CMSeeK is a toolkit written on Python platform that helps to scan the security holes of famous CMS such as: WordPress, Joomla, Drupal… and more than 150 other CMS. CMS is a content management system that helps create and modify digital content. The content is created and managed by CMS such as news, newspapers, images, videos. It can be said that today’s websites are built on a lot of open source CMSs. Not only news, but also personal blogs choose the solution using CMS for easy operation and management. The main functions of CMS include:
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
- Create, store, edit content
- Upload and Download content
- Search for content.
- User Permissions
Because CMS is open source, there may be security holes, leading to Hackers exploiting this vulnerability to take control of the Website. Besides, there are also security errors due to the user’s administration. Therefore, the CMSeeK tool will help you scan and point out the security weaknesses of CMS-using Websites. From there you can patch yourself or practice Hack into someone else’s system.
CMSeeK v1.1.1 – Vulnerability Scanner for WordPress, Joomla, Drupal and 150+ CMS
Functions of CMSeeK
Identify more than 155 basic CMS
Detect Drupal versions
Advanced WordPress Vulnerability Scan:
- Version detection
- User List
- List Plugins
- List of themes (Themes)
- User detection (3 detection methods)
- Look for vulnerabilities in the version in use…
Advanced Joomla Vulnerability Scan:
- Version detection
- Backup file finder
- Admin page finder
- Detect security holes
- Check directory listing
- Leak detection configuration
System of Modules that support Bruteforce:
- Use the available bruteforce attack modules or create your own.
Requirements and Compatibility:
CMSeeK is built with python3. You will need python3 to run this tool and can be compatible with current Linux systems (Ubuntu, Redhat, Kali Linux, Centos…). CMSeeK is not yet fully supported on Windows. CMSeeK relies on git for automatic updates, so please install git before use
How to use CMSeeK v1.1.1 to scan for vulnerabilities of WordPress, Joomla, Drupal and 150+ CMS
After scanning the entire Website, CMSeeK will show targets with security errors. Attached is a link to instructions to exploit those errors. To perform step-by-step installation and use, follow these steps:
Install CMSeek
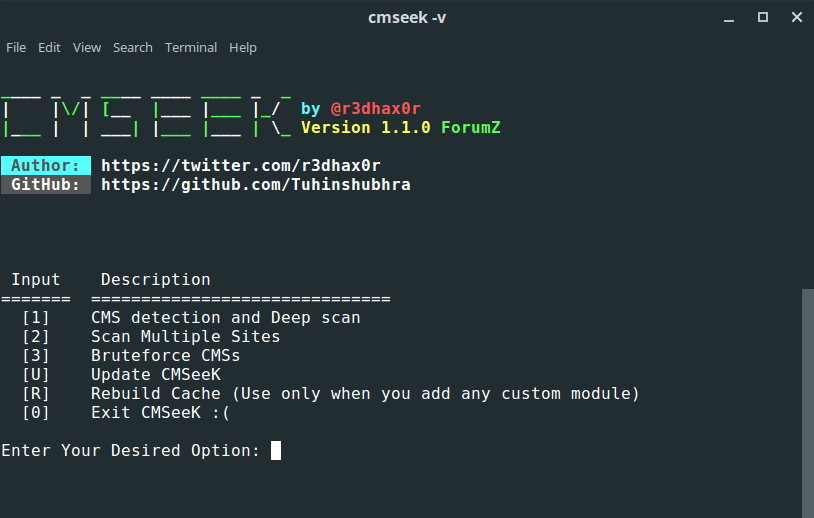
Using CMSeeK is pretty easy, just make sure you have it installed python3 and gitand use the following commands:
View CMSeek commands instructions with the command:
Check for updates:
You can check for updates from the main menu or use the command: python3 cmseek.py --update to check for updates automatically.
Vulnerability attack method:
Use the command below to scan your website for vulnerabilities:
python3 cmseek.py -u <target_url> [...]
