.ics is the extension of the calendar file, when opening this file it will integrate the calendars, calendar notes into the device. If Currently many Hackers take advantage of .ics to attack phishing. Recently while checking out Google Calendar, I noticed that .ics files can be abused in a way that they have never been used before. This technique allows you to create meetings on Calendar with fake organizers and attendees.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

Isc . file compatibility
I discovered that this technique will work on all the most popular email service providers (e.g. Google Workspace, O365), if opened on Android or iOS it will integrate into the phone’s Calendar. But it works better on Google targets due to the way Google displays .ics attachments. Therefore, the illustration below will only target Google.
Attack Procedure
Can understand the process of attacking with ics file like this, Hacker will trick you to open the ics file, and then scheduled content such as meetings, notes will be integrated into the Calendar on your device, When the date/month is scheduled it will show a notification and when you open the notification it will redirect to a malicious Web page or download malicious code to your computer.
Download the .ics template
The easiest way to download an .ics file is to create a Google Calendar invite from one Gmail account to another and then download the email attachment. invite.ics.
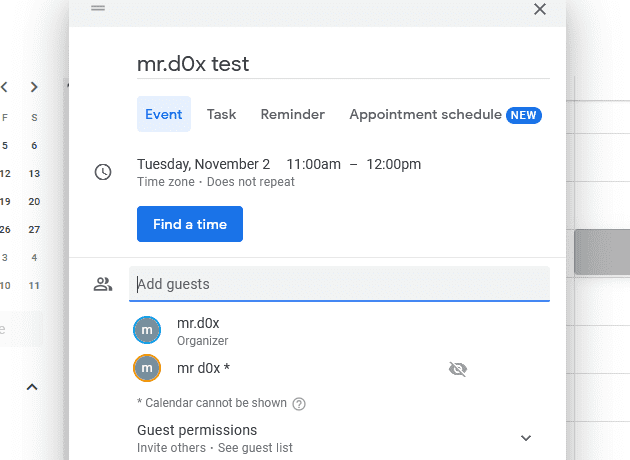
Sign in to the other email, click on the email invitation, and download the invite.ics file.

Now we have the .ics file to fake it.
Fake
Open the invite.ics file with a text editor. You will see each line in key: value format. Remove the line starting with the UID.
# Xóa dòng này
UID:[email protected]Now you can start spoofing contacts. The organizer can be tampered with by modifying the value CN= as below.
ORGANIZER;[email protected]:mailto:[email protected]
For attendees, you can add as many as you like and modify the value again CN= and that’s the email the user will see.
ATTENDEE;CUTYPE=INDIVIDUAL;ROLE=REQ-PARTICIPANT;PARTSTAT=NEEDS-ACTION;RSVP=TRUE;[email protected];X-NUM-GUESTS=0:mailto:[email protected]
Force attendees to accept the invitation
All attendees have a PARTSTAT= key. Just set it to PARTSTAT=ACCEPTED, and it will appear as if attendees have accepted the invitation.
Add profile photo
The attendee’s mailto: address can be another email you own or a random email. The perk of using an email you own is that you can log into that account and upload the profile picture of the person you want to impersonate.
For example, if one of the attendees has [email protected] and mailto:[email protected]. I can upload Johnathan’s photo to [email protected] and that’s what the user will see in the invitation.
Important Note
Make sure the organizer’s mailto: address is a non-Google email (not Gmail or Google Workspace). For some reason if it is a Google email, the “Yes/Maybe/No” buttons are not included in the email. For this example, I will use a Hotmail account.
Calendar title and time
You can change the calendar title by modifying the Summary: key in the .ics file.
You can modify the time with DTSTART: and DTEND:.
Process Summary
I’ll summarize the steps in case you can’t figure it out. I’m assuming I’ve downloaded the invite.ics file.
Step 1
Remove the line starting with the UID in the .ics file.
Step 2
Fool the organizers and attendees by modifying the CN= and mailto: values. Make sure the organizer’s mailto: value is a non-Google email. Also make sure you set PARTSTAT = ACCEPTED for all attendees except the victim.
