Using an incognito web browser will make your browsing experience much more secure. On the current market, there are many good anonymous web browsers, but in today’s article, I will introduce you to 4 good anonymous web browsers that you should use.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

Why should you use an incognito web browser?
Your personal information is a treasure trove of data that secret services, advertising services, cybercriminals, etc. all want to have.
While it’s almost impossible to completely erase your data from the global internet, there are a few things you can do to reduce your information footprint.
And one of the most effective ways is to use an anonymous web browser. Because the browser is your main communication when accessing the internet.
Enabling an incognito tab in your browser cannot make you completely anonymous. You can only be truly anonymous when using the anonymous web browsers below.
first. Tor Browser
https://www.youtube.com/watch?v=3FQaFlCeluk
Works on: Windows, Mac, Linux
Tor Browser has only one simple goal of anonymity. It is the best private anonymous web browser out there and the best browser to use the dark web.
Tor is designed to protect a user’s location, browser history, personal data, and online messages from anyone looking to perform network traffic analysis.
How does the Tor browser work?
Network traffic analysis is the most powerful skill of data collectors. It can track your behavior and preferences and discriminate prices on location-based online shopping sites, it can even reveal your identity to high bidders.
Basic encryption techniques do not protect you from traffic analysis. Data sent over the internet has 2 main parts: Payload and Header.
Payload is the actual data (e.g. the body of the email); header helps the data reach the destination. Include information such as source, size, and time. Encryption can only hide the payload, not the header.
And that’s when Tor appeared. It sends your internet traffic through so many individual relays and tunnels that Header scattered and rendered meaningless to data analysis tools. In a word, instead of going directly from A to B, Tor will send your traffic through Â, Â… and then to B.
If data collectors catch a single point on that route, they have no way of knowing where the data originated or where it is going. But is it completely anonymous to use Tor with a VPN? read this post just found out.
Tor . Browser Features
To access the Tor network, you need to use the Tor browser. It is so secure that the US Navy uses it for intelligence gathering. Tor is also used by law enforcement organizations who want to access websites without leaving government IP addresses in the website’s logs.
You do not need to install any software on your computer; Tor browser is a portable application that can run on USB. This means you can use Tor on any computer, even if it’s in a public place like a library or university or coffee shop.
Tor has a very similar design to firefox but the biggest difference is that it integrates NoScript by default. Unlike the regular NoScript add-on, the NoScript version on Tor has an easy-to-use slider to manage your privacy.
There are also some downsides to using the Tor Browser. For most users, the biggest issue is speed. Because your traffic is sent through a zigzag path to its destination, your browsing speed will not be fast. It doesn’t matter if you have a good connection, but if your internet speed is slow, Tor can be a bit unwieldy.
2. Epic Browser

Works on: Windows, Mac.
Epic Browser does not use a dedicated onion network, but Epic is able to neutralize many of your privacy risks while surfing the web.
Eg: it doesn’t save your history, doesn’t prefetch DNS, doesn’t allow third party cookies, has no web or DNS cache, and has no autofill feature.
When you close your Web browsing session, the browser automatically deletes any associated databases, preferences, and cookies from Flash and Silverlight.
3. SRWare Iron

Works on: Windows, Mac, Linux, Android.
If you are a Google Chrome user, SRWare Iron will be very familiar to you as it is based on the Chromium open source project.
The main difference between Chrome and SRWare Iron is data protection. Experts have criticized Chrome for its reliance on “Unique User ID”; every time you start a session, Google will warn about your data usage.
SRWare removes the use of IDs along with other Chrome privacy issues, such as search suggestions.
4. Comodo Dragon Browser
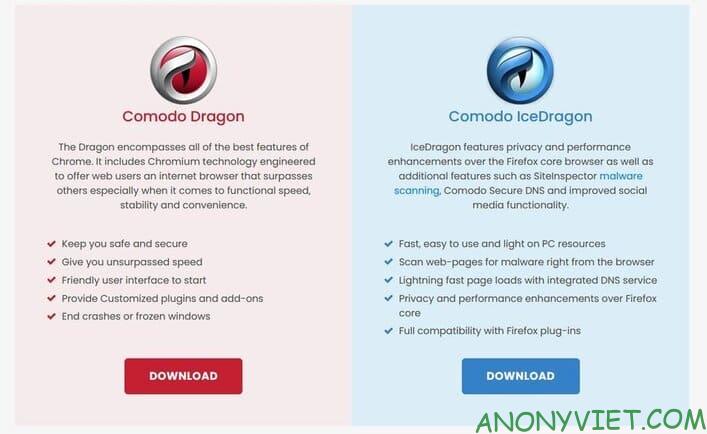
Works on: Windows, Mac.
Comodo isn’t as good as Tor Browser, but it has some built-in tools that will make browsing safer.
It automatically blocks all tracking, cookies, and built-in domain authentication technologies instantly classify strong and weak SSL certificates, and it uses Comodo antivirus to protect you from malware. malicious, viruses and other types of attacks.
Like SRWare Iron, Comodo is based on Chrome, so it should be quite friendly for many new users.







![[Tạo 2D Platformer Game với Godot] Part 2: Level Design [Tạo 2D Platformer Game với Godot] Part 2: Level Design](https://anonyviet.com/wp-content/uploads/2021/11/08-11-2021-10-29-43.png)


