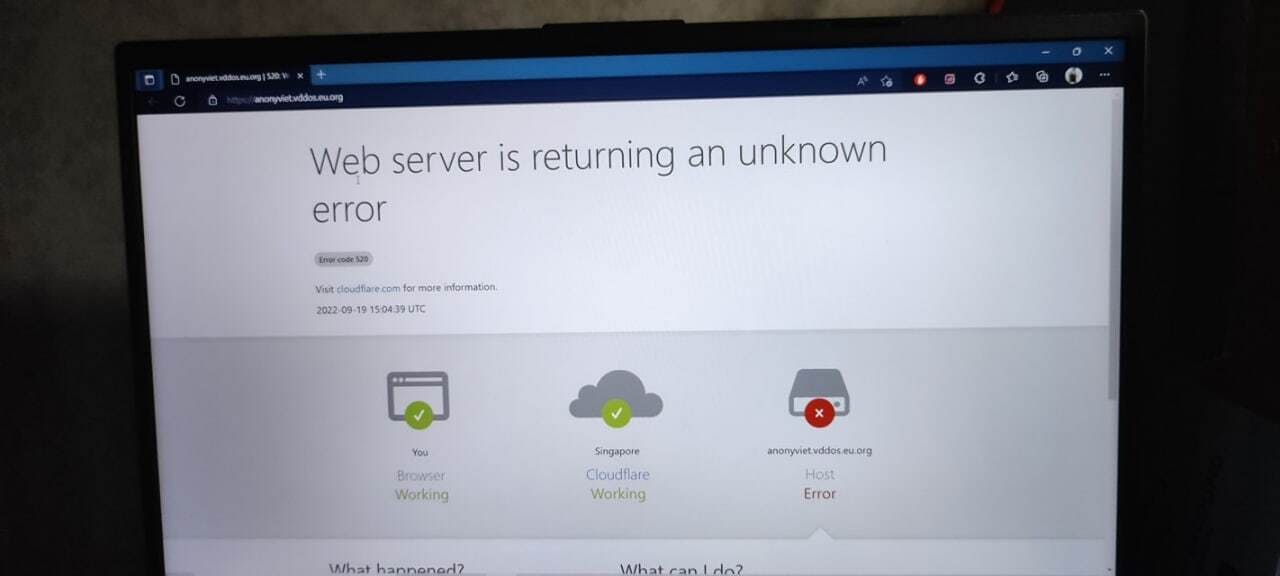
After launching the Event DDoS and AnonyViet system at: https://anonyviet.vddos.eu.org/, there were many teams and many singles participating, creating an extremely interesting brainstorm between the parties. Attack (you) and defender (AnonyViet + vDDoS). After opening the Server 2 times, I would like to briefly summarize as follows:
– The server of the site https://anonyviet.vddos.eu.org has a capacity of 4GB RAM, 4 Core CPUs, rented at TOTHOST.
– Installed Antiddos proxy of vDDOS enable 2 mixed layers: javascript obfuscate class Deep Encrypted + Invisible Captcha class (I will have a tutorial on how to install vDDoS later).
– Cloudflare Free, enable international IP Captcha, open BOT Search.
– A total of 4 people sent the link to check-host report properly, noting that the Server was Down.
