In this article, I will guide you step by step, i.e. from downloading the sample firmware and then analyzing it to find the answer. You can follow along and answer questions here.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

Prepare
The first and foremost thing is to find a router firmware that needs to be analyzed. In this case, we have been provided with the target, so we will download the firmware to the Linux machine.
We need to download the Linksys WRT1900ACS V2 firmware. You can download this firmware here.
Once downloaded, you can run the ‘file’ command to search for basic information about the file.
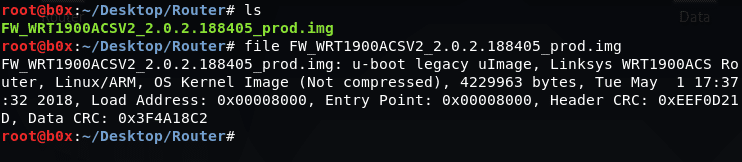
We can see that this is ‘u-boot legacy uImage’ and is the firmware of Linksys WRT1900ACS Router based on Linux/ARM.
Now that we’ve finished gathering the basics, we’re ready to go – Authorization. firmware investigation.
Start the investigation
An important tool here is the ‘string’ command. It gives us all the basic (English-accredited) string information it can find in the file’s binary. Run the command and see what we can find.
There are a huge number of strings to be found here, you need to save them to a text file for easier analysis.
![]()
Use the less command to view the first few lines of the file.
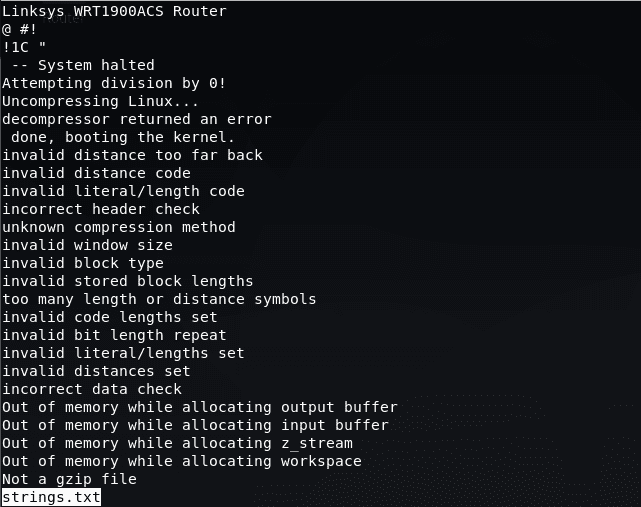
The first line needs attention because it gives us information about this firmware and the router on which it was created. Now we will find the operating system. We can print the whole file and search with the ‘grep’ command.
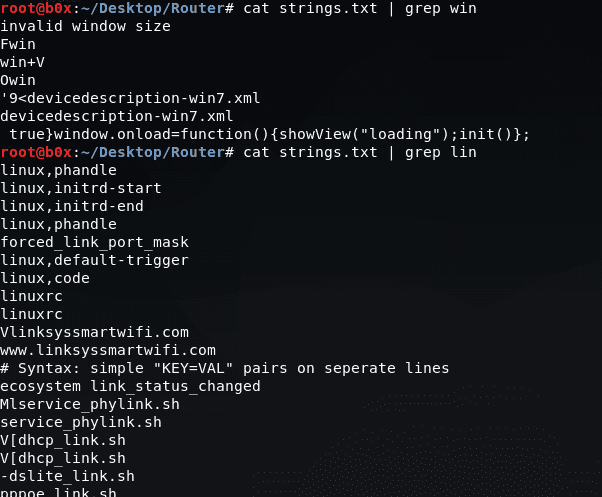
Based on the above results, we are definitely Linux operating system. We can see in the image above there are several folders listed.
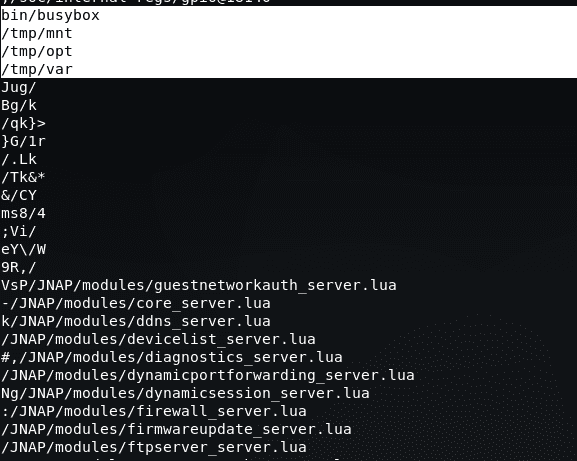
Now we have an overview. We need to unzip the firmware. To extract the firmware, I will use “BinWalk”.
