Hippie osint Toolkit A useful tool to help you explore and collect information from many different sources on the internet. With an easy -to -use interface and quick search support, this Toolkit gives users valuable data, especially useful in Capture The Flag (CTF) competitions or online surveys. In this article, let Anonyviet discover how to use Hippie Osint Toolkit and its outstanding features.
| Join the channel Telegram belong to Anonyviet 👉 Link 👈 |
What is Osint?
Osint or open information, is the collection of data from public sources for use in information collection. Unlike traditional intelligence methods, Osint is based on the legal information from public sources, such as domain name registration information, public records, social networks, even cloud storage data. This information is extremely useful for security analysts, private investigators and anyone who involved in hunting online threats.
See also: Discover FBI Tools: Github warehouse contains many useful Osint tools
In the world of online security and online surveys, Osint (open information) has become an indispensable tool. With the development of public platforms and databases, experts can collect important information without complex software installation.
Hippie Osint Toolkit is developed to provide you with easy -to -use Osint tools, especially useful for the Capture The Flag (CTF) challenges and investigation.
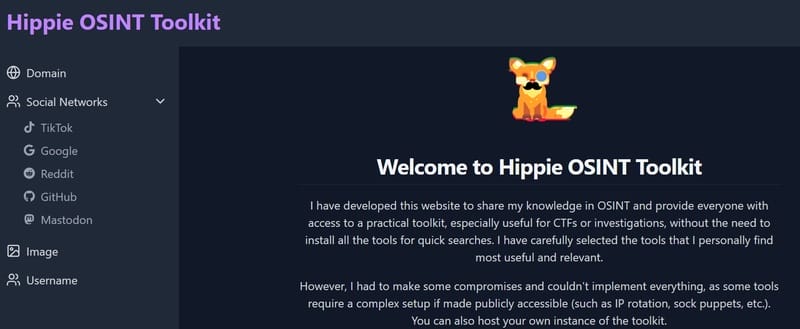
You can visit Hippie Osint Toolkit HERE
1. Domain analysis (domain)
One of the important areas that Osint is applied is the domain name survey. Whether you are studying the owner of a website or exploring related websites, this tool can disclose important information that is not always easy to find via search on the Internet.
Data can be found:
- Whois information: The Database of WHOIS stores domain name registration information, including the owner’s contact information, the date of creation and the expiry of the domain name and the registered house. This is very important to determine the legality of the domain name and search for the original owner.
- Subdomains (sub -name): Tools like CRT.SH help you find subdomains associated with a domain name, thereby detecting more relevant websites or services.
- Domain server (Name servers): Details of the domain name server help you understand the network infrastructure behind a website and can help detect related domain names or services.
Some of the main tools to investigate domain names:
Look up Whois: Websites like whois.domaintools.com Provide comprehensive search services. They can provide domain historical information, including old communications, which can be revealed more about an individual or organization.
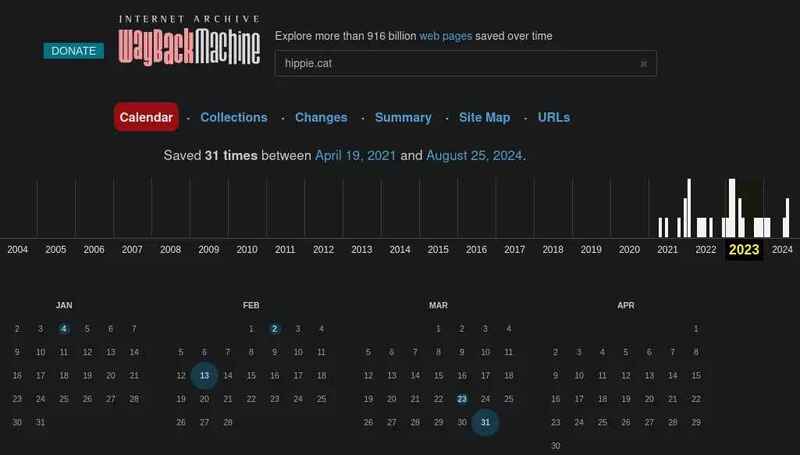
Wayback Machine: Wayback Machine https://web.archive.org is a tool used to monitor the change of websites over time. If you are investigating a change domain name, this tool can display the old versions of the site, helping you detect deleted or hidden information.