Day 1
This is the picture before launching the Event
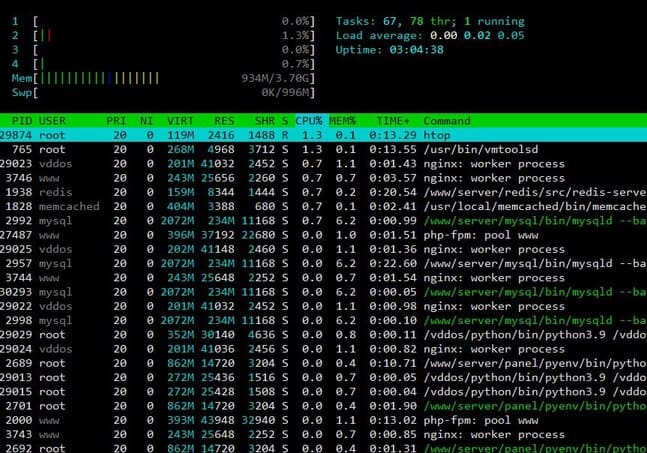
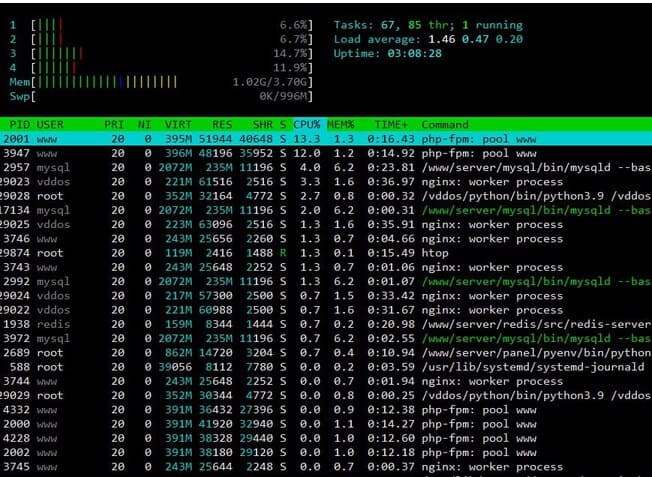
And 5 minutes after launching, some of you started to attack the Server, the CPU started to jump, but still at the level of maintaining the system.
Starting Style POST, HEAD, GET are deployed continuously, because there are many DDoS friends at the same time, many methods are recorded, but most of them are blocked by vDDoS Proxy
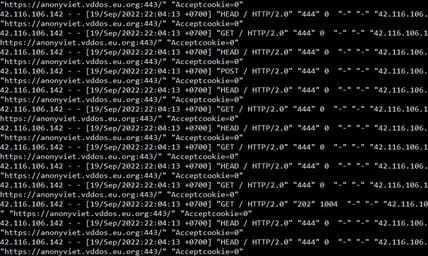
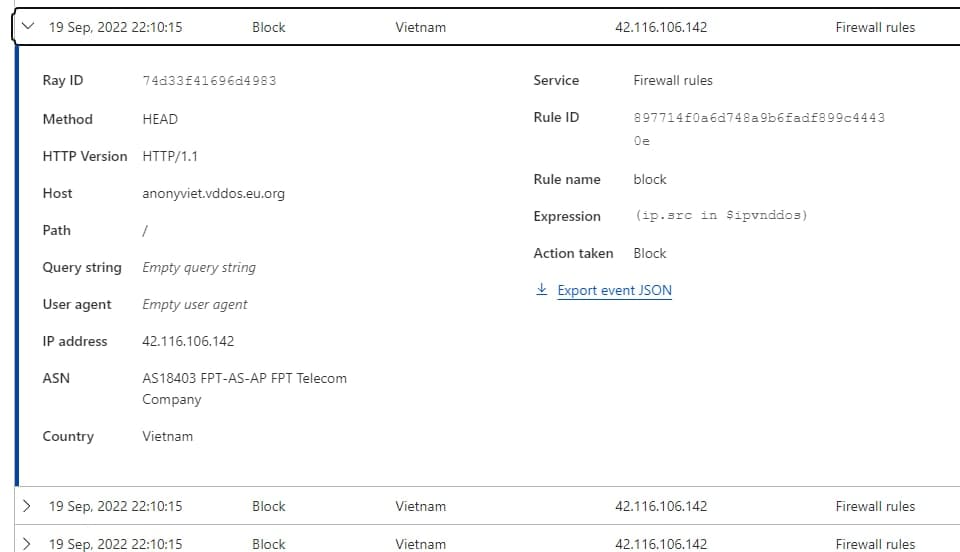
As in the picture "Acceptcookie=0" ie was blocked by vDDoS before entering the Backend. Due to being quite subjective, Team AnonyViet only allows frequency scanning 10 minutes times to push the bad IP to Cloudflare, so 1 member quickly sent a Report to the page https://anonyviet.vddos.eu.org after 15 minutes launch attack
After being knocked out in episode 1, Team decided to increase the frequency of scanning IP violations 3 minutes times, to avoid overloading the system.
