Google’s advanced search operators are called Google Dorking. Why can hackers use this technique to find vulnerable vulnerabilities? In a word, this technique uses Google to search for exactly what you want using specific keywords or commands. Basically, it narrows down the search to find what you need. 
| Join the channel Telegram belong to AnonyViet ???? Link ???? |
Google Dorking uses some of the inherent capabilities of google to find exact things on the internet through specific search strings. It can be log files, error files, webcams opened on the internet and even internal or admin pages that give us access to the device. In some cases, you can also find the password in the error log file. Sometimes even the administrative configuration files are exposed to the internet because the server is set up incorrectly.

Google Dorking is done by Google search operators. Some typical operators:
- site:
– used to limit search results to a specific site. For example, google to find hack related blogs on the website https://gourav-dhar.com: hacking site:gourav-dhar.com - inurl:
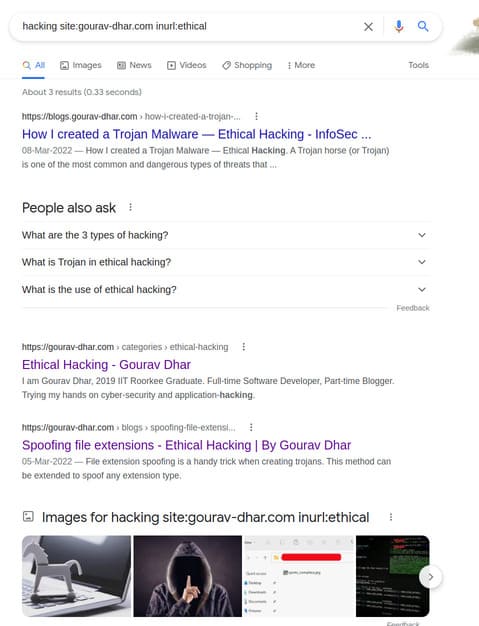
hacking site:gourav-dhar.com inurl:ethical
You will get the following results:
- intext:
– This operator checks the parameters contained in the site’s metadata (i.e. the information you see on the title and description of a google search). - intitle:
– Results will only return pages that contain the keyword in the HTML title - allintitle :
– Search for all keywords specified in the title. - allinurl :
– Search all keywords in url. - filetype:
– Look for clear document types. filetype:pdf will search for pdf files contained in web pages - ext:
– Same as filetype. ext:pdf finds the pdf extension. - cache :
– Used to see the Google cached version of a web page
And there are several other search operators that can also be found via Google Search.
How to Find Vulnerable Vulnerabilities Using Google Dorks
1. Check the log for login information
allintext:username filetype:log
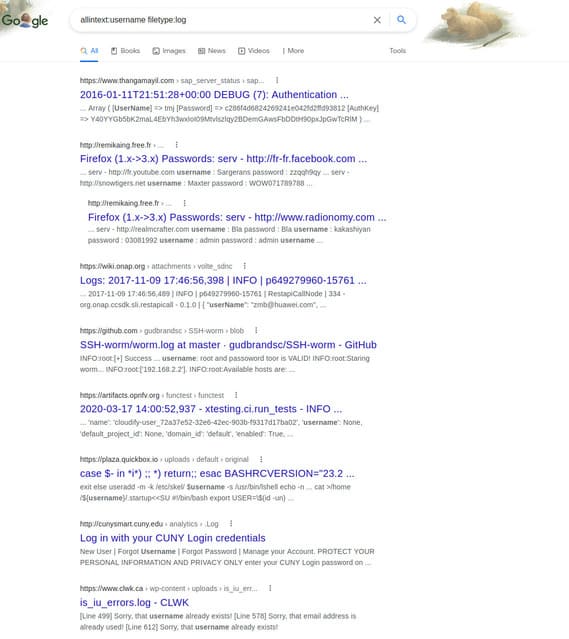
We will get a list of log files containing “username”. This can be useful to hackers if the log contains user credentials. If you explore the results a bit and apply filters, you should be able to find a username or password for further mining.
2. Find vulnerable webcams
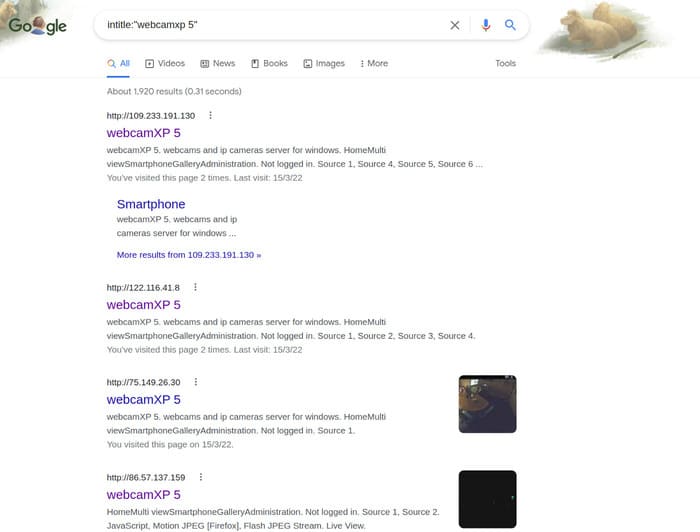
Google intitle:”webcamxp 5" and you’ll find a list of webcams that you can access right away.
I can watch live webcams of some classes. 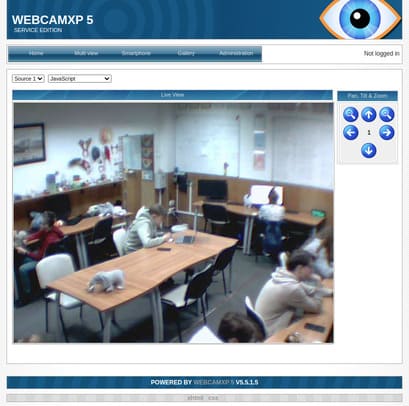
The best place for you to start practicing is Google Hacking Database. If you are unsure about search operators, then you should check out this site. Some people have searched before so you can use their search queries. The Google Hacking Database or Exploit Database looks like the image below and you can enter your queries in the top right.
Summary of Google Dorks
What I just did above is not illegal. We are only looking for information that has already been made public. Hackers use google dorks to find information that may have been accidentally made public. However, it is up to the person to use this information.











