Since countries started implementing stayhome campaigns, Zoom software has become an ambassador for meeting friends and family or even participating in online classes. But we have a new type of attack called Zoom-bombing.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
However, with the increasing popularity of Zoom, Zoom-bombing attacks are being seen more and more.
Zoom-bombing is when someone gains unauthorized access to your meeting to harass meeting participants in various ways.
On March 31, the FBI issued a warning to Zoom users that they should secure their browsers from Zoom-bombing attacks.
“The FBI has received numerous reports of conferences being canceled because of pornographic images and threats,” the warning was published by the FBI.
This article will show you how to protect Zoom meetings from unauthorized users.
Privacy considerations when using Zoom
One of the most important things to remember is that the host (meeting host) can record the meeting, including video and audio, to their computer. Therefore, be careful not to say or reveal anything that you don’t want others to know.
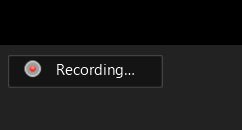
Meeting participants will know when the meeting is being recorded if the message “Recording….” is displayed in the upper left corner of the screen.
The second thing to remember is that users can download their chat logs before leaving the meeting. These logs contain messages that you can see, and they will not contain private chat messages from other users.
Finally, it was reported that Zoom did not have end-to-end (E2E) encryption between users.
This means that only communications between meeting participants and Zoom’s servers are encrypted, and meeting-related data sent via Zoom is not.
Theoretically, a Zoom employee could monitor the meeting’s data, but Zoom told The Intercept it has safeguards in place to prevent this from happening.
“Zoom has security measures in place to protect user privacy, including preventing anyone, including Zoom employees, from directly accessing any data users share during meetings, including the video, audio and text content of such persons. Most importantly, Zoom does not mine user data or sell any kind of user data to anyone.”
Years ago, I remember Mark saying the same thing. Hold on, if you’re using a free piece of software, congratulations on becoming a product of that software.
How to secure your meeting
Now that you know all the potential risks when using Zoom, before creating a meeting with friends or colleagues, you can refer to the ways below to secure your meeting.
Add a password for the meeting
When creating a new meeting, Zoom will automatically enable the “Require meeting password” feature and give you a random 6-digit password.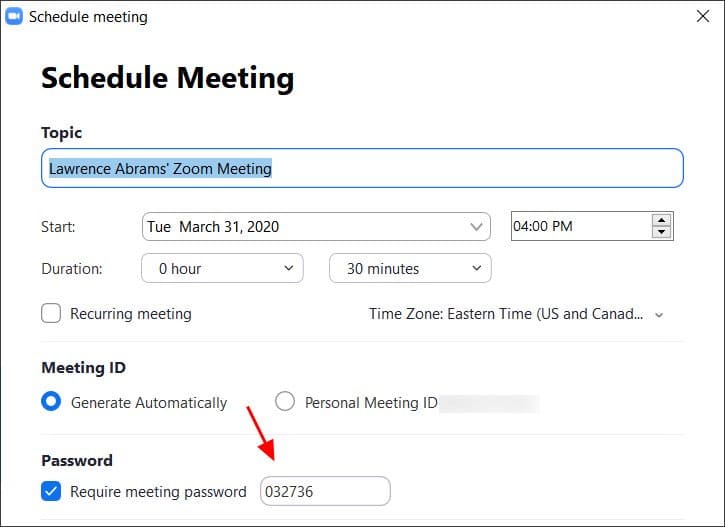 You should not uncheck this option because doing so will allow anyone to have access to the meeting without your consent.
You should not uncheck this option because doing so will allow anyone to have access to the meeting without your consent.
Use the lounge
Zoom allows the host to activate the lounge feature to prevent users from joining the meeting without the permission of the room owner.
This feature can be enabled while creating a meeting by opening the advanced settings (Advanced Options), ticking the “Enable waiting room” box, and then clicking “Save”.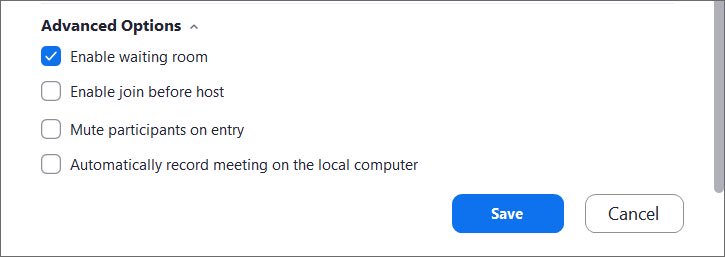
When this feature is enabled, anyone joining the meeting will be taken to the waiting room, where they will receive a message saying “Please wait, the meeting host will let you in soon”.
The host will then receive a notification when other people join the meeting and you can see who is waiting by clicking the “Manage Participants” button on the toolbar.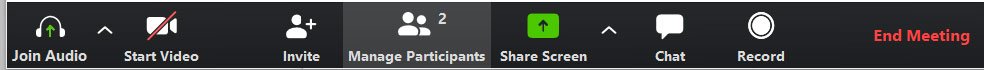
The next thing you need to do is allow them to join the meeting by clicking “Admit”.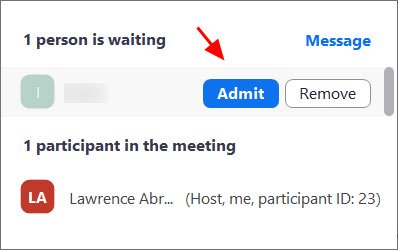
Keep Zoom app up to date
If you are prompted to update the Zoom app, install the update as soon as possible.
