If you suddenly receive frequent spam emails, the content of which may be registration or verification requests, there is a high chance that you are the victim of Email Bombing attacks. The perpetrators may be trying to hide their true goals, so here’s what you need to do to protect yourself.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
What is Email Bombing?

Email bombing are attacks on your mailbox (mail) by continuously sending large amounts of messages to your email. Sometimes these messages are completely meaningless, but more often they will be registration confirmation emails and security notification emails. In the first case, the attacker uses a script (command line) to search the internet for forums and homepages, then register an account with your email address. Each place will send you an email asking to confirm your address. This process repeats over many unprotected sites that the script can find.
The term “email bombing” can also refer to server congestion due to too many incoming emails in an attempt to overwhelm and crash email servers, but that is not the purpose of this article. Instead of a denial of service attack (DOS) to the email server you are using, a message spam attack is a much better way to mask the attacker’s true intentions.
You can also understand Email Bombing quite similar Spam SMS nice Spam mail you have encountered in life.
Why are you a victim?
Email Bombing is often a distraction used to hide your important email in the inbox. For example, an attacker could have gained access to one of your accounts on an online shopping site like Tiki and ordered expensive products on it. Email bombing fills your inbox with irrelevant emails, and hides purchase/delivery confirmation emails so you can’t find them.
If you own a domain name, an attacker might be trying to take that domain away. If an attacker gains access to your bank account or an account on another financial service, they may be trying to hide confirmation emails for financial transactions.
By filling your inbox, email bombing distracts your attention, hiding any important emails. When they stop email bombing, maybe they already have their purpose and your damage is not small.
Email bombing can also be used to gain control of your email address. If you have a nice address, then it is possible that an attacker will attack this address. Wait until you give up, they will be able to take over that address and use it for other purposes.
What to do when you get Email Bombing
If you find yourself the victim of an email bombing, the first thing to do is check and lock your account. Log in to any shopping account and check your recent orders. If you see a strange order, contact customer support and cancel it.
On Amazon, it is possible to save orders and hide them from the regular order list. A Reddit user discovered an email from Amazon confirming an order of 5 graphics cards worth more than $1000 buried in junk email.
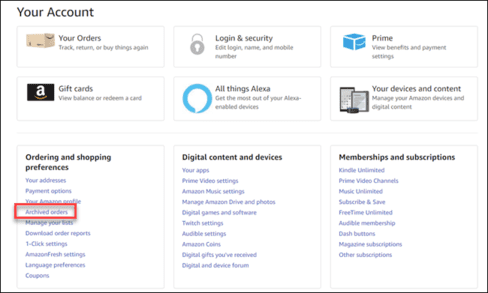
You can check your stored Amazon orders by going to Your Account and click on “Archive Orders” under “Ordering and shopping preferences”. In Vietnam, you probably don’t have to worry about this problem.
After you’ve checked all the websites where you’ve provided payment information, double-check your bank accounts and credit cards and look for any unusual activity. You should also contact your bank and let them know about the situation. They can lock your account and help you find unusual activity. If you own any domain names, you should contact your domain registrar and request a domain lock so that the domain name cannot be transferred.
If you discover an attacker has gained access to one of your websites, you should change your password on that site. And make sure you use strong passwords for all your important online accounts. A password manager will help you create and remember passwords. If you can manage passwords, you should set up two-factor authentication for every website. This will ensure attackers can’t gain access to the account — even if they do get the password.
Now that you’ve secured your accounts, it’s time to deal with your email. For most email providers, the first step is to contact the email provider. But contacting Google is complicated. The Google contact page doesn’t seem to provide a contact method for most Google users. If you’re a paid Google One subscriber or subscriber G Suite, you can contact Google support directly. When I researched their website, I only found a direct method of contacting you when you are missing a file in your Google Drive.
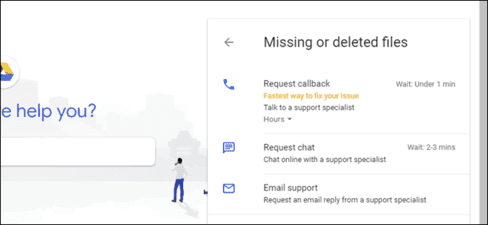
I’m sure anyone on this support group can help you with your problem. Or you can also create a filter to clean your inbox. Try to find some common characteristics in the emails you receive and set some filters to move them to spam or trash.
If you’re using Outlook.com email, you can find help on the web. Sign in to your email, then click the question mark in the upper right corner.
Enter something like “I’m getting email bombed” and click “Get help”. You will be given the option “Email us”then give instructions.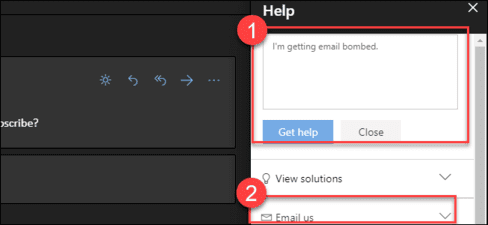
You won’t be saved immediately, but there’s still hope support will contact you to help. In the meantime, you should find some common ground to filter out what you’re getting.
If you’re using another email provider, try to contact them directly and set up a filter. In any case, don’t delete your account or email address. Gaining control of your email address may be what the attacker really wants. Giving up your email address is helping them achieve that purpose.
You can’t stop the attack, but you can wait for it to pass
In the end, there’s nothing you can do to stop the attack on your own. If your email service provider can’t or doesn’t help, you’ll have to put up with this attack and hopefully it will stop soon. Your attackers will either get what they want or realize that you’ve taken measures to stop them, so they’ll be easier to switch to another target.
