive
FTP servers can operate either actively or passively.
- Proactive FTP server, connecting to random port numbers for incoming connections.
- Passive FTP server, opens a connection to a specific port and IP address for passive listening and clients connecting to it.
DNS
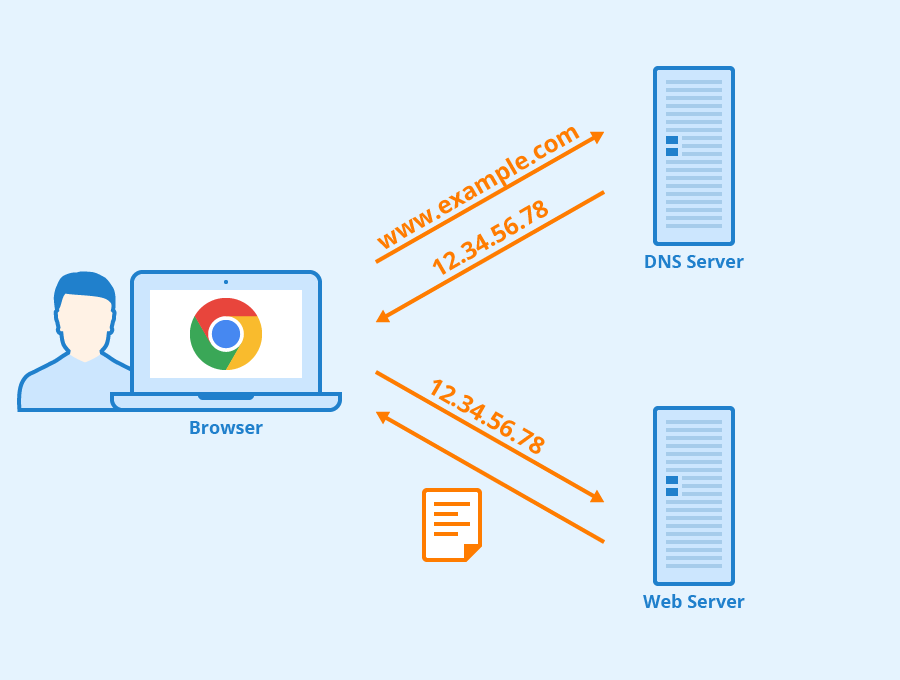
DNS, short for (domain name system). This service provides us with a simple way to communicate with devices on the internet without having to remember complicated numbers and values.
For example: https://www.google.com corresponds to “172.217.169.174”
Subdomain
A subdomain is an additional part of the main domain. Subdomains are created to organize and manage different sections of your website, for example:
For example:
admin.example.com → subdomain,
example.com → main domain
DNS is an application layer protocol.
SSH
Secure Shell (SSH) is a network security protocol that uses encryption and authentication mechanisms to implement services such as secure access and file transfer. The initial version, SSH1 focused on providing a secure remote login facility to replace TELNET and other remote login programs that were not secure. SSH also provides more general client-server capabilities and can be used for such network functions.
It is much more secure than TELNET, as it uses encryption and authentication to gain access to the server.
TLS
Server authentication occurs at the transport layer, based on the server possessing the public/private key pair
Transport Layer Secure
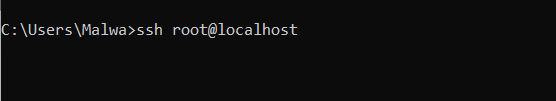
How does SSH work?
SSH is easy to use:
ssh [user]@ip-addr/localhost
SSH is an application layer protocol.
ARP
ARP, abbreviation for (address resolution protocol). This protocol is responsible for allowing devices to identify themselves on the network. This is one of the most important protocols in the network layer.
How ARP works
ARP has an important ledger in the network to store information, called a “cache”.
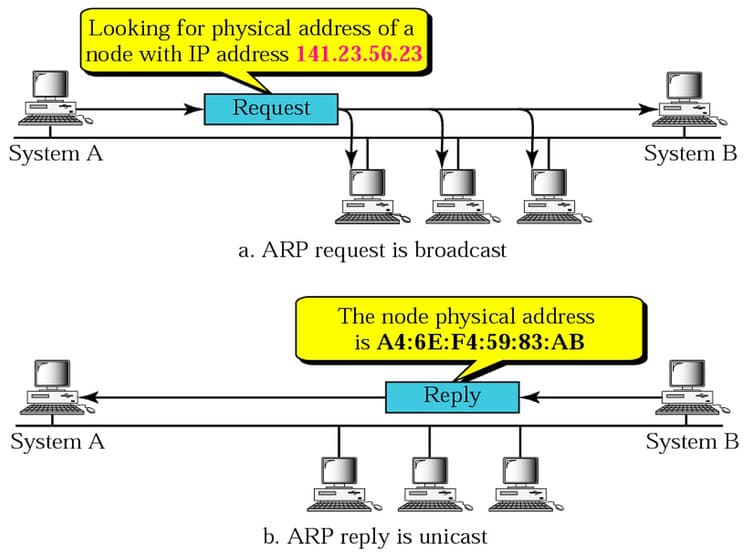
It works with MAC and IP addresses. ARP sends two types of messages.
- ARP requests
- ARP replies
ARP requests
When an ARP request is sent, a message is transmitted to every device found by the device on the network. This is nothing more than broadcasting a packet over the network to confirm whether we found the destination MAC address or not.
ARP replies
An ARP response is returned to the originating device to confirm this. MAC address feedback supports data communication.
ARP is in layer 2 protocol.
