This hack is for educational purposes only, so that new bug hunters can exploit the same method and responsibly disclose security issues to the owners of the site.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

The Covid-19 pandemic has moved everything from offline to online, so schools need a website to manage data related to their students, including their activities, assignments, tuition fees. , points, etc. So I will use the website https://ugtfdxlm.com as an example.
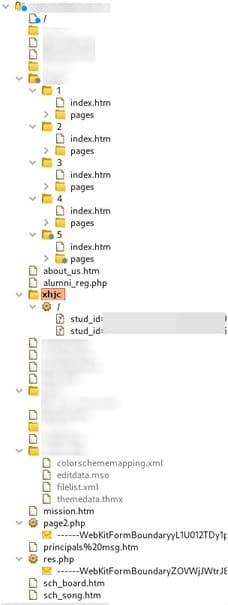
I opened the website and started accessing the various links present on it with burp running in the background. It’s mostly a static site with .html pages so not much can be found in those pages. Eventually, I started using burp to crawl on the domain that displays many of the resources contained in the site. I found some php pages but didn’t have any interesting information.
How I hacked a school’s website
Hole 1
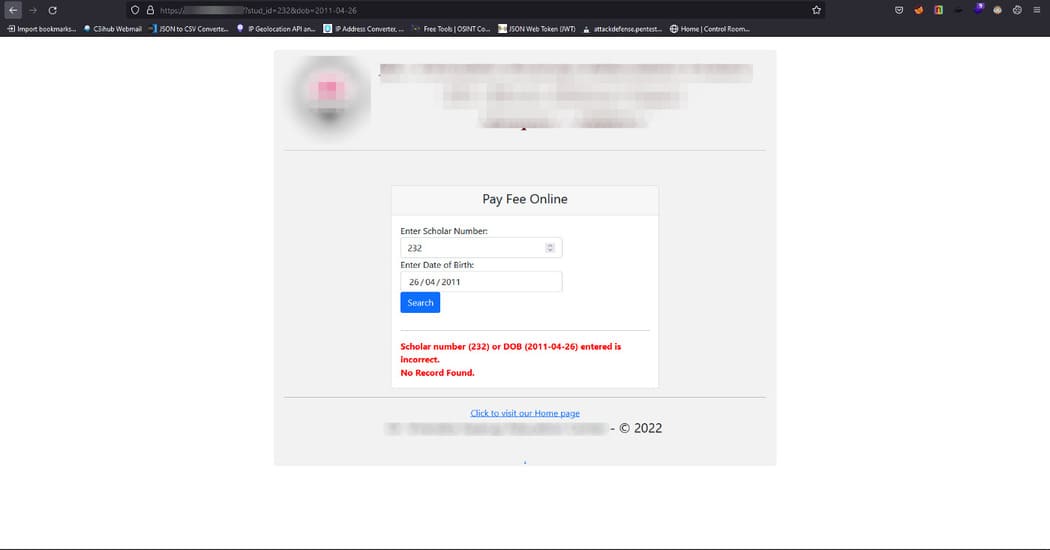
Then I see a subfolder that burp crawler found, such as xhjcso the URI becomes https://ugtfdxlm.com/xhjc. I opened it and there is also a php page whose function is to take the student’s unique admission number and DOB as input and display the tuition details related to that student. This seems to be a vulnerable place. I entered a random admission number and the DOB and submitted it, which throws an error because the numbers are random. But this makes a GET request, for example that request is https://ugtfdxlm.com/xhjc?stud_id=87263&dob=2011–01–23.