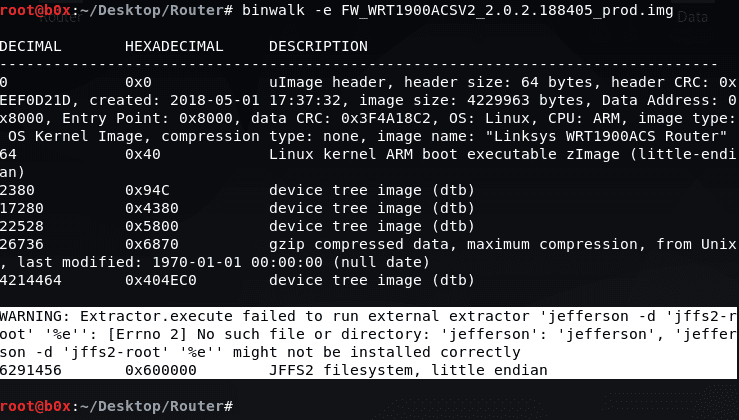
We get an error and binwalk cannot extract the file system. This is because binwalk does not support JFFS2. First we need to set it up. Execute the following commands:
sudo pip install cstruct git clone https://github.com/sviehb/jefferson cd jefferson python setup.py install
After successful installation let’s run binwalk again and now we can see that binwalk has identified the file system as JFFS2.
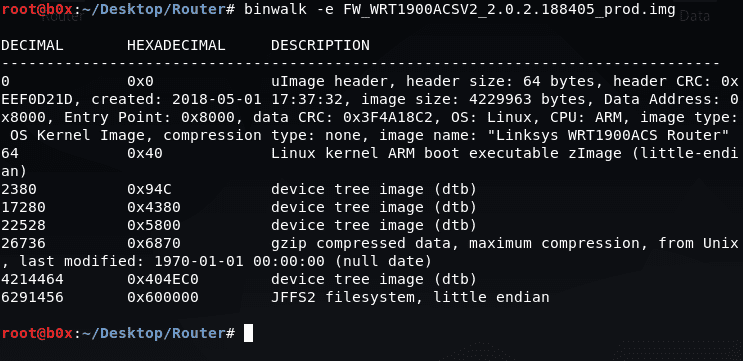
Now we have a lot of information regarding firmware. Title size, image size, CRC check, last created date, OS details, CPU it runs on, etc.
Binwalk creates a separate directory for the data it extracts.
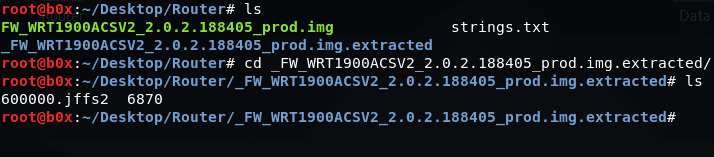
We can see that there is a file showing the JFFS2 filesystem and the other a gzip file. Running the file will output 6870 and no other data. This means that binwalk has misinterpreted the data, we can rerun binwalk on the file to look for other possibilities to try and extract the data in the correct format.
