In addition to Google, Hackers or PenTester often use specialized search tools to find information about vulnerabilities of networks and Websites. Here are 6 commonly used Hacker Search Engines to find vulnerabilities arranged in functional order and serving different requirements.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
Shodan.io
Shodan is the world’s first search engine for internet-connected devices. Shodan bots will scan all public IPs in the world and record devices from these IPs.
Most search engines such as Google, Bing, and Yahoo only return the content of Web pages, but Shodan alone gives the results of servers around the world and scans internet-connected devices, collecting web pages. information related to the scanning servers such as what ports are open, what services are running, are there security holes?
There must be quite a few of you using Shodan to hack Security Cameras, right?
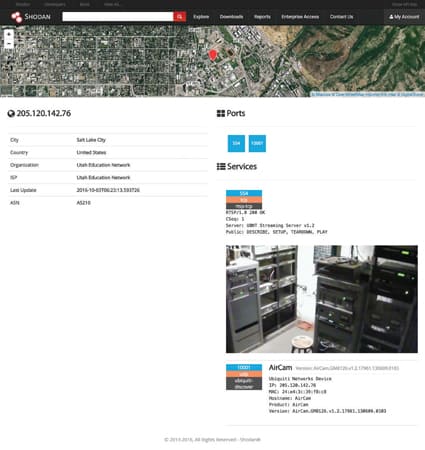
Shodan did that by generating a random IP, Port, testing the random IP and port, and then repeating this process for the most accurate results.
wigle.net
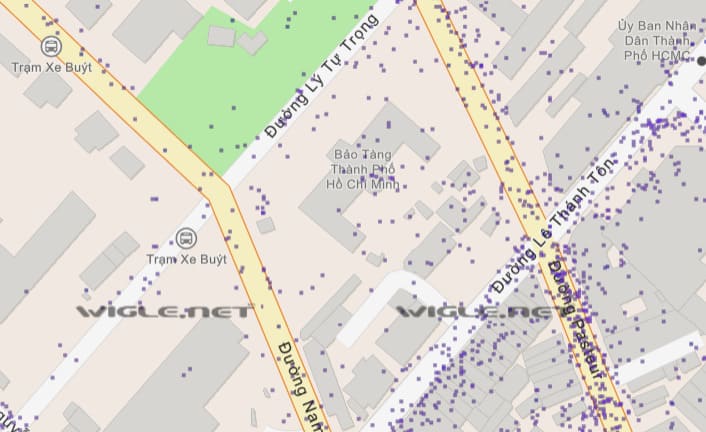
Wigle aggregates the location and information of Wifi networks around the world into a central database.
Wigle has a web and PC client for users that can map, query, and update databases.
Wigle can help you to monitor WIFI around you and detailed information about Wifi network; This is great if you intend to hack your neighbor’s WIFI or a certain cafe.
View articles about Hack Wifi on AnonyViet.
Hunter.io
Hunter.io works by searching and indexing email on corporate websites on the internet. Hunter.io will record common email patterns it finds, it’s like an Email directory, you can use Hunter.io to let OSINT find information about anyone or any company in the world.
This is a Hacker Search Engine often used to investigate a certain company, Just type any Domain, it will list Emails related to that Domain.
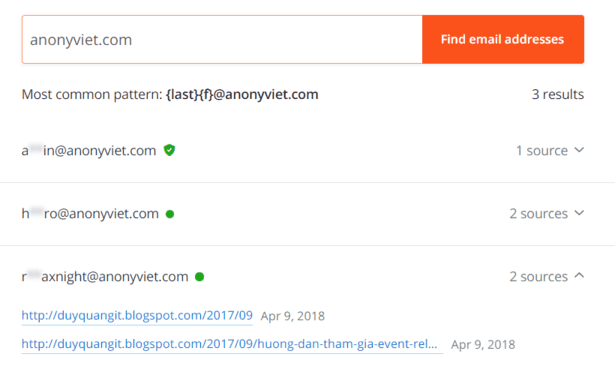
Job seekers can also use this feature to receive emails from the company they intend to send their CV to, which can be very interesting.
Vulners.com
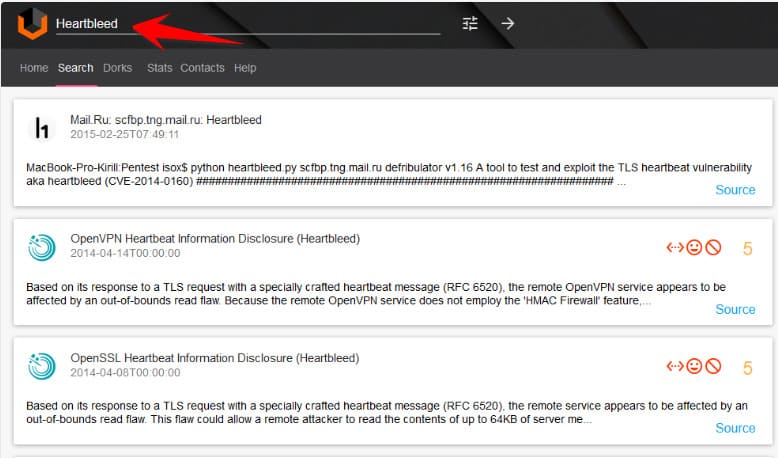
Vulners.com is a search engine that stores databases related to published security vulnerabilities in the world. vulners.com collects the latest news/articles on security from websites, security forums, lists of vulnerabilities found by researchers, content of vulnerabilities and how to exploit vulnerabilities from posts on hacking forums and even from Vulners.com’s Scan function. It also shows you how to attack the system through the name of the vulnerability found..
Furthermore, you automate the search process with the Vulners Search API. Free account gets 100 Credits/month.
pentest-tools.com is an Online vulnerability scanning tool, using more than 20 tools to scout, detect security holes and attack security activities.
You can use this tool to check the security of the website or the network on this Web site. Just enter the link and select the type of vulnerability to scan such as SQL Injection, XSS, Server Side-Request Forgery, Directory Traversal… or quickly scan the entire system. Just hang that link and wait for the results.
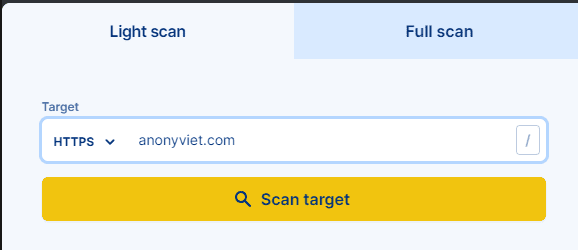
This web application security testing tool runs comprehensive website security checks to detect Log4Shell, OWASP Top 10 and high-risk vulnerabilities. You will receive a report with the vulnerabilities found to plan a fix or test attack.
Searchcode.com
Searchcode.com helps you find code and its examples on the Internet, it returns functions, APIs, and libraries in 243 languages across more than 10 codes on the Internet.
From there the Pentester, Hacker can study the code to find the loopholes of the programmer. However, for beginners, this can be a bit complicated and time consuming.