DHCP
DHCP, short for (Dynamic Host Configuration Protocol) helps a device want to connect to the network. if it has not been manually assigned an IP.
DHCP is based on the client-server model and is based on discovery, offer, request, and ACK.
DHCP sends a request called (DHCP discover) to see if there is a DHCP server on the network. When a DHCP client starts, it automatically sends a special DHCP discover message using the broadcast address. This DHCP discover message asks, “are there any DHCP servers out there”?
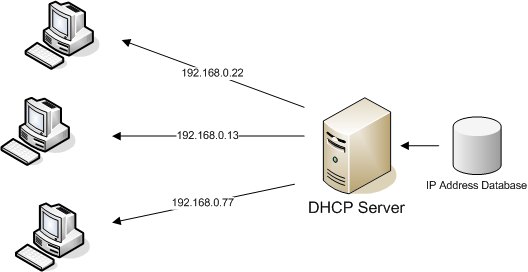
DHCP is an application layer protocol
MAC
MAC, short for (media access control). A MAC address is a unique identifier assigned to a piece of networking hardware by the manufacturer.
MAC address consists of six sets of two characters such as 00:12:ED:4B:16:5E. Do you want to see your NIC? If you are using a windows operating system, enter “ipconfig \ all” from the command prompt to display the actual address.
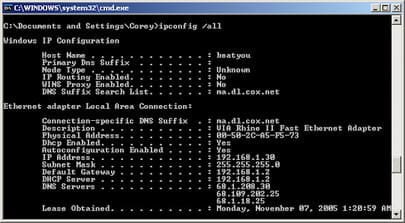
MAC addresses are at layer 2 (data link).
ICMP
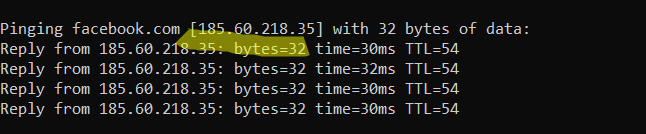
ICMP, short for (Internet Control Message Protocol) is one of the most important fundamentals in networking, because no ICMP means no response and that means no connection. Most of the time when you type “ping google.com” you will see TTL (time to live) which means ICMP packets travel as measured by ping, say your home network or the website you want to visit. access.
The easiest way to see ICMP on a network is to use ping and traceroute, but traceroute will also be used to analyze data flowing from its source to its destination address.
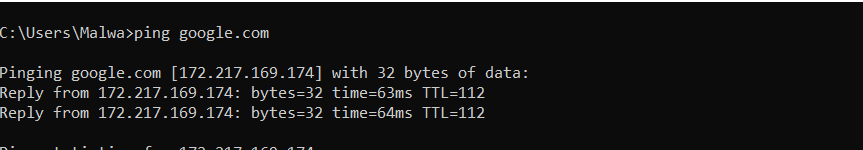
As shown in the image above, ttl is 112.
ICMP is shown as a layer 3 protocol.
NAT
NAT, short for (network address translation), originally used to solve the shortage of IPv4 addresses, is now used to mask public IPv4 addresses. To access the Internet, a public IP address is needed, but we can use a private IP address in our private network. The idea of NAT is to allow multiple devices to access the Internet through a single public address.
With NAT, a network can support more than 500 servers with private addresses, and a NAT router can switch these machines to the public address range when clients need to access the internet.
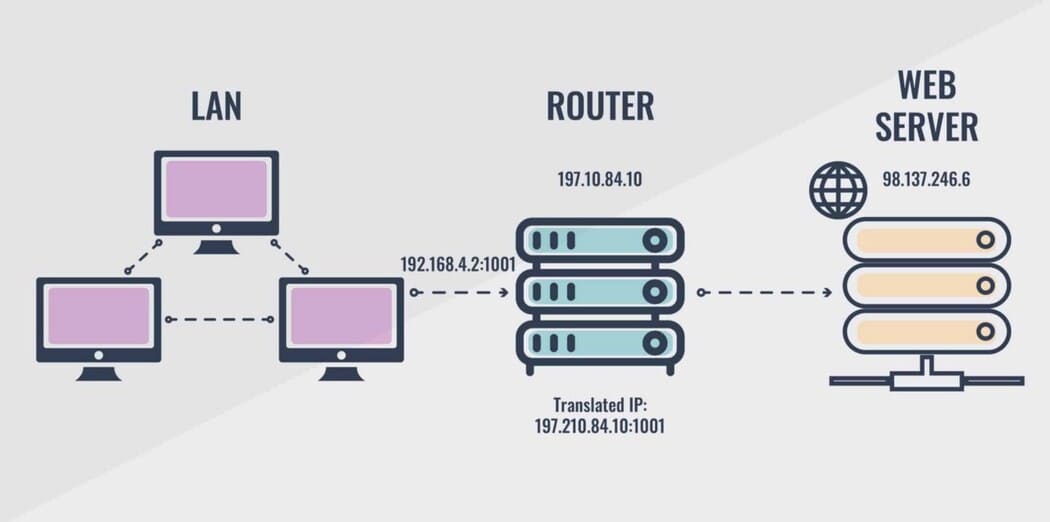
NAT is located at layer 3.
IP
IP, short for (Internet Protocol). Its main job is just to send messages between devices, and like any mailing service, it can’t do its job well if it doesn’t know where the recipient is. such as sending mail, streaming video, or connecting to a website.
For example:
Public IP -> 172.168.16.44
private IP -> 192.168.23.2
IP is in the network layer.