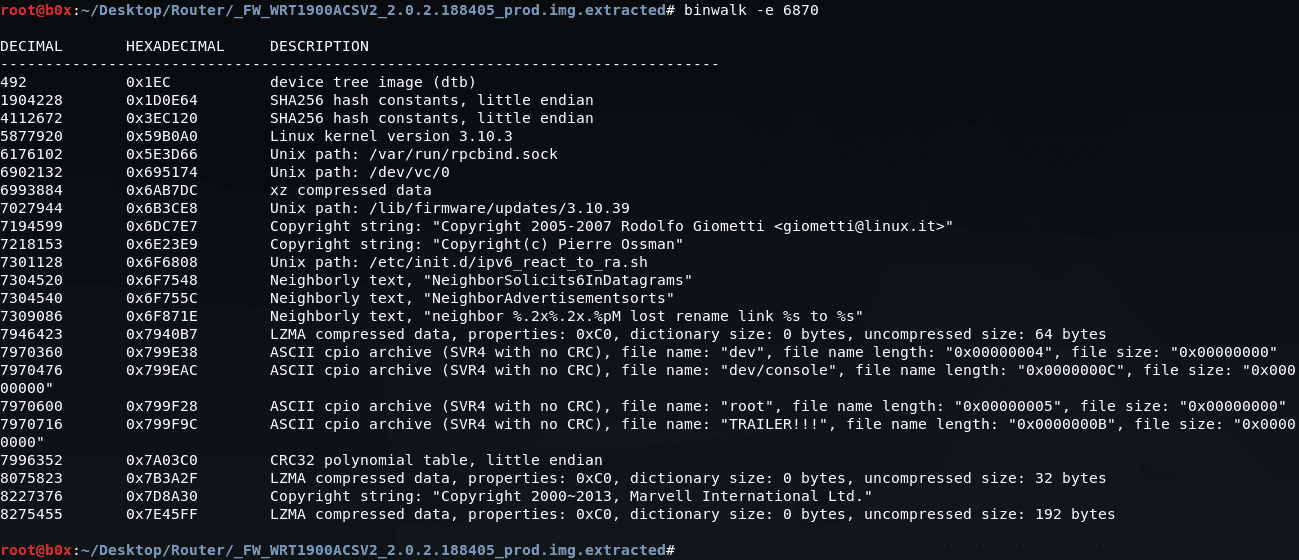
We can see that this file contains a copy of a real Linux kernel; binwalk also shows us the version on which this kernel works. We can also see some LZMA compressed data and some cpio cached data.
The next step is to mount the firmware to further analyze this part.
Mounting
First, we need to create a “Block Device”. It can be done using the command:
mknod /dev/mtdblock0 b 31 0Then we need to create a directory to push our filesystem to with the command:
mkdir /mnt/jffs2_file/Firmware requires some kernel modules. So we need to load them all to make sure that the filesystem is working properly. You can use the following commands:
modprobe jffs2
modprobe mtdram
modprobe mtdblockNow we need to write the image to “Block Device” and it can be done with the command:
dd if=/root/Router/600000.jffs2 of=/dev/mtdblock0Next, we need to mount the filesystem with the command:
mount -t jffs2 /dev/mtdblock0 /mnt/jffs2_file/Finally, we will access the mounted filesystem with the command:
cd /mnt/jffs2_file/Once all is done, execute the ls command to display the directories. We just mounted this firmware to local :v.
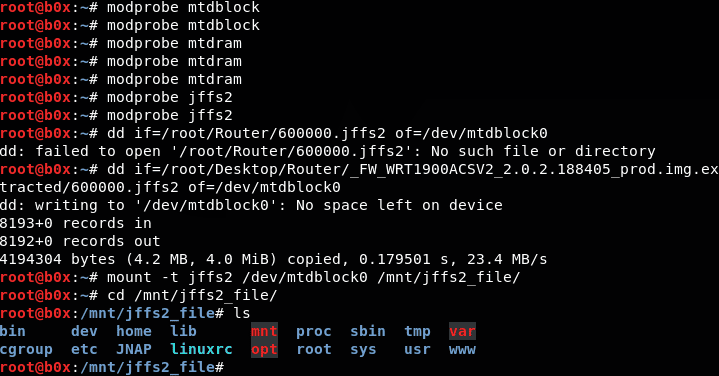
When listing all the files, we can see that some files are being symlinked to other locations. In essence, some files have ‘shortcuts’ to others elsewhere on the file system.
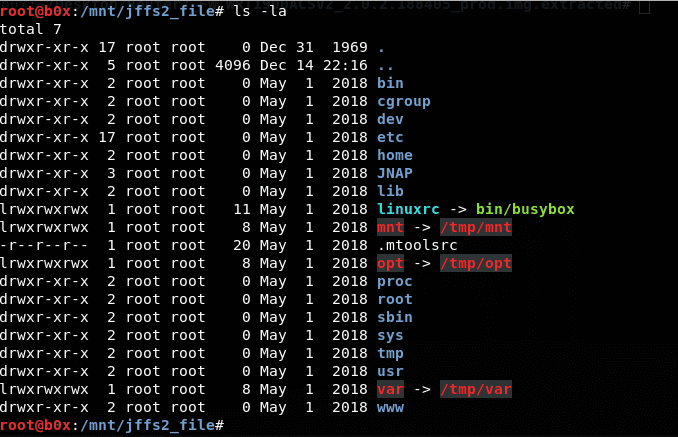
In addition, we can see that there are three parent directories associated with the /tmp/ directory. We can also see the /www/ directory, this is where the web application data will be stored.