Zoom’s latest updates have enabled the password feature by default and added meeting ID scanning to protect users.
With Zoom growing in popularity, hackers will focus on Zoom to find vulnerabilities. By installing the latest updates, you will be protected from any discovered vulnerabilities.
Do not share the meeting ID
Each user of Zoom is assigned a personal ID (PMI) that is permanently linked to their account.
If you give your PMI to someone else, they can see what meeting you’re hosting and potentially join if you don’t set a password for the meeting.
Instead of sharing your PMI, create new meetings and share the meeting link with whom you want.
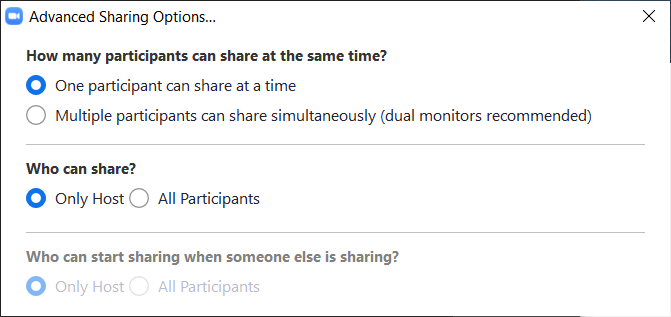
Turn off the Share Screen feature
To prevent unwanted attacks, you should prevent meeting participants from sharing their screens.
If you are a host, you can do this by clicking the arrow button next to “Share Screen” on the toolbar and then clicking “Advanced Sharing Options”.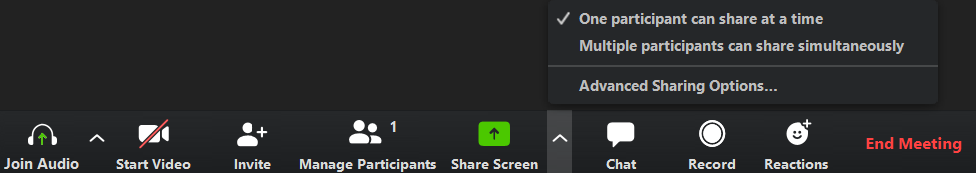
In the next window, select “Only Host” in the “Who can share?” section. Lock the meeting when full
Lock the meeting when full
If everyone has fully participated in your meeting, you should lock the meeting so that no one can join again.
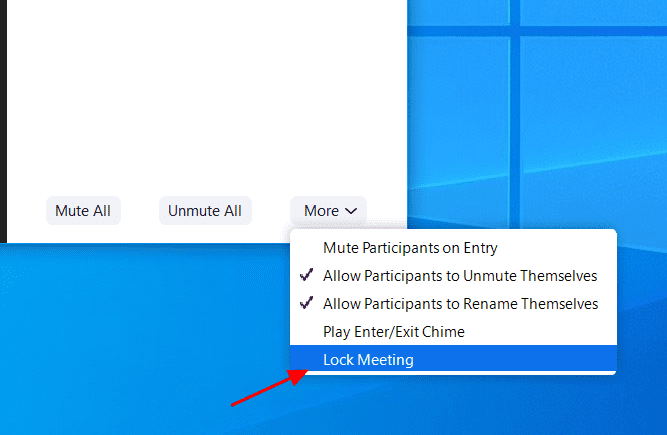
To do this, click on “Manage Participants” on the toolbar and select “More” at the bottom of the window. Then select “Lock Meetings”.
Don’t post photos of your meeting
If you take a picture of your meeting, anyone can see the meeting ID. This will allow others to try accessing your meeting.
For example, British Prime Minister Boris Johnson has tweets a photo with the text “first even digital Cabinet” and of course an ID in the photo.
This morning I chaired the first ever digital Cabinet.
Our message to the public is: stay at home, protect the NHS, save lives. #StayHomeSaveLives pic.twitter.com/pgeRc3FHIp
— Boris Johnson #StayHomeSaveLives (@BorisJohnson) March 31, 2020
An attacker can take advantage of this to try to gain unauthorized access to the meeting by joining via ID.
Do not post the link to join the meeting
When creating meetings, you shouldn’t post your meeting join link publicly.
Doing so will cause search engines like Google to index the links and allow anyone to access these links.
By default, the password is displayed in the link, so if someone has your link, they will be able to Zoom-bomb into the meeting.
Beware of Malware called Zoom
Since the outbreak of the coronavirus, the world has recorded a rapid increase in the number of malware, cheat and other pandemic-related attacks.
Malware and adware created to fake Zoom client.
For your safety, you should only download the Zoom app on the site Zoom.us.
You can see more how to install and use Zoom here.


 Lock the meeting when full
Lock the meeting when full