PowerMemory is a powerful script that allows users to extract and inspect user credentials contained in files and memory. This script is developed by Pierre-Alexandre Braeken and it helps us to get Windows Login Password using Powershell and CDB (Windows Debuggers).
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
Features of PowerMemory
According to the author, this tool works on versions of the Windows operating system, i.e. Windows 2003 to 2012 and even Windows 10 can be used.
PowerMomory has been successfully tested on versions 2003, 2008r2, 2012, 2012r2 and Windows 7 32/64 bit, Windows 8 and Windows 10 Home.
This tool is written on PowerShell, so it is difficult to be detected by Antivirus, the operation methods are similar to Mimikatzwhich displays the Windows Password in Plain Text.
Main feature:
- Completely based on PowerShell
- Works on a local, remote or from a locally collected dump file
- Do not use file system .dll to verify credentials address in memory but with Microsoft Debugger
- Use PowerShell (AES, TripleDES, DES-X) to decrypt the password.
- Destroy the undocumented Microsfot DES-X
- Works even if you are using a different operating system than the victim
- Leaves no trace in memory
How to use PowerMemory
Step 1: Download PowerMemory about
Step 2: Unzip the downloaded file
Step 3: Open PowerShell with admin rights
Step 4: To set up the environment, enter the command: Set-ExecutionPolicy Unrestricted -force
Step 5: Right-click the PowerMemory.ps1 file and select run with PowerShell
Step 6: Next select 1, this option will retrieve the password from memory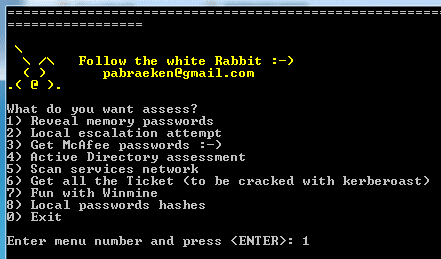
Step 7: The tool will ask you to grant Admin rights to PowerShell, just choose yes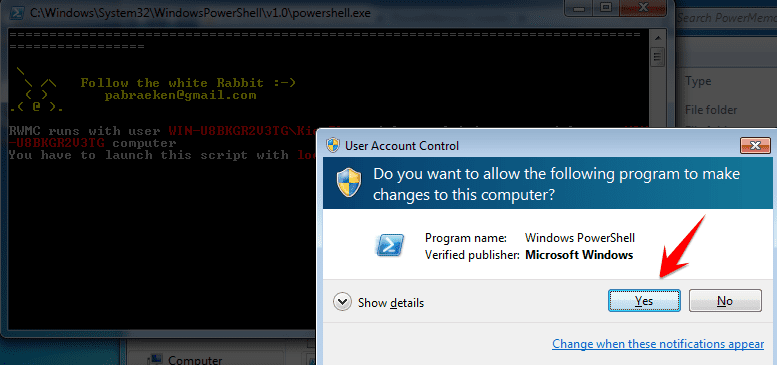
Step 8: Next, you choose 1 to activate cmdlets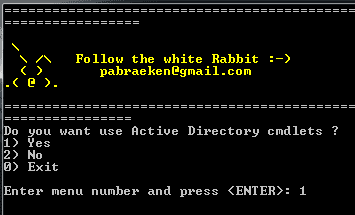
Step 9: Choose 1 to get the password on the victim machine
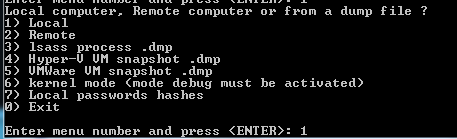
Step 10: I just want to get the password so I will are not select exfiltrate.
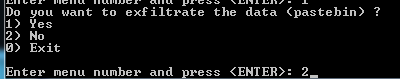
Step 11: Choose 1 to delete traces in the log, avoid leaving traces.
And here are our results
Here This method is completely new. It proves that one can easily hack login credentials or any other information from Windows RAM without using type programming language OLD. Also, with this method, we can modify user land and user kernel without being detected by new antivirus technologies.








![[CẬP NHẬT] 150+ Latest HOT TREND special character names 2026 [CẬP NHẬT] 150+ Latest HOT TREND special character names 2026](https://anonyviet.com/wp-content/uploads/2025/10/word-image-95531-3.png)