ORGANIZER;[email protected]:mailto:[email protected]
ATTENDEE;CUTYPE=INDIVIDUAL;ROLE=REQ-PARTICIPANT;PARTSTAT=NEEDS-ACTION;RSVP=
TRUE;[email protected];X-NUM-GUESTS=0:mailto:[email protected]
ATTENDEE;CUTYPE=INDIVIDUAL;ROLE=REQ-PARTICIPANT;PARTSTAT=ACCEPTED;RSVP=
TRUE;[email protected];X-NUM-GUESTS=0:mailto:[email protected]
ATTENDEE;CUTYPE=INDIVIDUAL;ROLE=REQ-PARTICIPANT;PARTSTAT=ACCEPTED;RSVP=
TRUE;[email protected];X-NUM-GUESTS=0:mailto:[email protected]Step 3
Modify the Calendar title to whatever name you want.
SUMMARY:Mandatory Company Townhall MeetingStep 4
Make sure you have set the time of the invite schedule correctly. The times shown below are 2021-11-02 12 noon – 1pm.
DTSTART:20211102T160000Z
DTEND:20211102T170000ZStep 5
Compose an email to the victim and attach the .ics file. The email header format should be as follows:
Invitation: CALENDAR-TITLE-HERE @ Wed Nov 2, 2021 12pm - 1pm (EDT) ([email protected])Step 6 – Options
Add the Google Meet link to the email body because Google splits the Google Meet link in the .ics file.
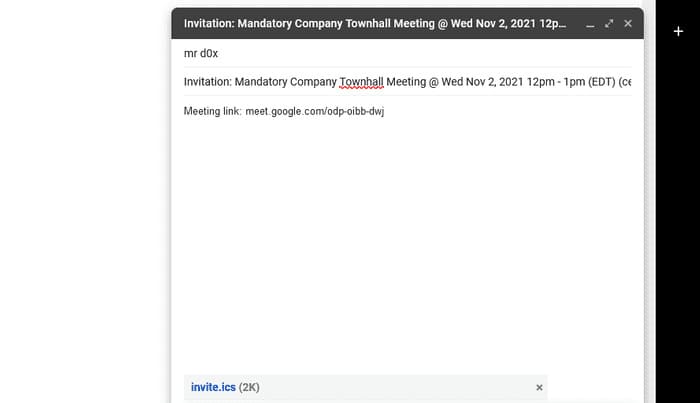
Result
As expected, users see the fake names you have recorded.
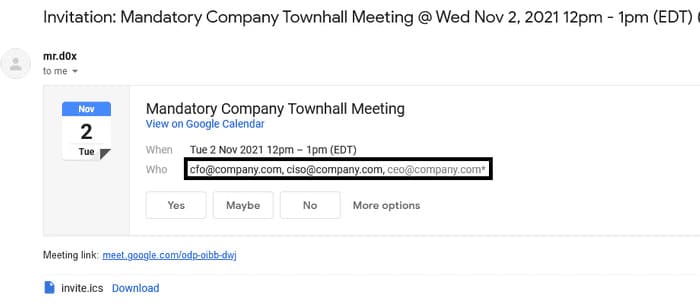
And both fake users accepted the meeting.
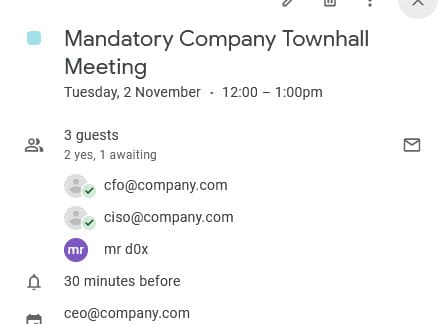
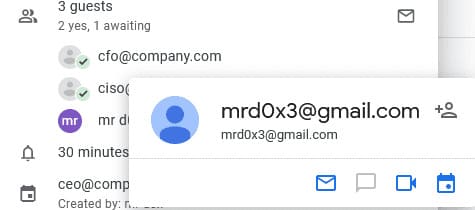
By hovering over the names on Google Calendar, mailto:email will appear, so try to set it to an address that closely resembles the fake email.
Example: [email protected] and mailto: [email protected]
Alternatively, you can also create meeting notes using Google Calendar here.











