OSINT stands for “open source intelligence”, which is the activity of finding information that you can access through publicly available data sources on the Internet such as from Google, Bing or specialized search engines. Pentesters use OSINT to research targets or learn about cyber threats. OSINT is an important tool for both Red Team and Blue Team. So in this article, I will introduce you to the top 10 OSINT tools for hackers.
| Join the channel Telegram belong to AnonyViet ???? Link ???? |
Top 10 OSINT Tools for Hackers
1. Shodan
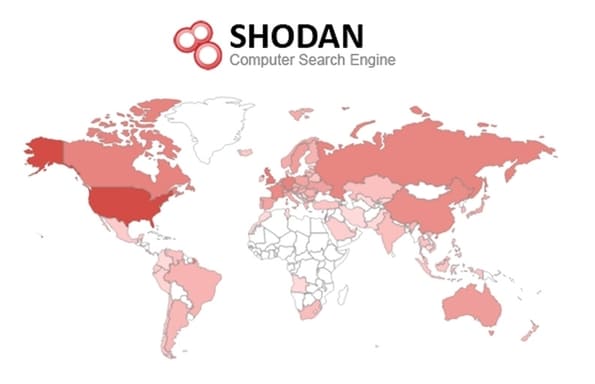
Shodan is a search engine for open devices on the internet, such as servers and IoT devices. These are devices that are publicly accessible to you. If the device is connected to the internet without careful security configuration, it can be found through Shodan.
The free Shodan version will limit the number of results. So the paid version is much more useful if you need to find servers, networking devices, and IoT peripherals (such as cameras).
2. Maltego

Maltego available on Windows, Mac, and Linux, giving users access to multiple data sources for OSINT, data research, and digital forensics purposes. There are over 58 data sources in Maltego including Google Maps, AlienVault OTX, ATII Hades Darkweb Intelligence, Blockchain.info, Crowdstrike, VirusTotal, etc.
The value that Maltego brings to you lies not only in huge data sources, but also in data patterns and trends through visualization. Of course, all the features of Maltego are not free, but I think the Maltego Community Edition version is enough for newbies.
3. Google Dorks

Google Dork It’s not an app, it’s a technique using Google. Although it’s not an app, there are developers who have developed open source software tools for Google Dorking that you can try, such as Pagodo and GoogleDorker.
Most people just type keyword strings into Google, such as “Vietnam weather” or “anonyviet”. But there are some search operators that you can use in Google. For example, you can try “site:anonyviet.com” to search for content within the anonyviet website, or use quotes around a search term to only return results containing that exact word. You can see more list of operators of Google Dork here.
A lot of websites are configured with very poor security. Google’s crawling bots visit these sites in search of content. So Google Dorking can be a useful technique for you to find data like email addresses, login information and phone numbers that are not properly secured.
4. Recon-ng
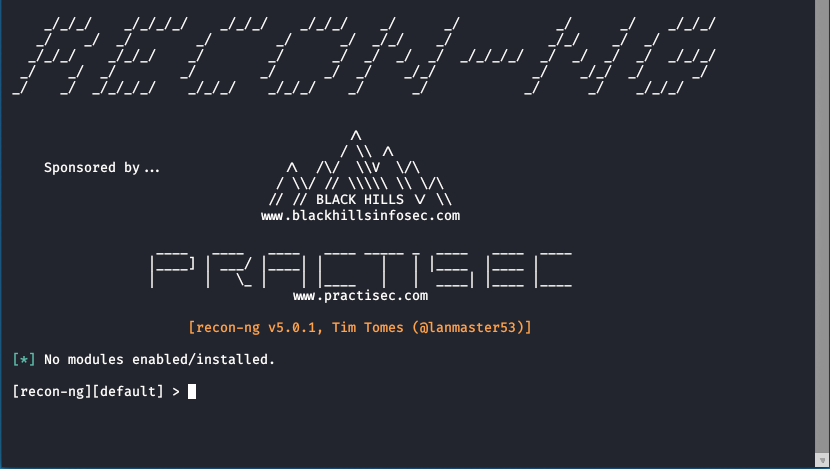
Recon-ng is an open source web reconnaissance tool. Its strength lies in the fact that you can install additional modules into this tool. If you use Recon-ng efficiently, you can save a lot of time in your OSINT work.
Recon-ng can be run from the terminal. If you want to add more power to Recon-ng, select Marketplace from the main menu and install the modules you want.
5. Ahmia.fi
Ahmia.fi is a search engine dedicated to finding websites on the Tor Network, although the search engine itself is accessible on the “clearnet”. But you’ll need the Tor Browser to open your search results.
There are many black markets and forums on the Tor Network, so using Ahmia.fi effectively will help with your OSINT investigation.
6. Wayback Machine

