Coming to the next part of the series “Basic hacking knowledge should know”. In this part 2, I will share some more hacking knowledge for everyone. Hope these knowledge will help you learn more good things.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
If you forgot some knowledge in the previous section, you can click Part 1 to read it again.
Basic knowledge of Trojan, worm, virus, logicbomb?
First of all, I want to briefly explain about these types. These are the same viruses that made history back in the day. You should find out if you don’t know yet! We will talk about them one by one to make it easier for you to imagine.
What are Trojans?
You can briefly understand this is a spy program that is installed on your computer to steal information. Then send everything back to its owner. Here, what it targets is stealing accounts, passwords or cookies, etc.
In general, it will give full control of the computer to its owner. They can gain access to control your computer or steal anything they want.
Talking about Viruses
A program that contains special code that is installed or spread from other computers to the victim’s computer. It is responsible for fulfilling the requirements of the code that its owner wrote. Often viruses will be used to destroy data and computers.
Worms are… ?
In short, a worm is a standalone program. It can replicate itself and spread throughout the network. Worms are also often used for the same purpose as viruses. It destroys data, destroys inside the network and more dangerously can bring down the entire network.
Finally, LogicBomb
A program that sends multiple packets of data at the same time to the same address. It will “fatigue” the system, block the transmission. Moreover, it is used as a tool to “terrorize” the enemy (bomb mail).

What is PGP?
” Pretty Good Privacy “also known as PGP for short. This is a tool that uses public key encryption to protect email data and records. PGP is a highly secure form of encryption that uses software for MS_DOS, VAX/VMS, Unix and for other forms
What are proxies?
In simple terms, a proxy is an Internet server that relays information and controls the security of Internet access, also known as Internet service clients. Proxy server is the installation station of the proxy. Proxy or proxy installation station has an IP address and a fixed access port.
You can understand is another computer that is responsible for processing data. It is like an information converter of the Internet signal. With the connection through 1 or more servers as above. Initially, the user’s computer sends the request signal through the proxy server. Here, that information will be processed and sent back to what you see every time you access the Internet.
Proxy allows users to access services on the Internet in a direct sense. With dual host homed, you need to login to the host before using a service on the Internet. Because proxies allow users to access Internet services from their personal systems. Therefore, it does not allow packets to go directly between the user system and the Internet. The path is either indirect through the dual homed host or through a combination of the Bastion host and the screening router.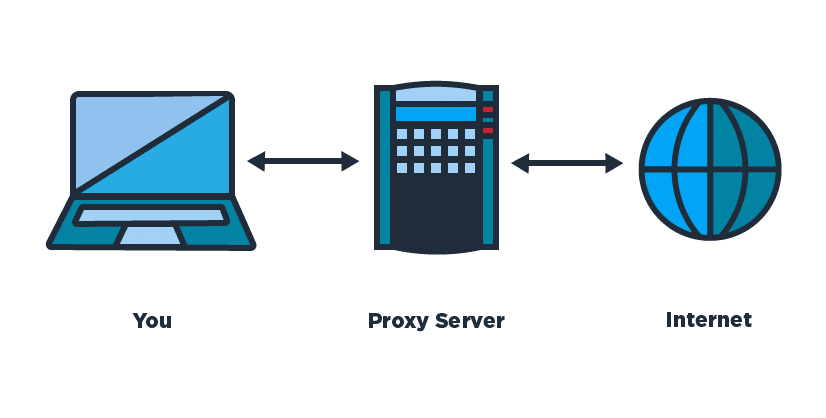
What is Unix?
Unix is a Windows-like operating system. It can run on many different computers including personal computers or service servers. It is a multitasking operating system and is written in the C programming language. And Unix is also the operating system that hackers often use.
What is Telnet?
Telnet is a program that allows us to connect to another machine through a port (also called a port). Every computer or server has ports, here are some common ones:
- Port 21: FTP
- Port 23: Telnet
Eg: You can call Telnet to connect to mail.virgin.net on port 25 .
How do I know I have Telnet to the Unix system?
I will tell you how a Unix system can greet you when you connect to it. When you call Unix, it will normally appear with the line : ” Log in: “, (but with that alone, this is not necessarily Unix except they appear before the word “log in”)
We are now at the prompt.” log in: “, you need to enter a valid account. A normal account has 8 or more properties, after you enter the account you will see a password, please try to enter Default Password Try the following table:
Account/Default Password
Root/ Root
Sys/Sys/System/Bin
Bin/Sys/Bin
Mountfsy/Mountfsys
NuucAnon
Anon/Anon
User/User
Games/Games
InstallInstall
DemoDemo
GuestGuest
What is a shell account?
A shell account allows you to use your home computer as a terminal with which you can type commands to another computer running Unix. “Shell” is the program that translates the characters you send and will be put into the execution of the Unix program’s command. With a correct shell account you can use a workstation far more powerful than you could ever imagine.
Here is the Bonus part
Leave ads to support AnonyViet!
Like Fanpage or follow website for quick updates of good articles.
AnonyViet-HanPhu