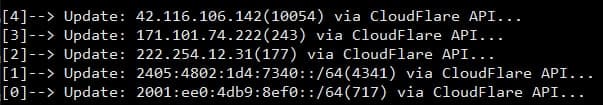
Typically IP xxx42 has up to 10K connections, no matter how soon the server will crash again.
And the result after increasing the junk IP filtering frequency, you can see below the picture, the front is IPs, and behind is the number of IP messages that are sent to the Server.
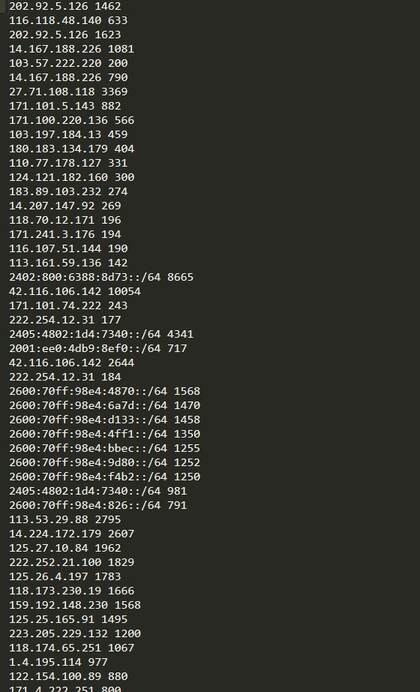
After 2 hours of watching, the server was fine, the CPU remained at 1.2%, so Team decided to go to sleep. The result recorded the total number of connections from international to 9.26 million requests
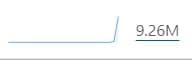
In which, the offending IP was pushed to Cloudflare by the Server to block 523K connections.

Was about to go to sleep, when a member hit HEAD, causing the CPU Server to jump from 5% to 100%. At that time, Team decided to block the HEAD method to ensure the safety of the system. Fortunately, it was timely, so the Web was not down. It was also late at this time, so we officially went to bed, in the end of day 1, we scanned 200 bad proxies.
The next morning, when I checked Cloudflare, I saw that last night there were 28 million requests from abroad attacking the Server.
The system pushes IP 4.18 million requests to Cloudflare to block.

Because Team set the scanner to be 100 packets to fail, that IP was banned, so it means that vddos has to bear x100 times this block before transferring it to Cloudflare’s IP. Therefore, the server’s Downtime ability at the most critical level will be about 30 seconds – 1 minute.
So the next morning, one of you Report Check-host recorded Server Down episode 2. Officially the system was Knock-out episode 2 and we had to close the Server, because we didn’t have time to monitor the defense during the day.
Day 2
Day 2 is still the same, after the launch, there were also small DDoS attacks from the participants in the Event, but the Server was almost unmoved. So my Team decided to invite the “Thai” guys to join, Thailand has a pretty strong DDoS Team, can solve ReCaptcha v3 and pass through our Proxy Server.
After inviting Vietnamese Member and Thai Team to join DDoS https://anonyviet.vddos.eu.org/ then officially crashed, knocked out episode 3. At this time, 2 of you also received the link report check-host.
Our side is planning to solve it by converting ReCaptcha v3 to ReCaptcha v2 (v2 has to be solved manually to bypass), but because it’s late, we decided to stop here. When I have time, I will reopen the Server for you to stay awake.
About how to configure vDDoS, you can refer to http://vddos.voduy.com/. I will write a tutorial later, if you have any needs, please comment below.
On the margins
During the reporting process, there are some dishonest cases such as:
– Get other people’s reports to receive rewards.
– When I announce to turn off the Server, then of course Check-host will report a Web error, you still get the Link Check-host when the Server is off to receive a reward.
– Some of you when you can’t DDos http://vddos.voduy.com/ then turn to DDoS https://anonyviet.com/ , Admin is quite heartbroken 😯
– Some of you with IP limit think that you have DDoSed AnonyViet and sent a shocking video like on TikTok =))
In general, a lot of depression happened in this Event, AnonyViet thank you for your enthusiastic participation ^^.