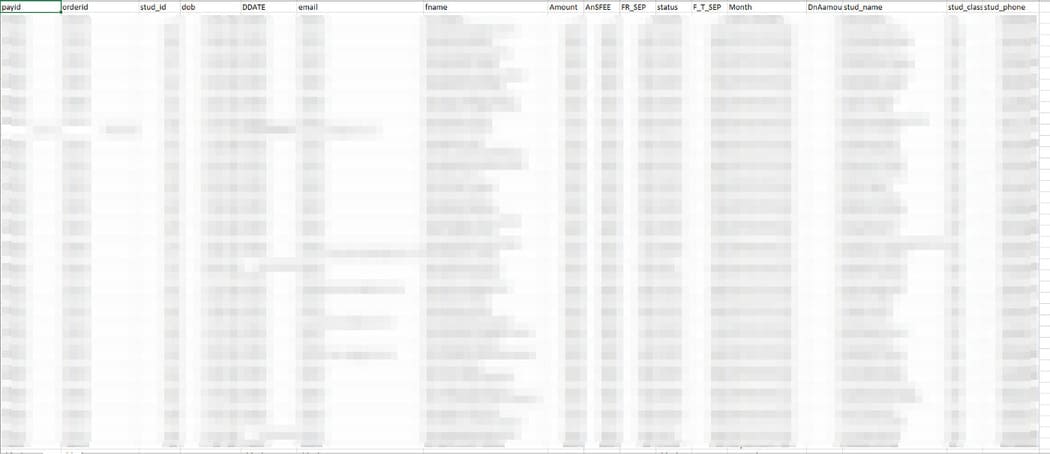
Seeing this type of URL, my instinct tells me to add the calculated payload of SQLi in the request i.e. https://ugtfdxlm.com/xhjc?stud_id=87263’+oR+1=1+#&dob=2011–01–23 and send it. The error is gone and this means the site has the SQLi error. I did a little more digging into it and was able to dump a database of tuition fees for the rest of the students.

The details include sensitive student information such as their admission number, name, father’s name, DOB, mobile number, tuition details, etc.
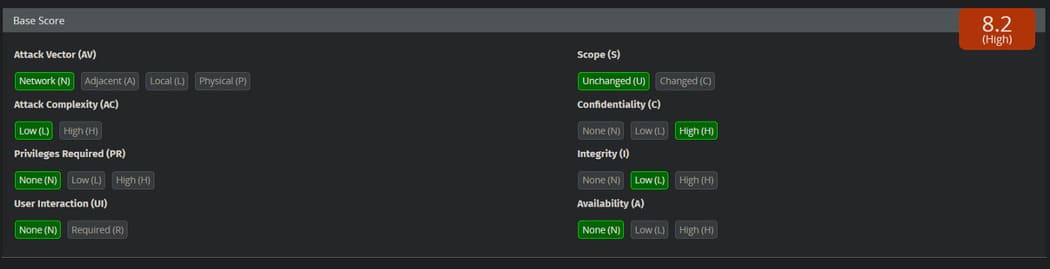
Obviously I will not exploit this vulnerability more because my ethics do not allow and will not abuse this information. But what else can I do with this vulnerability? This is a common question among newbies. With this security hole, I can now upload my own reverse shell payload to the server, execute it, and the whole server will be under my or the hacker’s control. Also, if the user has the privilege of the INSERT INTO command then he can insert new rows or even update the rows, such as making the tuition zero, but all this is unethical. The following is the CVSS score that will be assigned to this vulnerability:
Hole 2
On the same page, I think to add some HTML tags in the GET parameter like https://ugtfdxlm.com/xhjc?stud_id=
HELLO HTMLi
&dob=2011–01–23 and send it.