(
Eg: python3 cmseek.py -u https://abc.com
CMSeek detects CMS through the following steps:
- HTTP Headers
- Meta tag generator
- Page source code
- robots.txt
CMSeeK can currently detect 157 CMSs. Check the list in file cmss.py contained in the mseekdb directory. The list of cms is stored in the following way:
cmsID = {
'name':'Tên của CMS',
'url':'Trang chủ của CMS',
'vd':'Phiên bản có thể Quét lỗi (0 for no, 1 for yes)',
'deeps':'Deep Scan (0 for no 1 for yes)'
}
Scan results:
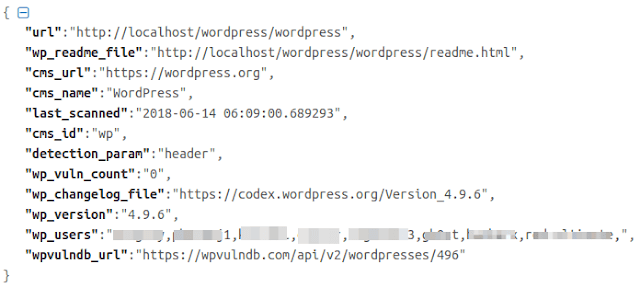
All scan results are stored in a json file named cms.jsonyou can also find the logs in the directory Result\<Website được quét>. Result Bruteforce stored in txt file in the same directory.
Here is an example of a Website json error scan log:
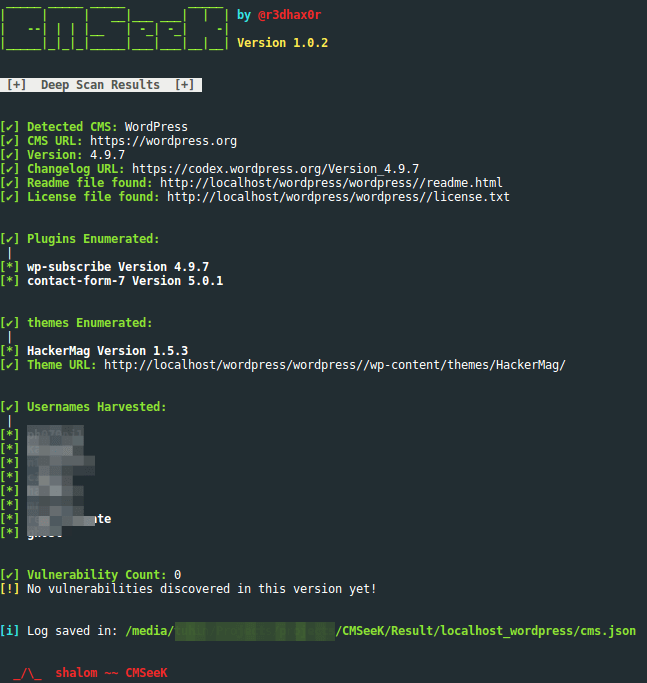
An example of the WordPress vulnerability scan results:
Module Bruteforce – Exhaustive attack
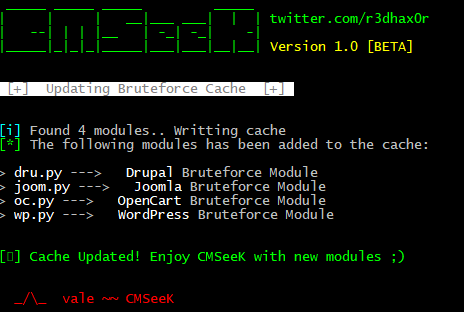
CMSeek has a Bruteforce Module function. Which means you can add your own custom Bruteforce Modules. REMOVEYou need to follow these steps:
- Add a comment to help CMSeeK know the name of the CMS using regex. Eg:
#<Name Of The CMS> Bruteforce module - Add another comment
### cmseekbruteforcemoduleto help CMSeeK know it’s a Module. - Copy and Paste the Module into the folder
brutecmsby CMSeeK. - Start up CMSeeK and clear Cache with command
Uon the Menu.
- If done correctly, you will see the output as shown below and the new Module will be listed in the Bruteforce menu when you open CMSeeK.