What is SSH? Secure Shell (SSH) is a network cryptographic protocol that enables secure communication over an insecure network. This protocol was developed to replace insecure old protocols, increasing security and privacy on all operating systems.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

What is SSH?
SSH stands for Secure Shell and is also known as Secure Socket Shell.
SSH is a secure connection network protocol. This protocol is mainly used by network administrators to connect to remote devices securely, but SSH also has a bunch of common functions.
Before SSH was developed, users and administrators often used insecure network protocols, such as Telnet, to communicate with remote devices. These now obsolete protocols send important information like passwords and logins in plaintext, making them vulnerable targets.
SSH usually communicates over port 22.
Difference between SSH1 and SSH2
There are two versions of SSH. I say “two” because between those two versions, there have been many additions and updates from SSH1 to SSH2.
As you guessed, SSH2 is the more secure protocol. It provides better protection against attackers and eavesdroppers, supports stronger encryption algorithms, and makes a ton of general improvements over the original SSH protocol.
What is OpenSSH?
OpenSSH is a widely used open source version of SSH. The original free version of SSH was developed by Tatu Ylönen. Later versions of Ylönen are proprietary, which means it costs money to license and use, and you cannot make unauthorized changes to the protocol.
As a result, a group of developers ripped off the original free version of SSH and named it OpenSSH, which is now developed as part of OpenBSD (an open source operating system). All major operating systems, such as Windows, macOS, and many Linux distributions, support OpenSSH.
How does SSH work?
To understand how SSH works, you need to understand two things.
First, what is a shell? Second, how does a public key work? Let’s find out what a shell actually is before diving deeper into the details of an SSH connection.
What is Shell?
A shell is a piece of software that allows you to communicate with the operating system that is hosting it. Typically, you use commands to interact with the shell, although graphical user interfaces (GUIs) exist.
Another important thing is that you don’t have to sit in front of the computer to use the shell. You can operate a remote shell over a network connection using SSH.
What is public key?
In modern computers, there are two main types of encryption:
- Symmetrical Algorithm: Use the same key for both encryption and decryption. Both parties must agree on the key of the algorithm before communication begins.
- Asymmetric algorithm: Use two different keys: a public key and a private key. This allows encryption to be more secure when communicating without having to set up an algorithm first.
SSH is a type of public-key cryptography, which uses both types of encryption to create a secure connection in a client-server model. When the client tries to make a connection with the server, each party communicates through separate encryption protocols.

After resolving a suitable encryption protocol, the client and server use the Diffie-Hellman Key Exchange Algorithm to arrive at a shared encryption key as part of the symmetric algorithm. This encryption key remains a secret throughout the connection and is used to encrypt all communications between the two parties.
So, where is the asymmetric encryption feature?
In public key cryptography, you have two keys: public key and private key. You can send the public key to someone else, and the person to whom you send the public key only knows the private key. Together, they form a pair.
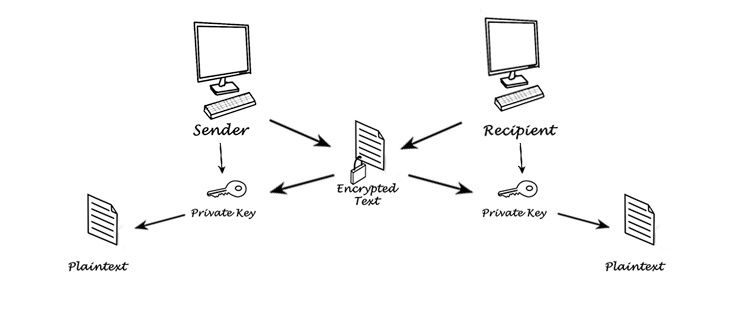
Before a symmetric key exchange takes place and a secure communication channel is established, SSH uses asymmetric encryption to generate a temporary key pair. The client and server exchange public keys, authenticating each other before the symmetric key generation process begins.
What encryption algorithm does SSH use?
Because SSH uses symmetric encryption to secure your connection, you can configure SSH to use a variety of symmetric encryption algorithms such as AES, Blowfish, Twofish, Salsa20/ChaCha20, 3DES, IDEA ….
Is SSH the same as SSL/TLS?
While both SSH and SSL/TLS previously provided security for insecure network protocols, SSH and SSL/TLS are not the same thing.
Secure Sockets Layer (SSL) and its successor, Transport Layer Secure (TLS), provide an encrypted communication tunnel. You use TLS every day when you send email or browse the web. SSL and TLS are application layer protocols. In internet communication networks, the application layer standardizes communications for end-user services.
While both SSL/TLS and SSH provide encryption, the network protocols themselves are designed for different purposes. SSL/TLS is designed to protect your data connection, while SSH is designed to let you securely access remote computers and execute commands.
However, you can use SSH in combination with SSL to transfer files, using SSH File Transfer Protocol (SFTP) or Secure Copy Protocol (SCP). Incidentally, you can too use SCP to copy data from my PC to Raspberry Pi.
Is SSH the same as VPN?
Like the question above, a Virtual Private Network (VPN) also provides an encrypted tunnel for your communication. But while SSH provides a secure connection in a client-server configuration to a specific computer, a VPN provides a secure connection between your computer and the VPN server.
You cannot execute remote commands on the VPN server. Instead, when you turn on a VPN, data transmissions to and from your computer go through an encrypted tunnel to the VPN server before going out onto the internet.
So SSH allows a secure connection to a computer to execute remote commands, while a VPN provides an encrypted tunnel of data between your computer and the VPN server.
This process can hide your computer’s location and add some security when using an internet connection. You can read this paragraph to get a better idea of how VPNs work.
On which platforms is SSH available?
As long as the operating system you are using has an SSH client or built-in SSH functionality, this secure network protocol should be available to you.