Anonyviet Please send readers the full set of tools 3 tools to infiltrate the computer. It’s just a tool, but they’re actually you virus created by us and sent to the victim. When the victim activates it The virus will connect to the server, create a connection and do everything it is asked to do.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
SSH Toolkit ( Admin 2908 )
- RAT SSH (RAT is used to penetrate the computer)
- Key Logger SSH (Used to record computer keyboard operations)
- Crypter (Use encryption – bypass antivirus)
All 3 tools will be integrated into the same program and you can use all three tools at the same time
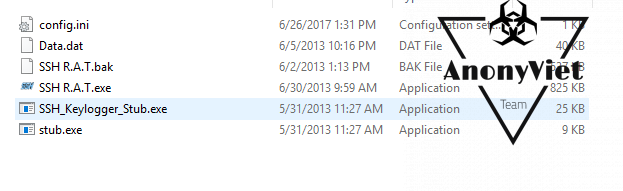
When extracting, you need to check if the files are still enough as shown in the picture! Because if Turn on Antivirushey you need turn off.
If you don’t feel safe when you turn it off antivirus then please turn on Freeze the computer. After freezing, just use it.
Why is it safer to freeze the computer and then use it?
Because when you freeze your computer’s state will be secure at that time. When the computer is restarted, it will return state before freezingthen all damage caused by the virus are all deleted. You can also imagine yourself freeze time that’s on the computer.
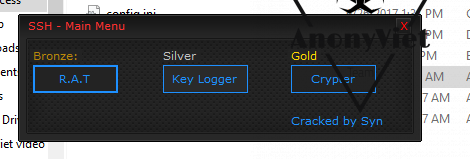
After opening SSH RAT, You will see a trio of tools appear as shown in the image including RAT, Keylogger, Crypter, …
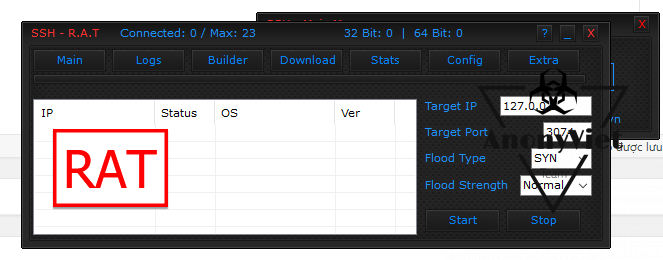
This is RAT – Use to infiltrate and control the victim’s computer completely
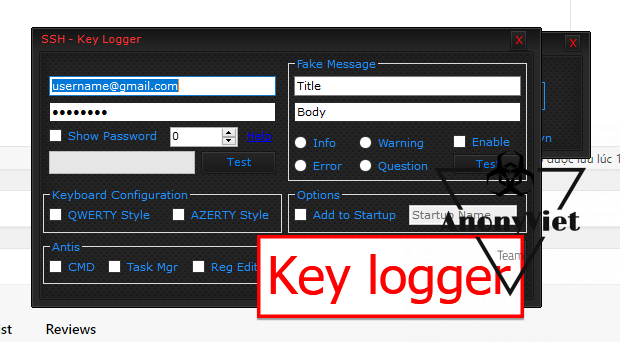
This is Key Logger – hide yourself and record the victim’s keystrokes

This is Crypter – Bypassing Antivirus
Download
Decompression pass: anonyviet.com
I will release a video soon Live Stream use on Fan Page Anonyviet. Hope this toolkit will make you enjoy.
Hope you have a great experience!
Anonyviet – Better and better