The Wayback Machine is a search engine for over 632 billion web pages, many of which date back to the 1990s.
Archive.org is using the Wayback Machine to archive as many web pages as possible. You can also use their website to manually host websites that are currently online. If these sites are deleted or down, you can find a copy of them stored in the Wayback Machine.
7. theHarvester

theHarvester is another useful open source scouting tool that you can install from GitHub. It can be used to collect email addresses, servers, subdomains, employee names and ports from various public sources such as search engines, PGP and Shodan.
You can easily run theHarvester from your command line. This tool has a special set of options for you to explore the data in the DNS server. DNS servers have a lot of useful information because they associate domain names with specific IP addresses.
Some of the data sources you can explore with theHarvester include LinkedIn, Bing, Google, and VirusTotal.
8. TinEye
TinEye is a powerful tool for image analysis. If you have a photo on your device, you can upload it to TinEye and see if the photo is being used on another web.
Specific use cases: Find other people’s information from their photo, the location where the photo was taken, or the app used to take the photo.
9. OSINT Framework
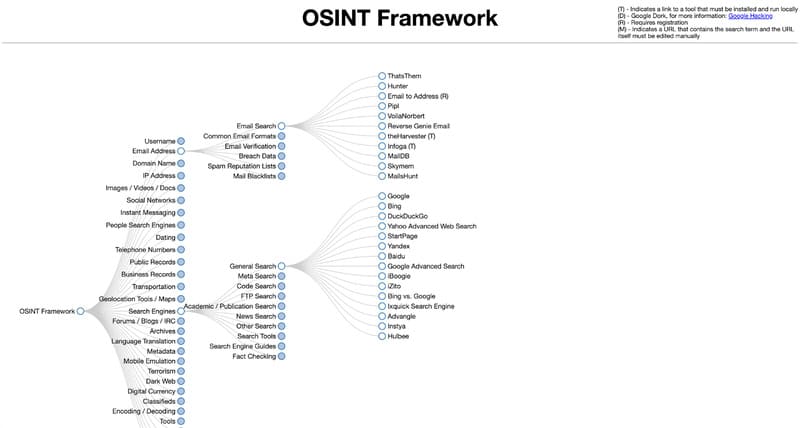
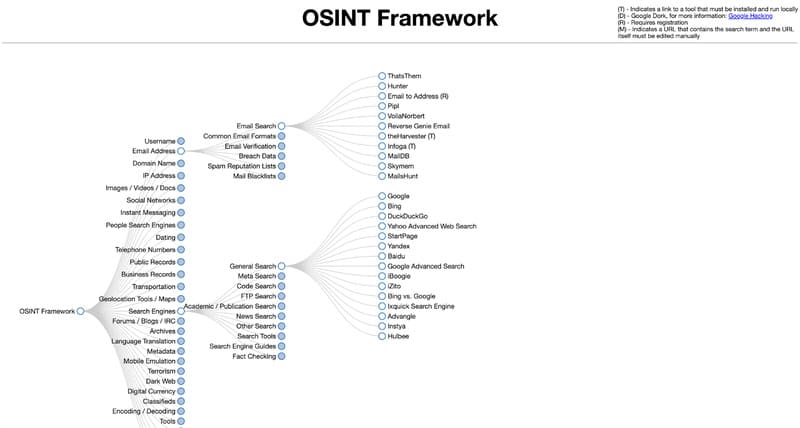
OSINT Framework is the perfect web app if you’re not sure what OSINT data source you’ll need to use to find the information you want. The OSINT Framework provides you with potential data sources that you can use.
You can analyze malicious files, usernames, geolocations, IP addresses, domains, IRCs, Dark Web, big data, threat information, phone numbers or more with this tool. OSINT Framework can be the first step in your OSINT journey.
10. Library
The best offline data source is a library. You can visit the library, or the library’s website can help you directly find the information you are looking for.
There is a lot of information that has not been digitized at the library such as magazines, newspapers and directories. In Ho Chi Minh, you can go to the General Science library. Sign up for a membership card and you can spend the day in the library. I often come here to run the deadline again :v.