Cloud archives: Cloud storage boxes are exposed (such as AWS S3, Azure and Google Cloud) sometimes can contain sensitive information, including private documents and images. Tools like Osint.sh Buckets and Grayhatwarfare can help you find these revealed cloud storage boxes.
Track code: Tools like osint.sh analytics and osint.sh Adsense help you identify the general Google Analytics or AdSense IDs between domain names, indicating the owner or the relationship between them.
Search back: When you find a tracking ID, you can use the tools to find other domain names to share that ID, helping to detect other websites that belong to the same organization.
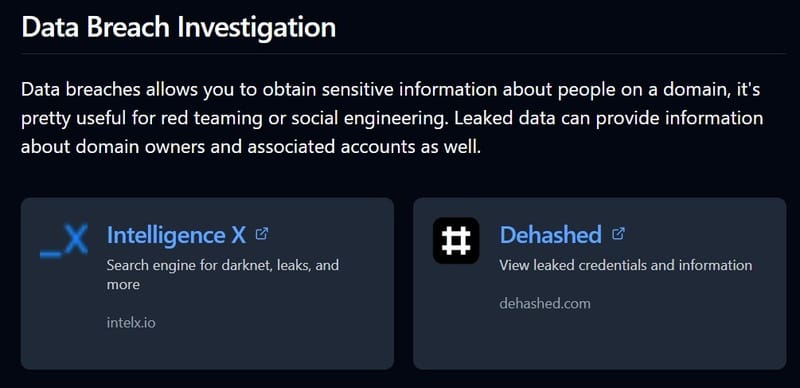
Leaked data: Information such as email addresses, user names and passwords from data violations can be found through tools such as Dehashed or Intelligence X. These data are very important in testing attacks and identifying cyber threats.
Not stopping there, Hippie Osint Toolkit has many other tools waiting for you to explore!
2. Investigate information on social networks
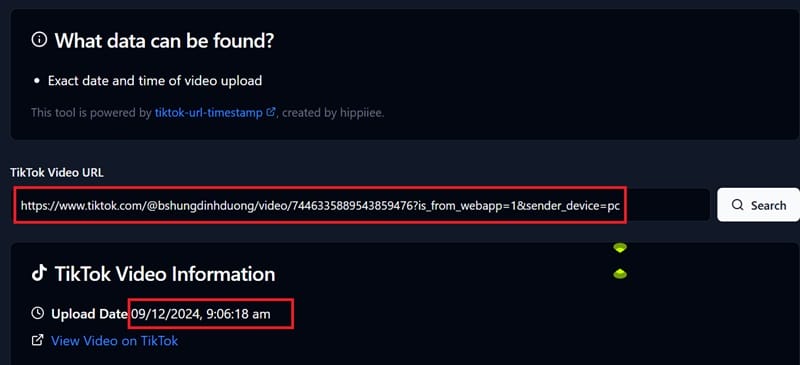
Tiktok
Only by any video URL link, you can determine the time to post that video
This tool can search for information related to Google account:
- Profile information: Including name, email and profile photo.
- Activity on Google Maps: Information such as photos, evaluation and statistics from user activities on Google Maps.
- Data from other Google services: Data from other Google services is linked to the account.
Github
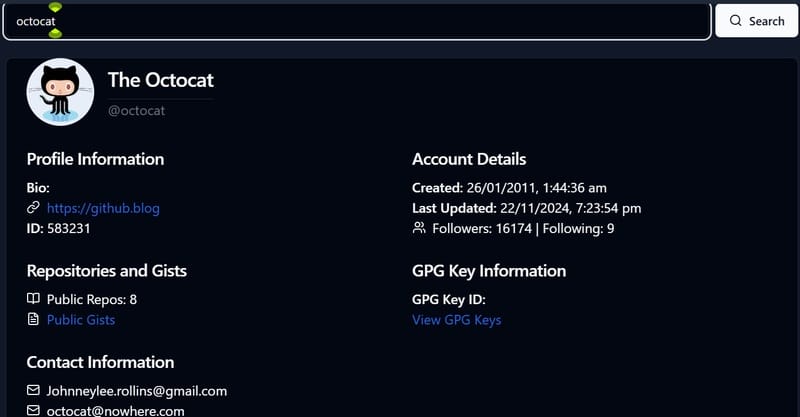
The data can be found on the GitHub account includes:
- Basic information of users: username, real name, biography, avatar.
