What is MITER ATTCK? Let’s find out in this article. As technology advances, we are more and more aware of the importance of network security. The danger of cybercrime also increases year by year. To deal with this, cybersecurity professionals are embarking on the development of new security tools to fight hackers every day. Among these tools, there is a very famous framework called MITER ATTCK which contains different techniques, vulnerabilities and attack procedures for organizations to identify vulnerabilities in their systems.
| Join the channel Telegram belong to AnonyViet ???? Link ???? |
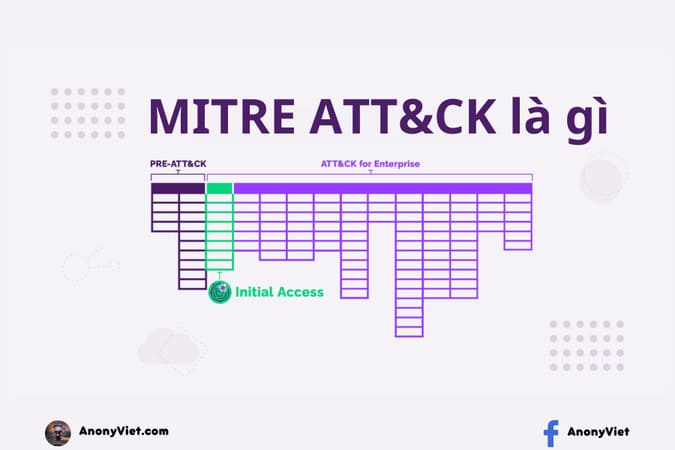
What is MITER ATT&CK?
MITER ATTCK (MITER AT&CK) is an open framework that contains real-world attack tactics and techniques. This framework is completely free, it provides various tools for data protection or system security.
This framework allows us to share a common set of communication principles with other cybersecurity teams including: red team, blue team, SecOps, etc. In addition, it also mimics the behavior and tactics of attackers to help us identify risks and prepare defenses against possible attacks. So it’s a great resource for IT security teams.
While it offers a lot of benefits, it’s still a tool, so it’s not perfect. MITER AT&CK has some limitations because not all techniques are malicious, so it can detect some that are not a real risk.
However, its advantages outweigh its disadvantages. So I think you should try it, maybe it will be useful for your system.
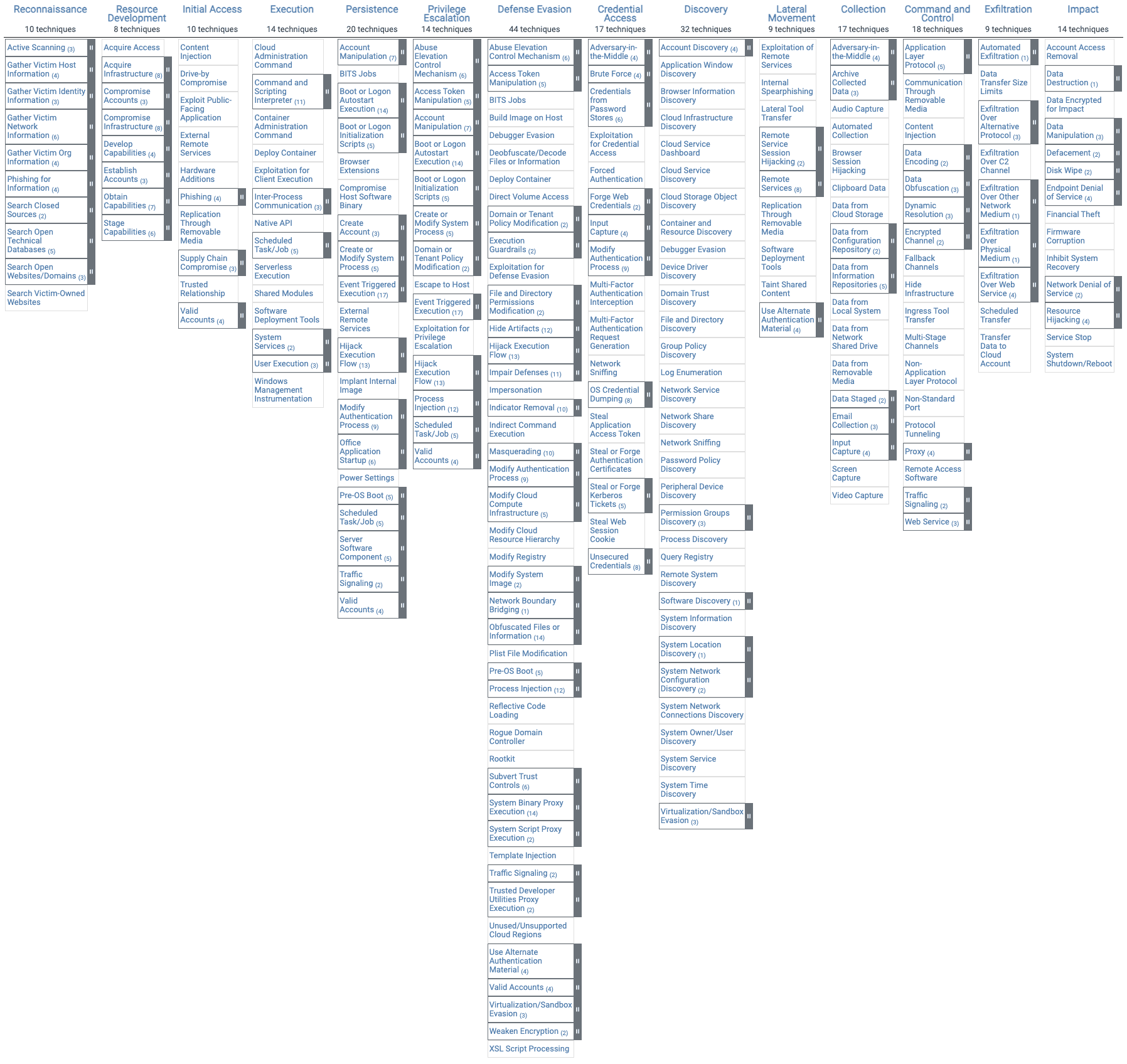
How to use MITER ATTCK
