Trojans and Backdoors are two methods that hackers use to illegally infiltrate the target system. They have different states, but have one thing in common: The hacker must install another program on the target computer, or the user is tricked into installing a Trojan or Backdoor program on their computer. .
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
1. Trojan
Trojan A type of malicious code named after the legend of “Trojan Horse”. A Trojan is a program which contains dangerous and malicious code hidden in the form of good data but the program appears to be innocuous as far as this feature it can control and cause harm, for example opening a distribute files in your hard disk.
2. Backdoors
A backdoor is a program (program) or related to a program, used by a hacker to install on the target system, in order to give him back access to the system at a later time. The purpose of the backdoor is to verifiably remove the logging system. It also helps hackers to stay in access status when detected by the administrator and find a way to fix it.
3. The purpose of the trojan
• Steal information such as passwords, credit card security code information using keylogers
• Using the victim’s computer to create a botnet (ghost computer network) to perform DDOS attacks
• Delete or replace important system files
• Create a fake connection to attack DOS
• Download Spyware Adwares and Malicious Files
• Disable firewalls and anti-virus software
• Screen capture, audio recording, screen recording of the victim’s device
• infect the victim’s PC as a proxy server for relay attacks
• Using the victim’s computer to spread spam and mail bombs
4. Recognizing a Trojan Attack
• CD-ROM drive opens and closes by it
• Your computer’s browser redirects to unknown pages
• Anti-Virus is disabled or its properties are not active.
• Taskbar disappears
• The chat dialog is appearing on the victim’s computer
• The color setting window is changed
• Windows Start button disappears
• Account and password changed or not authenticated
• Computer screen turns upside down or upside down
• The settings of the idle screen change automatically
• The service provider complains that the victim is scanning his ip
• Unusual purchase reports appear on your credit card
• Wallpaper and background change
• Functions of left and right buttons are reversed
• People know a lot of information about the victim
• The computer screen is turned off by it
• Document or message printed from your printer
• Mouse pointer disappears or moves by it
• The computer is turned off or turned on by it
• Shortcut Ctrl+Alt+Del stops working
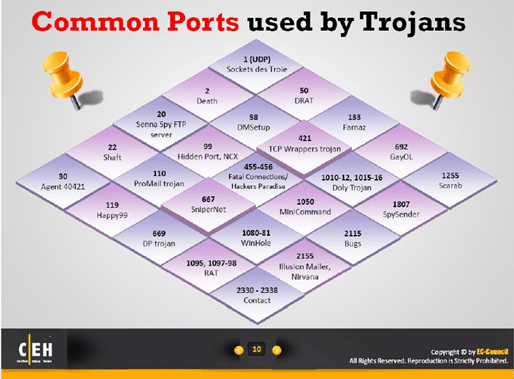
5. Ports used by popular trojans
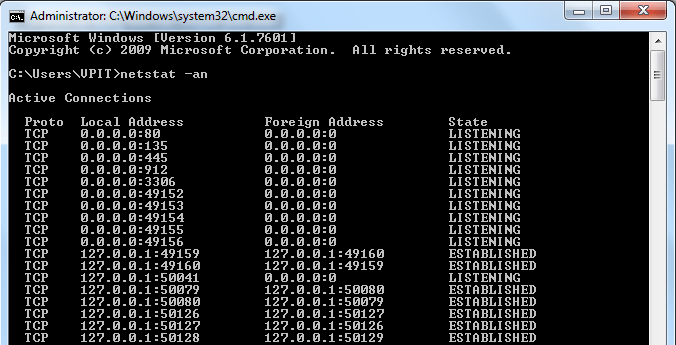
How to use netstat -an command in CMD mode to see the status of ports?
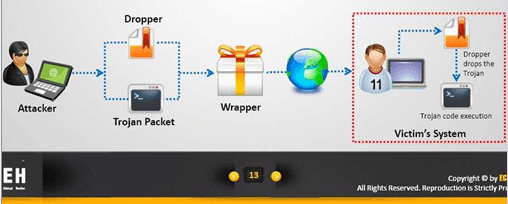
6. How are Trojans deployed?
• Create a new Trojan using Trojan house Construction Kit
• Creates a Trojan, part of a Trojanized package that installs malicious code on the target system
• Create a wrapper to install on the victim’s computer
• Dissemination of Trojans
• Implement droppers
• Regular enforcement of termites
7. How does the Trojan infect?
• Legalize an illegal package in packaged software
• Fake program
• Download files, games and screensavers from sites on the internet
• Untrusted freeware sites
• NetBIOS (Share files)
• Instant messaging app
• IRC(Internet Relay Chat)
• Attachments
• Physical access
• Errors in browser and mail software
8. Classification of trojans
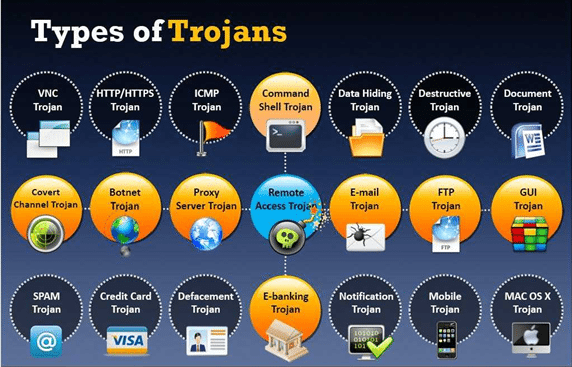
a. Command shell Trojan
• The Trojan Shell command allows remote control of the shell command on the victim’s computer
• The Trojan server is installed on the victim’s machine, in which it opens a port for the Attacker to connect to.