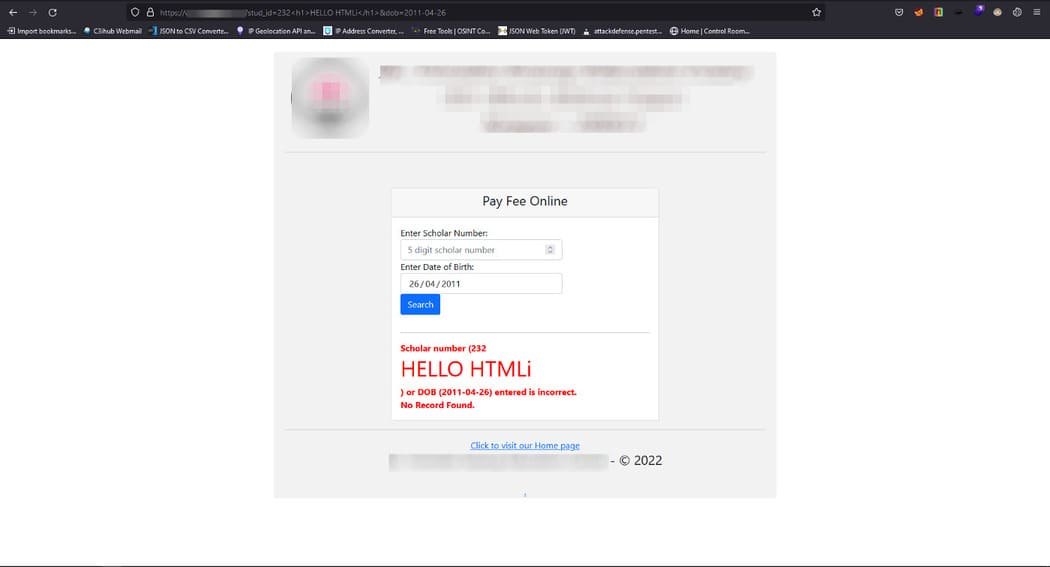
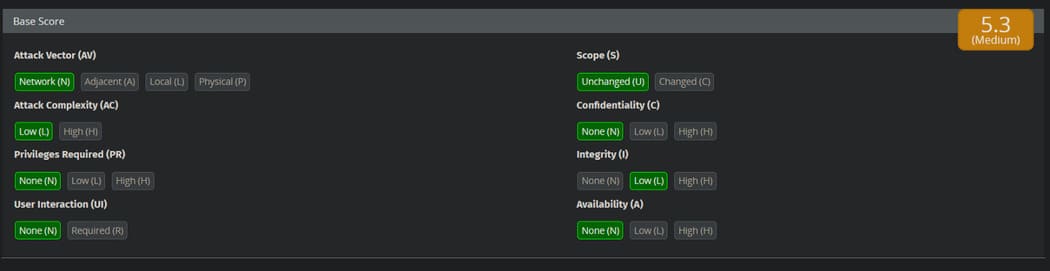
I was able to fake the page content and prove that I can insert HTML into the web page. The following is the CVSS score that will be assigned to this vulnerability:
Vulnerability 3
Since the URL https://ugtfdxlm.com/xhjc?stud_id=87263&dob=2011–01–23 accepts tokens, it is also vulnerable to XSS vulnerabilities. The URL will become https://ugtfdxlm.com/xhjc?stud_id=&dob=2011–01–23.
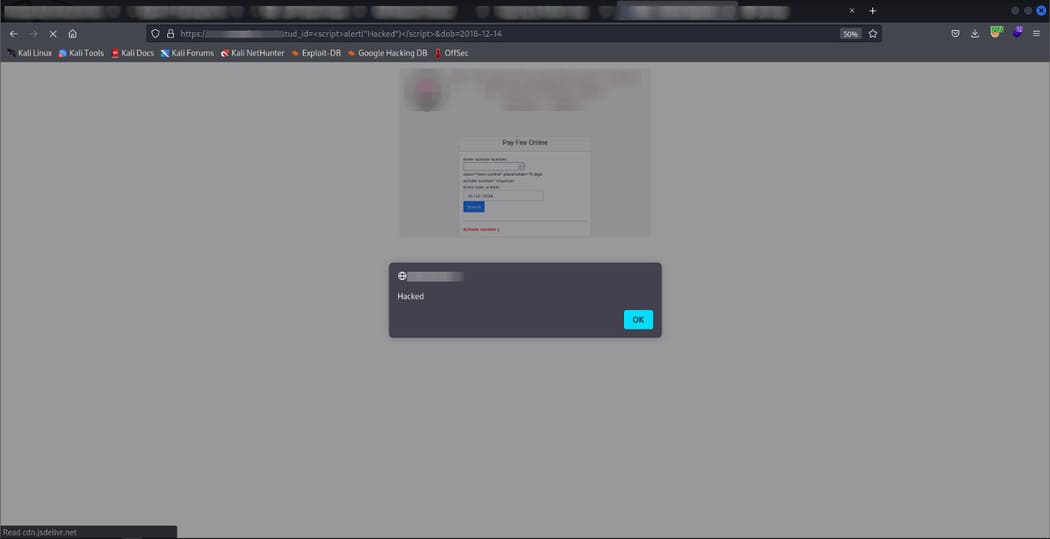
Hackers can use this vulnerability to add their own form asking for DOB and number of students for admission and upon submitting the application, the hacker can get those details in the server using javascript. The URL could be sent to the parents and they could fall victim to a scam. That’s why HTMLi and XSS are also critical vulnerabilities. A CVSS score will be assigned to this vulnerability:
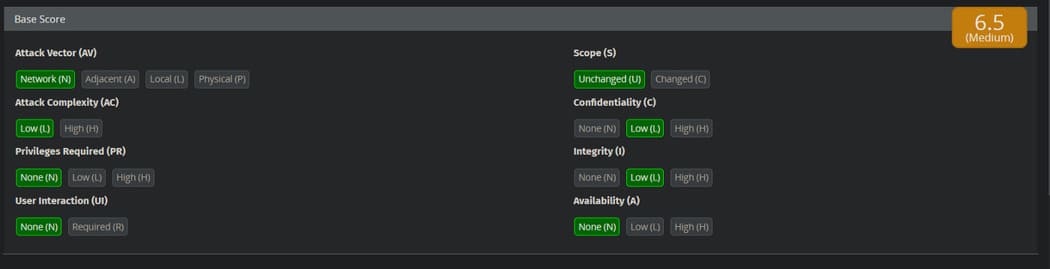
Vulnerability 4
