In this article, we will learn how to exploit Command Injection errors through the OsCommandInjection room on TryHackMe.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

How to exploit Command Injection error
Command Injection is the abuse of an application to execute commands on the operating system using the same privileges as the program executing on the device.
- Command Injection remains one of the top ten vulnerabilities in OWASP.
It is also known as “Remote Code Execution” (RCE) because an attacker can trick the application into executing a string payload provided by an attacker without direct access to the system itself (i.e. an interactive shell).
The web server will continue to process and execute the code under the “privilege” and “access control” of the person running the application.
- Furthermore, due to the ability to execute code remotely within the application, these vulnerabilities are most often hunted by attackers because they allow attackers to actively communicate with the vulnerable system, allowing attackers to attack that reads system files, data, or other similar things.
command: whoami – It will list the victim’s account under which the application is operating as an example of command injection.
[Question 1.1] Read me!
Answer: No need to answer.

This vulnerability exists because applications frequently use functions in programming languages such as PHP, Python, and NodeJS to pass data and make system calls on the machine’s operating system.
Example: Take input from a field and look for the entry in the file.
Examples of these functions:
- This type of data is usually stored in a database, and that’s where the application collects user input to interact with the application’s operating system.
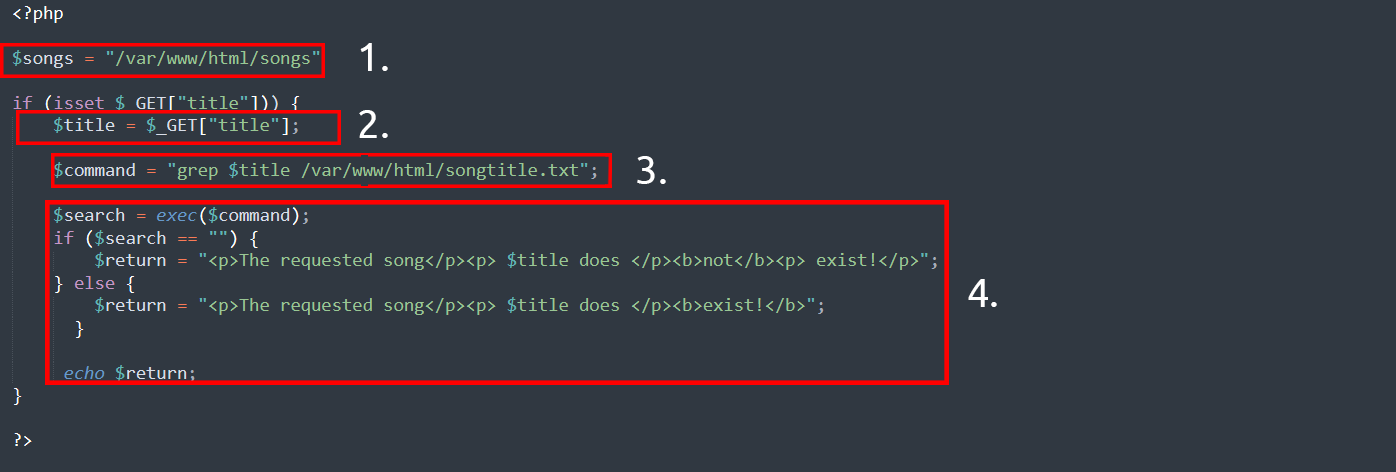
1) The application stores MP3 files in a folder present on the operating system.
2) User enters the name of the song they want to search. The application saves this input in the $title variable.
3) The data in this $title variable is passed to the grep command to search for a text file named songtitle.txt to type whatever the user wants to search for.
4) The search results of songtitle.txt will determine whether the app notifies the user that the song exists.
An attacker can take advantage of this program by issuing their own commands for it to execute. Instead of using grep to look for an entry in songtitle.txt, an attacker could ask the application to read data from a more sensitive file.
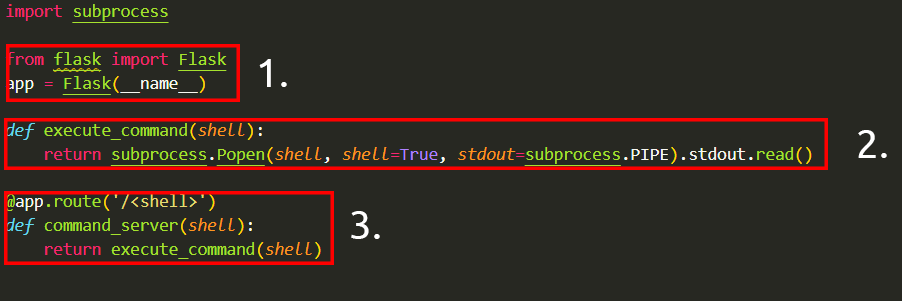
1) The “flask” package is used to set up the web server
2) A function that uses the “subprocess” package to execute a command on the device
3) The web server will execute whatever command is provided. For example, to execute whoami, I just go to http://flaskapp.thm/whoami
[Câu hỏi 2.1] Which variable stores the user input in the above PHP code?
Answer: title
[Câu hỏi 2.2] What HTTP method is used to retrieve user submitted data in PHP script?
Answer: GET
[Câu hỏi 2.3] If I want to execute the id command in the Python script, I need access route any?
Answer: /id