- Account information: Date of account creation, last update date.
- Contact information: email address, blog/website link.
- Social statistics: The number of followers and followers.
- Information about archives: The number of public archives and Gists.
- Information about the GPG key: The public key is used to sign the commitment.
- Activities and history of contributions: Details of user contributions, such as commitment and pull request.
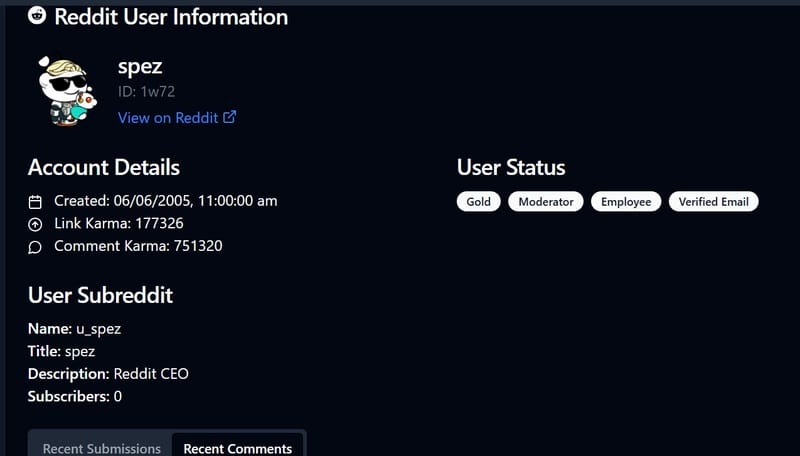
- Basic information of users: username, ID, date of account creation.
- Analysis of Karma: Including Karma (Link Karma) and Karma comment (Comment Karma).
- User status: may be a golden member, administrator, Reddit staff, have confirmed the email or not.
- Information about user’s personal subreddit: if any, including the Subreddit that the user manages or participates.
- Recent posts: title, content, score, comments of recent posts.
Mastodon
User information:
- Basic record details: username, display name, biography.
- Account statistics: The number of followers, followers and posts.
- Date of creating account and update the latest status.
- Account flag: Is the account BOT, locked, can be detected or not, etc.
- The records and associated accounts.
Information about instance:
- The name, description and miniature image of Instance.
- Registration status and approval request.
- Support languages.
- Administrators and contact emails of Instance.
3. Image analysis
The image is a valuable resource in Osint, and has many techniques to analyze the information hidden inside the image or image found online.
Search for reverse images: Tools like Google Lens, Tineye, and Yandex help you follow the origin of the image or search the same image online. These tools are especially useful to monitor the image spread or identify the origin of the image uploaded by the user.
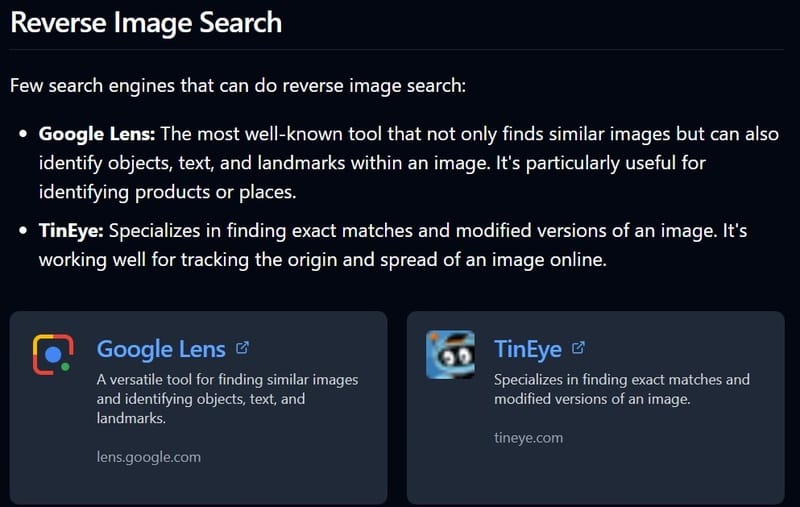
Image positioning: Tools like Overpass Turbo and Geospy.ai It is possible to analyze the image to infer the location where the image is taken based on geographical features.
