Collecting information is one of the most important steps in pentesting or attacking victims, specifically network scanner. You cannot access a system if you do not have enough information about it. An example to make it easier to understand: suppose you are connecting to a network and one of the devices connected to this network is your target. You need to know all the machines connected to the network and get their MAC and then try to gather information to be able to access your target.
| Join the channel Telegram belong to AnonyViet 👉 Link 👈 |
In this article, I will show you how to build a network scanner (sounds really stupid, from now on I will use the word network scanner) using python.
Prepare Lab
The lab includes 2 virtual machines:
Note: Virtual machines all use NAT connection type. Subnet IP on Nat is 192.168.75.0. The Kali machine will scan Windwos XP to test the network_scanner software.
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/34-1.png)
What is Scapy?
Scapy is a Python interpreter that allows you to create, spoof or decode packets on the network, or capture packets and analyze them, etc. It also allows you to inject packets into the network. Scapy also supports a large number of network protocols and it can process and manipulate wireless communication packets.
Scapy can be used to replace networking tools, such as nmap, hping, arpscan, tshark, and wireshark.
Scapy's operating principle is to send and receive packets, it can also sniff other packets. Sent packets can be easily generated using built-in options and analysis of captured packets. Capturing packets helps us understand what is happening on the network (our home).
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/35.png)
What is ARP?
Currently, there are many ways to discover other machines on the same network. The simplest is to simulate what a normal device would do to discover another device on the same network.
For example, suppose I have a lab set up like the one below.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/40.png)
We have devices ABC and D. They are all connected to the router. We can see that each device has its own IP and MAC. Now, for example device A needs to communicate with device C. Device A knows the IP of device C. But as we know, for devices to communicate in the same network, device A needs to know the MAC address of device machine C because the machines use MAC to communicate rather than IP addresses.
In order for two machines to communicate with each other, they will use a protocol called APRP, which stands for address resolution protocol. And it's a very simple protocol that allows us to bind IP addresses to MAC addresses.
To know the MAC address of machine C, machine A needs to use the ARPU protocol. Basically, machine A will send a packet including its own MAC address and the IP address of the target (machine C) to all machines on the network.
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/41.png)
Now, all machines will not respond to these packets except the machine with IP 10.0.2.6, which is also machine C. ![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/42.png)
Device C will respond to these packets in the form, I am the machine with IP 10.0.2.6 and my MAC is 00:11:22:33:44:66. Done, it's that simple.
Check how many devices are connected to the router
Because NAT's IP subnet is 192.168.75.0, I will detect how many devices are connected to the router in this network. NAT is now acting as a router. ![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/37.png)
Why do I have to add “/24” to the IP? Because “/24” means we will use 24 bits for the Network ID part, and the remaining 8 bits for the Host ID. To put it simply, the program will scan from the ip range 192.168.75.0 to 192.168.75.255, which is also the IP subnet of NAT, readers. this article to understand more.
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/39.png)
Using ARPU in Python
As mentioned above, what is ARP? We will use the ARPU protocol to send a packet containing the target's IP address, then the target will respond to this packet and send it back to us with its MAC.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/43.png)
![]()
Why does ARP ask who has IP 0.0.0.0? But why does ARP reply as 0.0.0.0? Surely there is no machine with IP 0.0.0.0 so it displays like that. So how do I let ARP ask for another IP? First, we must know why ARP asks for IP 0.0.0.0 then we use the function ls().This function will display the default fields in ARP.
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/45.png)
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/46.png)
Please pay attention to the part pdst because it is None so it will be equal to 0.0.0.0. So how do we change it? It's simple, you just need to add parameters. parameters To be pdst and assign ip as arguments in function scapy.ARP(). And remember to remove /24, because now we don't need to search for ip in the range from 0 to 255 anymore.
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/47-1.png)
![]()
We have successfully created an ARP request packet. To see more information about the package, use the function show().![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/49.png) If you notice, the MAC of the packets just created is also the MAC of the machine.
If you notice, the MAC of the packets just created is also the MAC of the machine.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/50-1.png)
Please note this to avoid confusion, the reason it has the same MAC as Kali is because the target ip (the ip these packets will be sent to) of this packet is 192.168.75.128, which is also Kali's ip. In other words, it is sending packets to Kali itself and then getting Kali's MAC.
Note: hwdst and pdst are the MAC and IP of the machine sending packets (Kali), and hwsrc and psrc are the MAC and IP of the machine receiving (replying) the packets you send.