Applications that use user input to provide data to the system can often lead to unexpected behavior.
Shell operator:
first) ; = is functionally similar to “&&”, in that it does not require the first command to be executed successfully, which means that if the first command fails, the second will still run.
2) &= Because it is a background operator, the command will continue to run and you will be able to perform other tasks (that is, can run concurrently with the first command)
3) && = Symbolizes “and”, it will execute the second command after the first command is completed successfully, note that the first command MUST SUCCESS to run the second command.
In most cases, Command Injection can be detected in one of two ways:
- Blind Command Injection – When testing the payload, there is no direct output from the application and must analyze the behavior of the application to discover if your payload was successful.
- Verbose Command Injection – After you have checked the payload, the attacker will get an immediate response from the program. For example, you can use the “whoami” command to see what user the application is running as and the username will be displayed directly on the page.
Detect Blind Command Injection:
- This method has to use payload, so it is a bit time consuming.
- If possible, force some output.
1) ping = The application will hang for x seconds, depending on how many pings you specify.
2) >= It is “redirector”, which means we can take the output of a command (such as “cat” to output a file) and redirect it somewhere else. Once redirected, we can use “cat” to read the contents of the newly created file.
3) whoami = Print the username corresponding to the current user id.
4) curl = This is a great approach for testing as it sends and receives data from an application in your payload.
Detect Verbose Command Injection:
- One of the simplest methods is for the application to provide feedback or output about what is happening or is being run.
ping hoặc whoami được hiển thị trực tiếp trên ứng dụng web
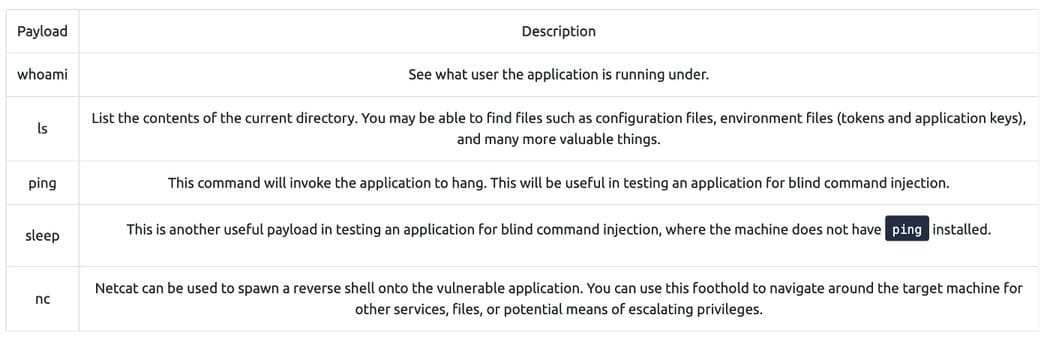
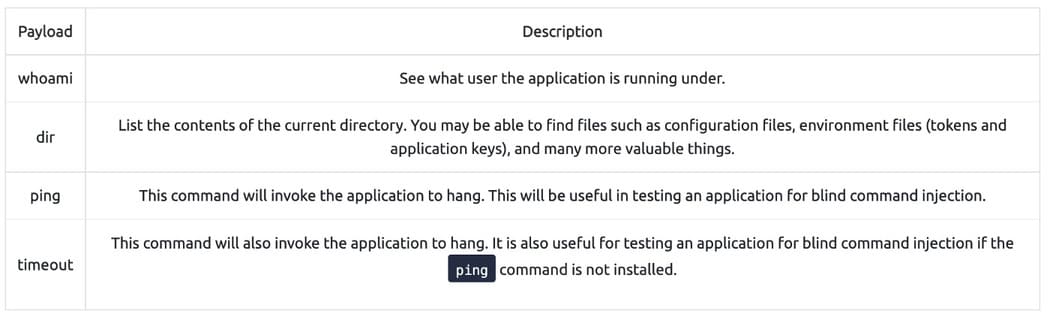
Useful Payloads:
- Linux