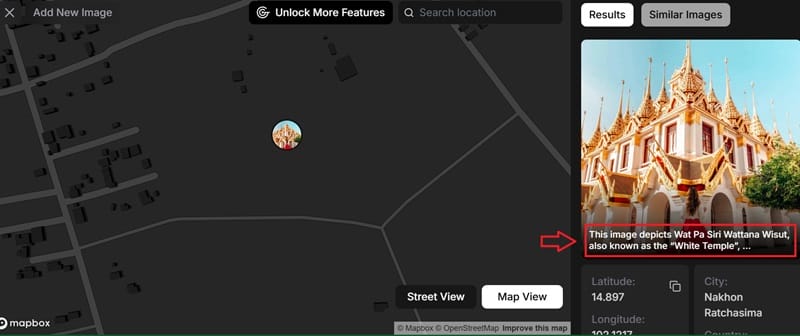
Extract Metadata: EXIF data in the image can provide information about shooting time, camera settings, and even GPS coordinates. Tools like EXIFTOOL and Forensically help you extract this Metadata to collect useful information.
Face recognition: Pimeyes As a tool to help identify and search for a person’s image on the Internet, even if they appear on different platforms and site.
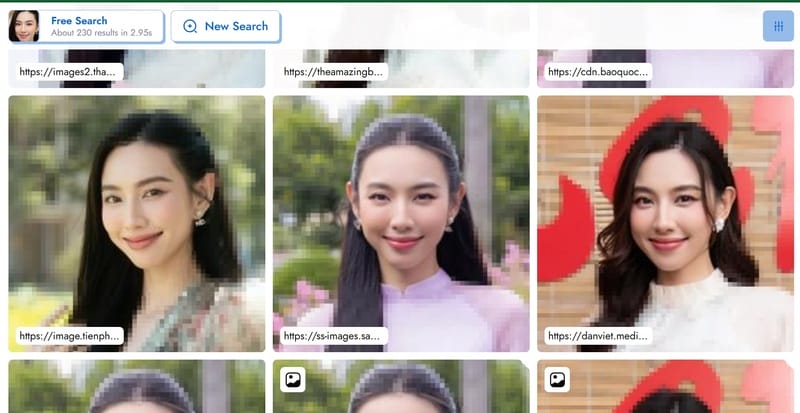
Delete details in the photo: Cleanup.pictures will help you quickly remove objects from images, useful when you want to focus on specific factors for further analysis.
4. Investigate user information
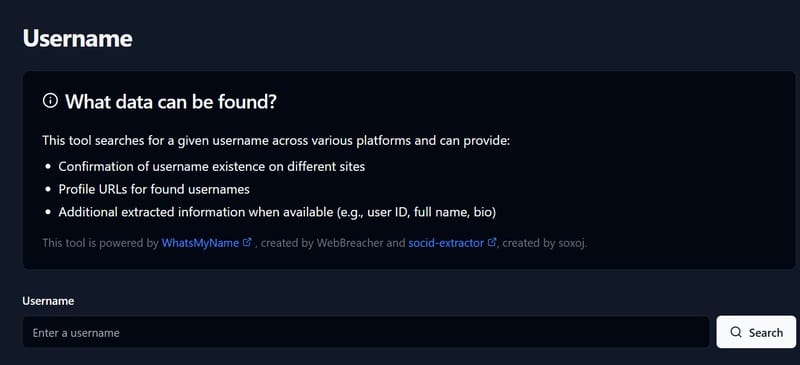
This tool can search for username on different platforms and provide the following information:
- Check whether the username exists on different platforms.
- Provide direct links to users’ records on websites or social networks.
- Additional information (if any), including information such as user ID, full name, biography, and other data related to users.
See also: Seekr: Collect & Manage data osint
Conclusion
Hippie osint Toolkit Has proved to be an effective tool to collect information from open sources. Thanks to the easy -to -use interface and useful toolkit, users can quickly search, analyze and discover important data. If you are looking for a quick and effective solution for investigation or CTF, Hippie Osint Toolkit is definitely the option not to be missed.