So how do we change the IP to get the MAC of another device? First we have to know what the dst of the broadcast is, then set the target MAC to broadcast.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/51.png)
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/52.png)
Why change target MAC to broadcast? As mentioned above, we need to send these ARP packets to all machines on the network. And to do that, we need to change the target MAC to broadcast so that it sends packets to all devices on the network.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/55.png)
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/53.png)
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/54.png)
What we need to do next is create a new packet that is a combination of the previous two packets (ARP and Broadcast) that we created. To do this, we just need to add a “/” because Scapy supports that.
Why do we have to combine those two guys? ARP packets are just packets sent to a given destination ip and returned to us by MAC, so it cannot be sent to the entire network. But broadcast can solve this problem for us, so we combine the two.![]()
You can use the show() function to view information about the created packets.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/66a.png)
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/58.png)
Send and receive Packets
After we have configured the packets, it's time to send them out and receive packets back including the MACs of the machines on the network. To do that we use functions srp(). This function will return 2 lists: response list and non-response list.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/59.png)
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/60-1.png)
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/61.png)
So we have obtained the IP and MAC of the devices on the network. But those are the packets that can be responded to, what about the ones that cannot be responded to? Try it out, you just need to replace the jaw print wall print(unanswers.summary()) okay. The result is too long so I'm too lazy to take a picture for you guys to see, but in short, it's the unresponsive IPs from 192.168.75 to 192.168.75.255.
Printing the results is too difficult to see, so I will guide you how to design the interface like the image below.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/62.png)
Interface design
As I said above, the software will return 2 lists: answered and unanswered. We only need the response list so we only use the answered list. Now, we go through the list and print the values to see how it is saved.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/63.png)
Why did I add “[0]” into the jaw scapy.srp.Because this function returns 2 lists, when you assign the result of the function to a variable, it will not understand whether you want to get a responsive or non-responsive list, so I have to add “[0]”.
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/64.png)
Too much redundant information. Now I will deal with them one by one. First is this place, I want to hide this place.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/65.png)
You just need to add parameters verbose=Falseinto the function scapy.srp.![]()
Next we will take only what is necessary. You print element 1 of elements, remember to include the function show().![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/67.png)
And it will print several results like this, depending on the number of response packets.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/68.png)
Now, you proceed to get the IP and MAC of the machine that responded to your packets.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/69.png)
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/70.png)
Next, you design the IP and MAC frames.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/71.png)
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/72.png)
Now we will improve it a bit, what if in the future you need to use this list? Maybe we should run it again from the beginning, so we will put this list into the dictionary (dictionary) for easy management and save the dict in the list.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/73.png) We create another function
We create another function print_result() to print the results.![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/73-1.png)
So the design is done. Next, we apply the knowledge in the following sections previous post to add optparse into the software.
Add optparse
LIVE 2 previous articleswe have learned how to add parse to software. Now is the time to apply it. I won't explain again.
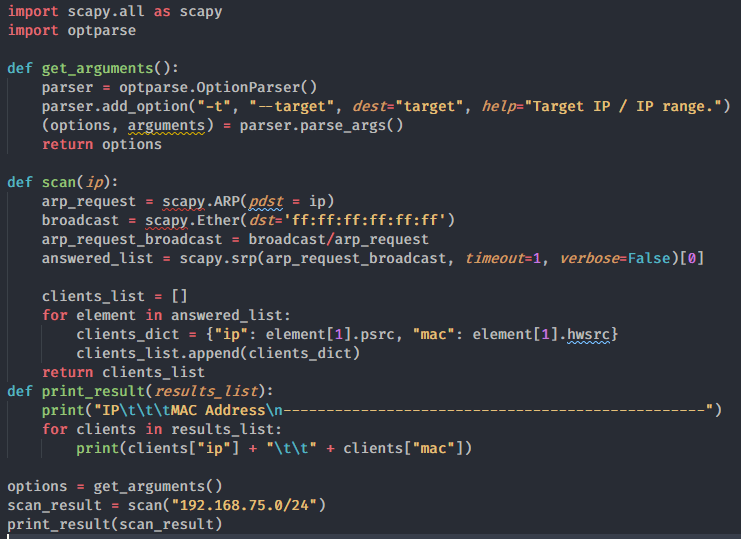
![[PyHack] Lesson 3: Network Scanner Scans network information [PyHack] Lesson 3: Network Scanner Scans network information](https://anonyviet.com/wp-content/uploads/2020/05/75.png)
So lesson 3 is finished. If you encounter any errors, please inbox the fanpage Anonyviet. Or join the group Anonyviet to learn and interact more.