- Windows

[Câu hỏi 3.1] I will use payload What if I want to identify the user under which the application is running?
Answer: whoami
[Câu hỏi 3.2] Which popular networking tool would I use to check the capabilities blind command injection on a Linux machine?
Answer: ping
[Câu hỏi 3.3] I will use payload to check the Windows machine to put blind command injection into the?
Answer: timeout

We can avoid this vulnerability with a number of methods, from using potentially harmful functions or libraries in the programming language to filtering input without relying on user input.
Vulnerable functions:
• Exec
• Passthru
• System
In the example below, the program will only accept and process numbers entered into the form.
- This means that commands like “whoami” will not be executed.
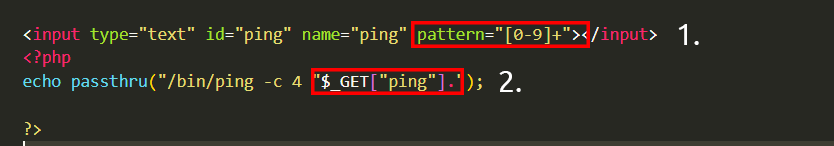
1. The application will only accept a specific character pattern (digits 0-9)
2. The application will then proceed to execute only this data, which is all numeric.
It should be noted that any program that uses these functions without doing a full check is vulnerable command injection.
Filter input:
- This is one of the most effective methods to avoid command injection; it is a process of adjusting the formats or data types that users enter, by restricting the input characters that anyone is allowed to enter.
Eg:
1) Accepts only numeric data
2) Remove any special characters like >, &, and /.
The following image illustrates how to use the PHP function “filter_input” to determine if the data provided via the input form is numeric.
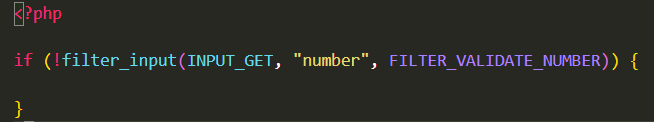
Without using filters:
These filters will limit you to specified payloads; however, we can deprecate these filters by exploiting the logic of the application.
- For example, a program might remove quotation marks ; using the hexadecimal value.
The example below demonstrates that, even if data is provided in a different format than expected, it can still be processed and produce the same result.
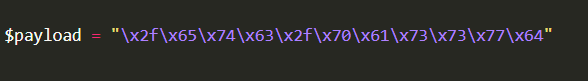
[Câu hỏi 4.1] What is the term for “cleaning” the user input provided to an application?
Answer: sanitisation

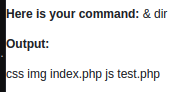
Use “127.0.0.1” for localhost testing.

With the “localhost” test, we discovered a few things.
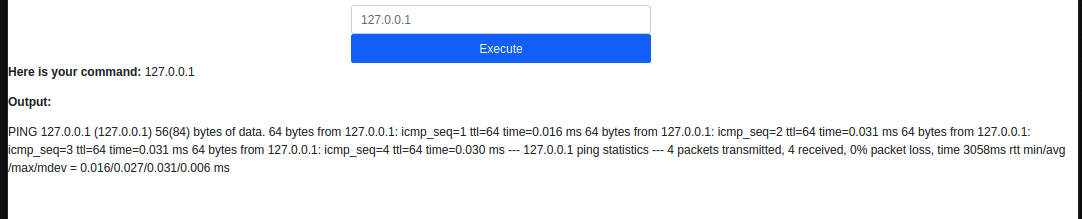
“& Dir” worked, indicating that the victim was using “Windows” and not Linux.
Command Injection Cheatsheet:
– https://github.com/payloadbox/command-injection-payload-list
[Câu hỏi 5.1] What user is this application running as?
Since we know the victim is using “Windows”, we can use the shell operator “&” to find out which application is running.
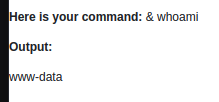
Answer: www-data
[Câu hỏi 5.2] What is the content of the flag in /home/tryhackme/flag.txt?
Because the “&” operator is a vulnerable function and allows us to navigate the directory, and since we can access “dir”, we just need to navigate to flag.

Finally, to read the file, we have to use “cat”, so instead of “dir”, we will use “cat”.
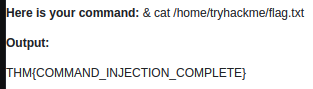
Answer: THM{COMMAND_INJECTION_COMPLETE}
So you already know how dangerous this vulnerability is.