What is Nuclei?
Nuclei is an open source toolkit used to scan Website security holes, also known as Bug finder. Some Bug Hunters are using this tool to receive bounties from websites with weak security. A special feature that Nuclei is favored by many Hackers is that it has a large user community and error code templates are always updated regularly, so when a vulnerability has just been released, Nuclei already has a template to scan.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
Another highlight is that Nuclei is completely free and you can customize how to scan Website as well as create templates to scan Website bugs to your liking.
Nuclei can scan various protocols, including DNS, HTTP, TCP and many more. All kinds of security checks can be done using kernel templates.
How to install Nuclei
It is recommended to turn off anti-virus programs on Windows when performing an Upgrade Kali Linux to avoid blocking installation packages. To install Nuclei, execute the following commands on Kali Linux:
sudo su
Enter password user
apt-get update -y
apt-get upgrade -y
Because nuclei is written in Goland language, so we need to install Goland on Kali Linux, execute the following commands:
apt install gccgo-go -yapt install golang-go -y
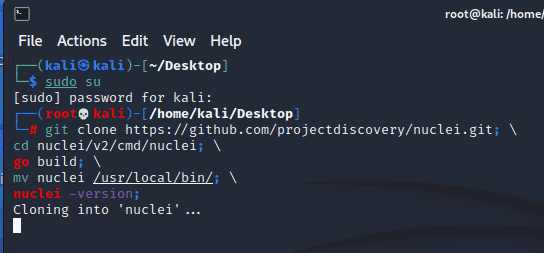
Install Nuclei to scan Website security holes
git clone https://github.com/projectdiscovery/nuclei.git; \cd nuclei/v2/cmd/nuclei; \go build; \mv nuclei /usr/local/bin/; \nuclei -version;
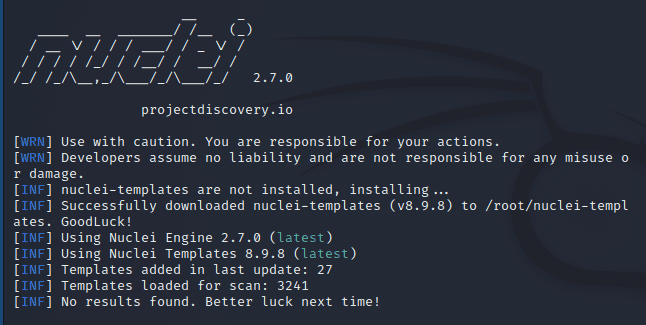
After the installation is complete, type the command nuclei -h to start
The case of reported nuclei outdated, is because you downloaded the old version. Let’s execute the update template command again.
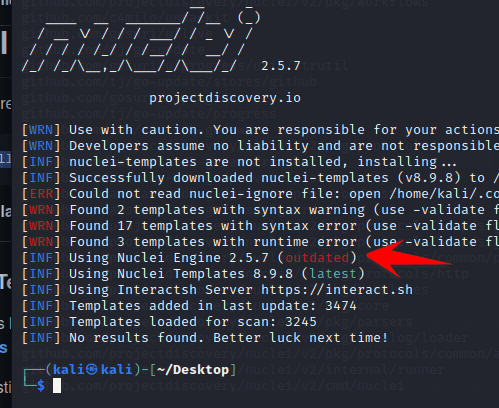 Use the command:
Use the command:go install -v github.com/projectdiscovery/nuclei/v2/cmd/nuclei@latest
sudo nuclei -update
If successful, you will see the following interface:
If you want to use nuclei to find Bug Website on Windows, download the version Windows kernel back to use.
How to use Nuclei to scan Website vulnerabilities
To proceed to find Bug Website we execute the following command:
nuclei -u địa-chỉ-website
Eg: nuclei -u https://domain.com
In case some Websites will have a firewall (WAF) and block scanning processes, you can reduce the frequency of sending requests to the server by rate-limit. Let’s use the parameter: --rate-limit.
Eg: nuclei -u https://domain.com -rate-limit 1 //ie send 1 second send 1 request
To bypass WAF, you can change the packet header to avoid blocking, with the parameter -h
Eg: nuclei -u https://domain.com -rate-limit 1 -header 'User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64)'
In case you want to scan many Web pages, create a file named url.txt, fill in 1 Web page per line, then use the syntax -list url.txt
You can see some more examples when scanning Website vulnerabilities at nuclei’s home page.