Since I have found all possible vulnerabilities related to URL GET request, there are no other holes to test on cz domain other pages are static. And since this is a basic website, so there is a chance that there will be an error/misconfiguration on the site, I tested the Click jacking feature on the site. And it actually works cz the X-frame header is missing.
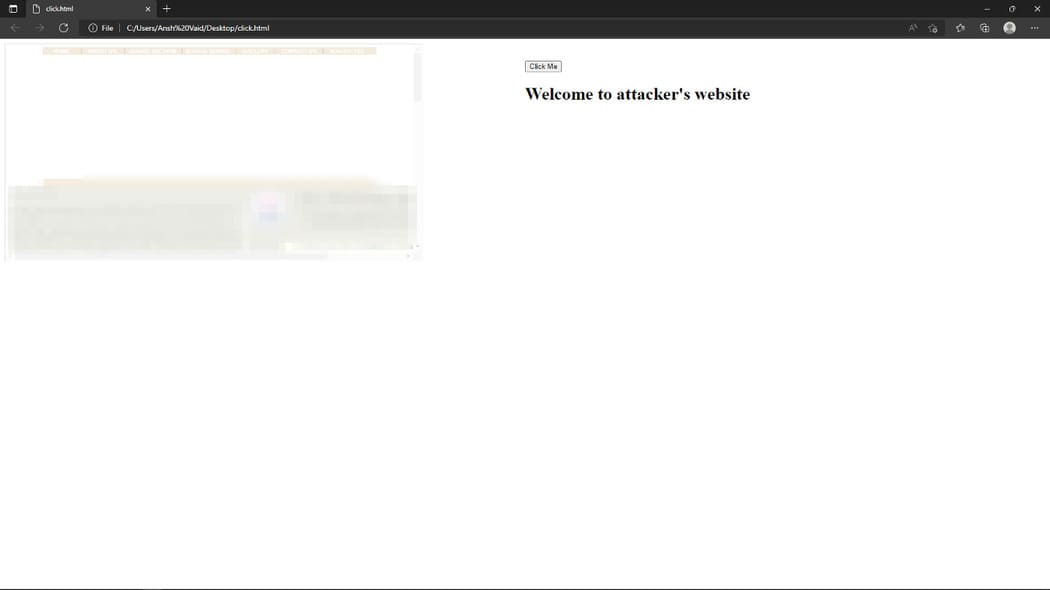
After I found these vulnerabilities, I wrote them an email, which was in the contact section of the website explaining to them the severity of these vulnerabilities, but they didn’t reply back, otherwise I helped them patch these vulnerabilities. The database that I received has sensitive information, hackers can also use this information for fraudulent purposes because most parents don’t know much about cyber security.
Anyway, I just wanted to share that anything in the public domain that is vulnerable to hacking is high risk, you never know what information could be misused in what way.
In addition, schools should also be aware of the severity of this type of data that is vulnerable to hacking, and should be equipped with more knowledge about cybersecurity.