In fact, this framework only describes and classifies malicious behavior, so we need a tool to apply all the information it provides.
You can implement it by mapping or continuous integration (CI/CD) using various cybersecurity tools. The most common method is to use tools such as Security Information and Event Management (SIEM) or Cloud Access Security Broker (CASB).
Alternatively, you can deploy it in your CI/CD environment using tools like GitLab or Jenkins.
Using MITER ATTCK with Kubescape Cloud
There are many different tools to scan and secure the system with MITER ATTCK. But in this article, I will use the open source tool Kubescape.
Kubescape is an open source tool for vulnerability scanning on K8s assemblies and YAML files, it checks for software vulnerabilities using RBAC and risk analysis, and detects misconfigurations according to various Frameworks, including the MITER ATTCK Framework.
Simple Demo Using Linux
I just demo simply because according to the needs of each person, the process will be quite different. You only need 3 steps to use Kubescape.
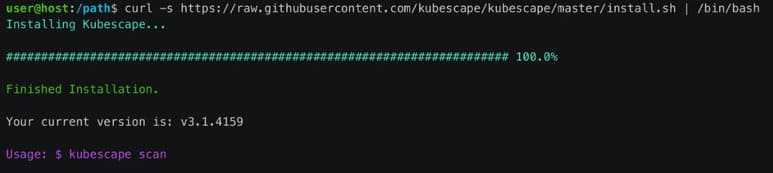
Step 1: Download Kubescape.
I will download Kubescape to the device with Kubectl. So you need to install Kubectl and have the cluster running. Then you just need to open terminal and run the command below:
url -s https://raw.githubusercontent.com/kubescape/kubescape/master/install.sh | /bin/bash
Step 2: Run kubescape. After successfully installing Kubescape, you can scan your system with the command below:
kubescape scan --submit
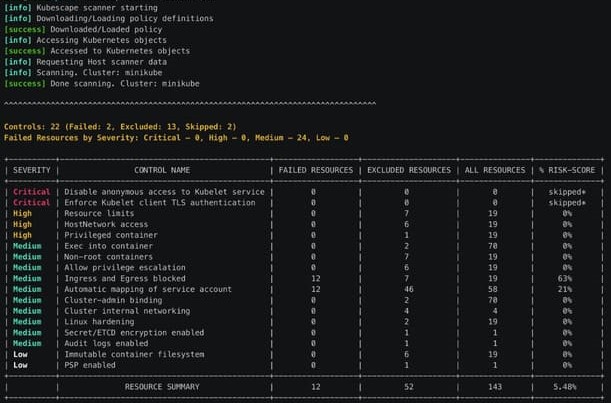
As you can see, the cluster that I created is quite risky. In addition, you can also export the scan results to PDF format.