Take a look in the bin directory:
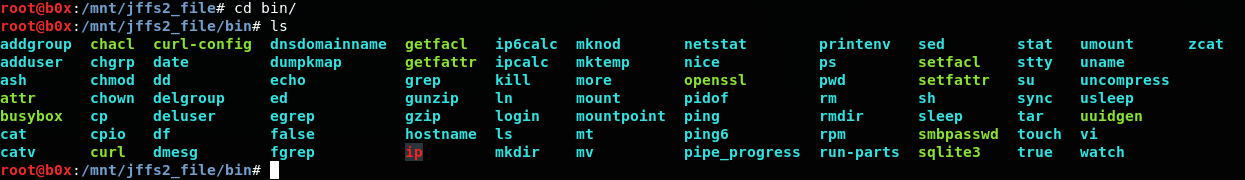
We can see that the database is “sqlite3”.
Now let’s see what’s inside the etc folder.
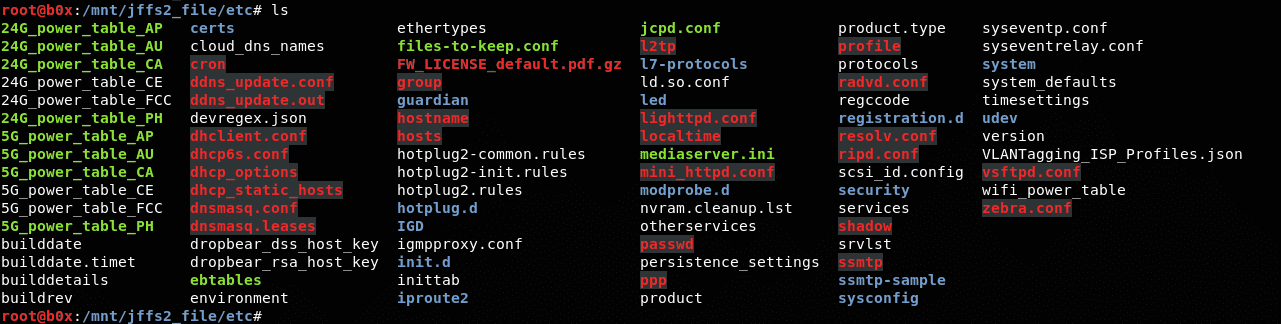
There are a lot of configuration files here, along with a lot of data. Take a look at the thebuilddate. I wonder what this file can do???
![]()
There are also RSA keys here and we can see that the SSH server being used here is “dropbear”.
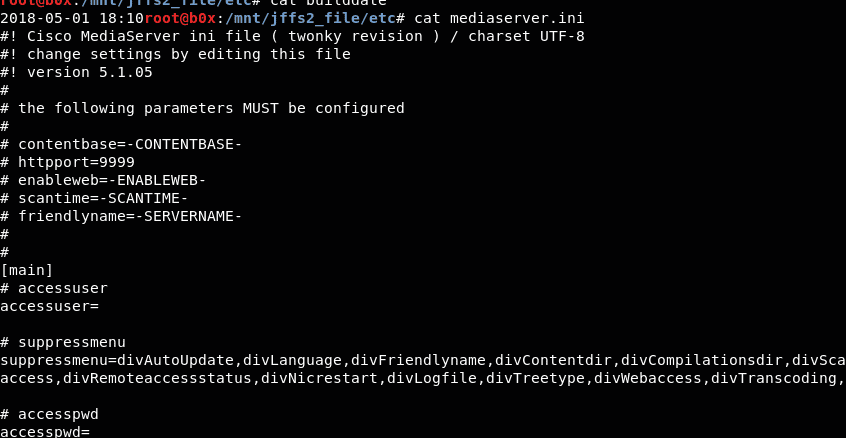
Interestingly, there are intermediate server data also displayed here. Further inspection shows that this is from Cisco.
