Keylogger is spyware that records keyboard activities. Depending on the intended use, the Keylogger can hide itself while operating and avoid detection by the victim. In addition to recording the actions typed on the keyboard, Keylogger can also take screenshots, steal files, open backdoors for hackers to attack.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
Once upon a time when the game Vo Lam Truyen Ky was just born, street hackers often used Keyloggers installed in net shops to password hack Game. Because at that time, the net shop owners did not have such security experience now. And internet shops also rarely install freezing software, but even if they do, they will install it Deep Freeze. Deep Freeze at that time removed within 3 notes :D.
Gradually according to the development, from Virus -> Trojan -> Keyloggers -> RAT. Although RAT has more powerful functions than Keylog, RAT requires a bit more complicated configuration. As for Keylog, you only need to declare Email or FTP to receive Keylog data sent back.
If you want to study about RAT, you can Download synthesize 50 most powerful computer control RAT today.
How does keylog work?
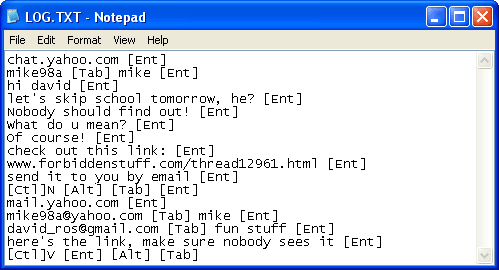
Record keyboard activity
Once installed, Keylog will silently Record keystrokes of the victim. That is, when the victim types something on the keyboard, Keylog will record it. With this, you can easily steal the victim’s account/password, see what content the victim chatted with, and what email he wrote? for whom…..
Take a screenshot, click
A nice feature of some Keylogs is screen capture according to the specified timeor take a picture when the victim clicks. Very good feature if you want to keep track of whether your lover is in a selfie xxx movie :D.
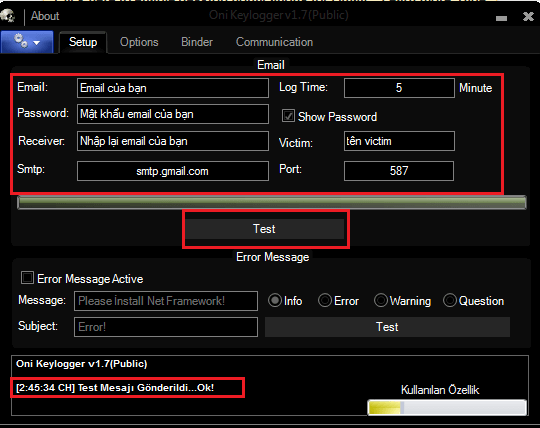
Send activity log to Email, FTP
Of course, you must have this feature to see the Log sent by Keylog. In the past, it was common to use SMTP of Yahoo and Gmail. Currently, if you want to receive Logs smoothly, you should create your own SMTP service, or configure an FTP account on Hosting to receive data.
For Gmail you should Turn on function Less Secure up for keylog to send mail.
Suicide feature
Keylog also has a suicide feature. This means that after a period of operation and completion of the task Keylog can kill itself to avoid detection later.
And there are many more features, you can discover more by yourself…
Summary of the 20 strongest KeyLoggers
Today, AnonyViet would like to share with you 20 Strongest Keylogs, and the most popular today. The list below, you download and use offline. These Keylogs have been cracked into full-featured copyrights.
- Actual Keylogger v3.2
- Actual SPY 3.0
- Any Keylogger 2.30
- Ardamax Keylogger 4.4
- Award Keylogger Pro.3.8
- Blazingtools Perfect Keylogger v1.7.5.0
- Elite Keylogger V5
- HawkEye Keylogger Cracked
- iSafe All In One Keylogger Professional Edition 3.5.8
- iSafe Monitoring Pro 7.0.0
- iSpy keylogger
- Keylogger Douglas 2.0
- Perfect Keylogger 1.68
- Refog keylogger Version 5
- Revation Keylogger v3.0
- Revealer keylogger
- Spy King Keylogger
- Spy Tector keylogger Cracked
- SpyBoss KeyLogger Pro 4.2.3
- The Best Keylogger 3.54 Build 1000
- The Best Keylogger 3.54 Build 1006
- The Conquerers Keylogger
Password: anonyviet.com