A workstation is on the Attacker’s machine, where it is used to run shell commands on the victim’s computer
b. Email Trojans
• Attacker remotely controls the victim’s computer by sending an email
• Attacker can get files or folders by sending commands via email
• Attacker opens SMTP relay server and spoofs email from a field to hide the origin
c. Botnet Trojans
• The botnet Trojan infects a large number of computers over a large geographical area, creating a network of bots controlled through a central Command and Control (C&C)
• Botnets are used to launch a variety of attacks on a victim including denial of service attacks, spamming, click fraud and financial information theft
d. Proxy server Trojans
• Trojan Proxy is commonly used as an application that allows a remote attacker to use the victim’s computer as a proxy to connect to the Internet.
• Proxy server Trojan, when infected, starts hiding a Proxy server on the victim’s computer
• Thousands of computers on the Internet are infected with Proxy servers using this technique
e. FTP Trojans
• FTP Trojans install FTP server on victim machine, it opens FTP port
• Attacker can connect to the victim’s machine using the FTP port to download any file that exists on the victim’s computer.
f. VNC Trojans
The VNC Trojan starts a VNC Server daemon on the infected system. It connects to the victim using any VNC viewer with the password “secret”. When the VNC program is scrutinized, the Trojan will never be detected by the anti-virus.
g. HTTP/HTTPS Trojans
• HTTP Trojan can bypass any firewall and work under the reverse of an HTTP tunnel
• They are executed on the local host and then self-replicate in a pre-calculated cycle
• Subroutine appears to the firewall user thus allowing Internet access
H. Remote Access Trojan
The Trojan works like accessing Remote Desktop. Hacker takes over all GUI to access remote system
• Infects computer(Rebecca’s) with server.exe and back-connecting Trojan
• Trojan connects to port 80 so that the Russian attacker establishes a reverse connection
• Jason, the attacker, has full control of Rebecca’s machine
i. . E-banking Trojans
E-Banking Trojan Intercepts the victim’s account information before it is encrypted and sends Trojan commands to the attacker’s control center.
k. Destructive Trojans
• This is a dangerous and destructive type of Trojans
• When executed this Trojans destroy the operating system
• Trojans format all local and network drives
• User will not be able to boot the operating system
l. Encryption Trojans
• Encryption Trojan: encrypts data files in the victim’s system and makes the information unusable
• Attackers ask for a ransom or manpower to make purchases from their online drug stores in return for the password to unlock
9. Detect trojans
• Run Trojan scanner to detect Trojan
• Scan for suspicious NETWORK ACTIVITIES
• Scan for suspicious changes to OS FILES
• Scan for suspicious STARTUP PROGRAMS
• Scan for Suspicious FILES AND Folders
• Scan for suspicious DEVICE DRIVERS installed on the computer
• Scan for suspicious WINDOWN SERVICES
• Scan for suspicious REGISTRY ITEM
• Scan for suspicious OPEN PORTS
• Scan for suspicious RUN PROCESSES
10. Countermeasures against Trojan
• Avoid downloading and executing applications from untrusted sources
• Avoid opening email attachments received from unknown senders
• Install patches and security updates for operating systems and applications
• Scan CDs and floppy disks with anti-virus software before use
• Avoid accepting instant messaging schemes
• Block all unnecessary ports at servers and firewalls
• When hardware is weak, Set default configuration
• Disable unused functions including protocols and services
• Avoid typing commands blindly and execute pre-made programs or scripts
• Monitor intranet traffic for odd ports or encrypt traffic
• Workstation local file integrity management through checksums, audits, and port scans
• Run versions of anti-virus, firewall, and intrusion detection software
• Restrict access in the desktop environment to prevent malicious applications from installingat on
11. Countermeasures against backdoors
• Most commercial anti-virus products can automatically scan and detect backdoor programs before they can cause damage
• Prevent users from installing apps downloaded from untrusted Internet sites and email attachments
• Use anti-virus tools such as Windows Defender, McAfee, Norton to detect and remove backdoors
\
12. Penetration testing
• Scan system for open ports, running processes, registry keys, device drivers and services If any suspicious ports, processes, registry entries, device drivers or services are detected , check the related executables
• Gather more information about the word from the publisher’s website, if available, and the Internet Check if open ports are known to be opened by Trojans in the wild
• Check startup programs and determine if all programs in the list can be recognized with known functions
• Check data files for modification or manipulation by opening several files and comparing the hash value of these files with a precomputed hash
• Check for suspicious network activity such as bulk file uploads or unusually high traffic going to a specific web address
• Check for important OS file modifications or manipulations using tools like tripwire or compare hashes yourself if you have a backup
• Run an updated Trojan scanner from a reputable vendor to identify Trojans in the wild.
• Text all findings in previous steps, it helps in determining next action if Trojans are identified in the system
• Isolate the infected system from the network immediately to prevent further infection
• Complete system disinfection for Trojans using anti-virus updates