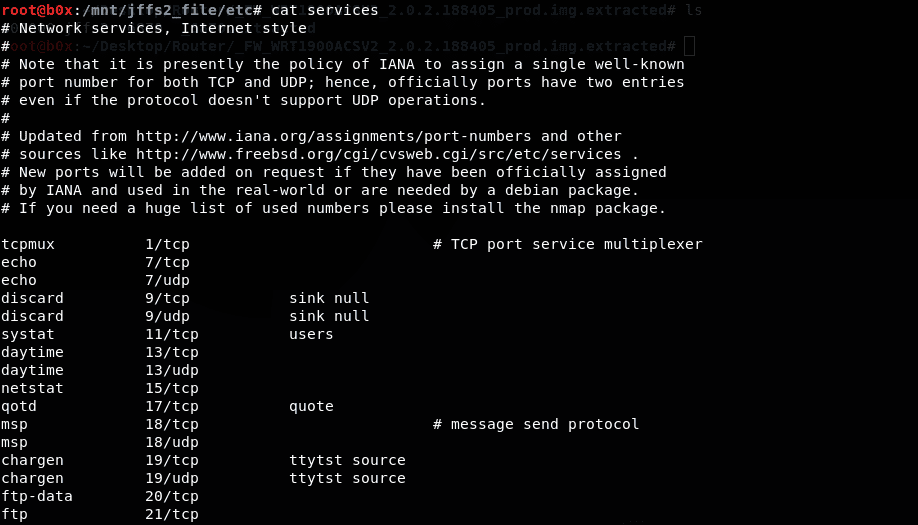
Take a look at the other service files for more information regarding the protocols used and their assigned port numbers.
There is another file called “system_defaults” which contains all the default settings for the router.
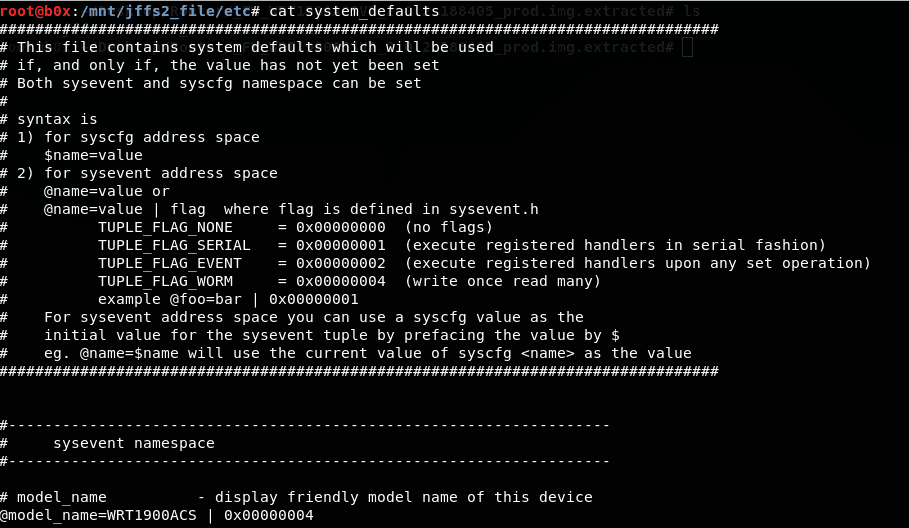
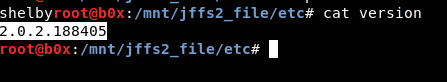
There is a file containing the firmware version.
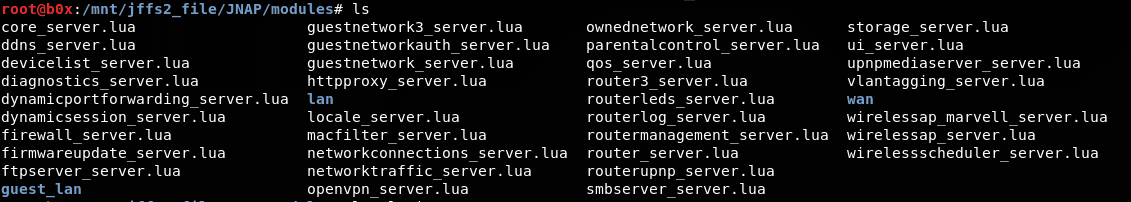
There is a folder called JNAP that contains lua scripts. These scripts are used to control the network.
This is a very quick summary of router firmware analysis. In addition, you can also see more rooms to practice hacking on tryhackme here.