The term Brute Force has been mentioned a lot recently after Hieu PC attacked a fake website with a Brute Force Attack form, to log into cPanel – the tool that hosts and manages that fake website. Today we will learn what Brute Force Attack is and How to prevent it.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
Unlike many other tactics used by Hackers, attacks Brute Force do not rely on the site’s security holes. Instead, these attacks rely on users having weak or predictable credentials. Simple attacks and defined targets make attacks Brute Force very popular.
What is Brute Force Attack?
Brute Force attack occurs when a hacker tries to try each password to see if it can log in. These attacks typically involve multiple attempts at the account password in the hopes that one of them will be valid. It’s a bit like you’re having a bunch of keys and trying to lock them one by one, but on a much larger scale.
Passwords aren’t the only resources that can be vulnerable to this type of attack: Links and directories, usernames, and emails are other common targets.
What is the purpose of Brute Force attack?
The goal of a Brute Force attack is to gain access to a restricted resource for other users. This could be for an admin account, a password protected site, or simply for listing valid emails on a certain website.
Having access to a valid account can mean that you are the owner of that Website, free to change, edit or even delete the Website.
How does Brute Force attack work?
The most common type of brute force attack is dictionary attack using a common username and password to try to gain access to the admin account.
Typically, generic dictionary attacks will try to log in with the most commonly used credentials, such as “admin” and “123456”.
How do you know if you are suffering from Brute Force?
Basically, if someone is trying to log into an account repeatedly and fails, it could be a Brute Force attack.
Signs may include:
- Same IP address fails when trying to login multiple times.
- Many different IP addresses trying to login to one account failed.
- Multiple failed login attempts from different IP addresses within a short period of time.
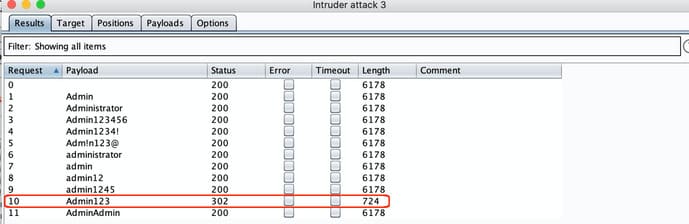
Brute Force Attack Example
Possible brute force attacks add you to the botnet to expose you to DDoS attacks. Hack attack Brute Force after having login information to change the Website interface.
Gaining access to an admin account on a website is like exploiting a critical vulnerability. Hackers will try to profit from accesssuch as by adding spam, spreading malware, or phishing to keep victims unsuspecting.
Brute Force Attack Types
Basically, Brute Force is an act of trying many combinations, but there are many variations of this type of attack to increase the success rate. These are the most common:
Simple Brute Force Attack
A generic Brute Force attack can use different methods, such as repeating all possible passwords at once. This is often used on weakly secure websites where there is no limit on the number of incorrect entries.
Dictionary Attack
This attack uses a list of common passwords instead of random access, builds a “dictionary” of possible passwords, and repeats them. Using a good password list can help improve the hacker’s success rate, but these attacks require time, and the number of passwords in the dictionary you have.
If you have ever Hacked Wifi WPA2, you must have used a dictionary to detect Passwifi.
Hybrid Brute Force Attack
A hybrid attack uses both a dictionary attack and a regular repetition attack. Instead of trying literally all passwords, it will make modifications small for dictionary words, such as adding numbers or changing letters.
Credential stuffing
With the increasing amount of user/password data exposed by weakly secure websites, using multiple accounts using the same password makes it easier for accounts to be hacked.
Once the Hacker has a hacked database of Website A, they can easily use the collected login information to access Website B, if the users share the same user/password.
Therefore, regularly changing the password, and not sharing the same password for the account is a regular thing to do.
How to prevent Brute Force attack
Since Brute Force attacks are not a security hole, updating the software is not enough to protect yourself. Here are some common methods to prevent these attacks:
Use strong passwords
Brute force relies on weak passwords. Strong passwords have the following characteristics:
Only : You should avoid reusing passwords, as websites are compromised and passwords will be exposed. By reusing passwords, Hackers can more easily target you with your compromised credentials on other websites.
Long : Longer password means more combinations. A five-character password is easy to crack on any computer in seconds, 10 characters will take years, and 50 characters will take almost forever.
Hard to guess: Pieces of information like your own name or the city where you live can make passwords easier to remember, but also easier to guess if someone gets any information about you. The same goes for regular text, such as “12345” or “password,” which is commonly used in logins, because they are easy to remember.
With these characteristics in place, Brute Force attempts will fail to guess your password.
The same principles apply to recovery questions: If your recovery questions are weak but your password is strong, it’s much easier for an attacker to reset your password instead of guessing it.
Do not reveal the login link
The requirement for brute force attacks is to submit credentials. If you change the login page address – for example, switch from /login.php luxurious /anonyviet-login this may be enough to prevent most automated tools and batches from sniffing passwords.
However, advanced attacks or public forum pages require a URL for members to log in
Limit the number of wrong login attempts
Brute Force attacks are based on trying multiple passwords and accounts. By limiting the number of logins per user, Hackers won’t be able to try multiple passwords
A common way to limit login attempts is to temporarily ban an IP from logging in after five unsuccessful login attempts. If entered incorrectly, the IP will be blocked.
However, there are now some bypass tools by manually changing the IP with a proxy or VPN, helping Hackers to Brute Force continuously.
Use CAPTCHA
Captcha is a good way to prevent bots and automated tools from performing Brute Force attacks on your website by giving login challenges. Since challenges are designed to be solved by humans, tools and software will have a hard time overcoming them to prevent their attacks.
Now Hacker also released auto bypass captcha tools, including Google Captcha.
Use two-factor authentication (2FA)
2FA creates another layer of security after logging in with a user/password, such as confirmation via email or OTP SMS.
This extra layer prevents anyone from successfully obtaining your credentials.
Pause Brute Force Attacks
It’s amazing to know that one of the most popular and successful methods is man-made. Avoiding Brute Force attacks can simply be a matter of changing your security habits, such as using stronger passwords and not reusing them, or changing the login page to an easy-to-guess URL.
You can also put a little extra effort into security by setting up two-factor authentication or setting your site up later. web application firewall (WAF) . Basically, a firewall will prevent hackers from trying to break into your account.
If you want to learn the tools and how to use the tools used to Brute Force, comment below I will write a more detailed article.