Shodan and Censys are the birthplace of our digital lives that connect the giants to the Internet. Start with smartphones, Wi-Fi routers, Surveillance cameras, smart TVs, SCADA networks and traffic light management systems connected to the internet.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

In 2016, the impact of the Mirai botnet attack, considered a distributed denial of service attack, affected 300,000 vulnerable Internet of Things devices.
The integrity and privacy of IoT device data is another growing issue, which is voice-enabled devices like Amazon Echo and Google Home.
Shodan and Censys
It’s in Google’s interest to help you find the data you need on the Internet. There are also special search tools for information security professionals that help discover devices that can be accessed from the Internet.
IPv4 Hosts
Shodan and Censys can scan Internet-connected systems, looking for open ports and services listening on a port.
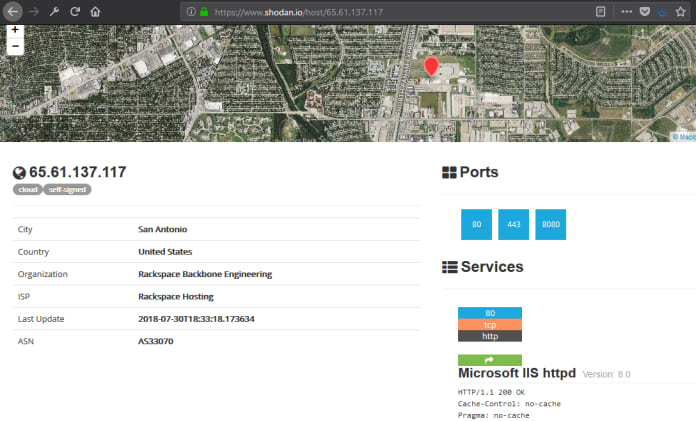
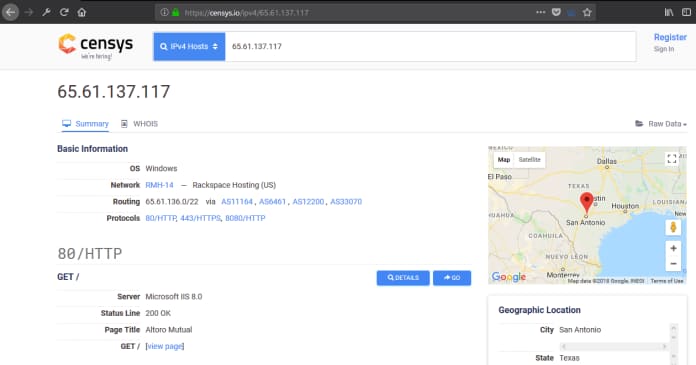
Detected open ports have the correct banner version, WHOIS information, and server geolocation.
Operating systems:
Detect old version of Windows operating system (Windows XP) on the Internet.
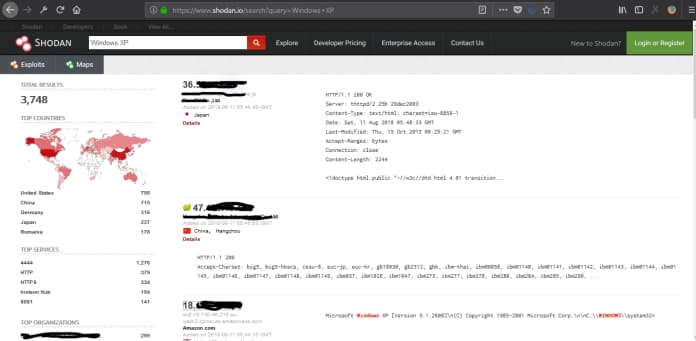
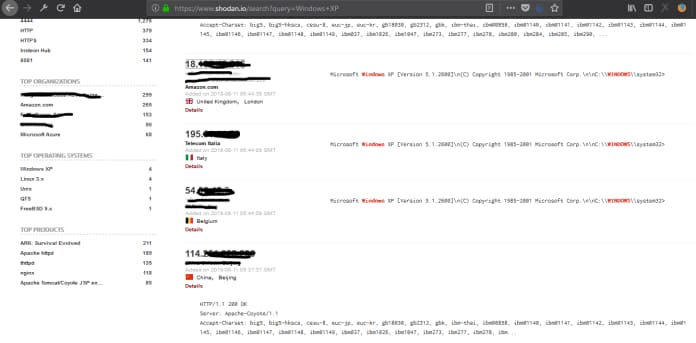
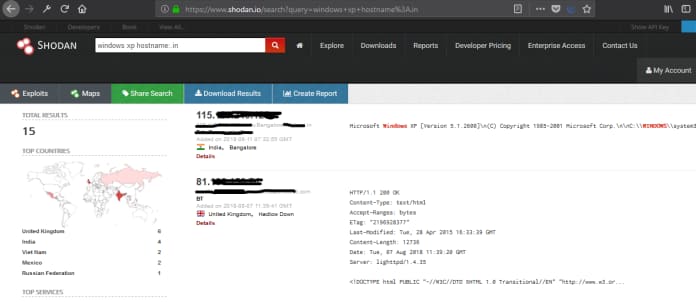
Using the appropriate filter (windows XP hostname:.in) can find any operating system on the internet.
Web Server
Check web server versions with Query Server:
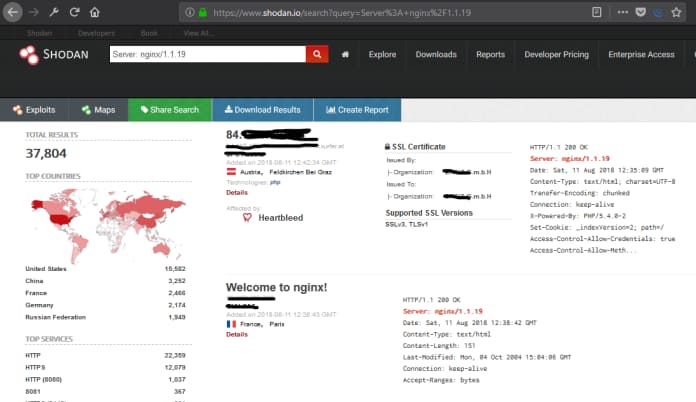
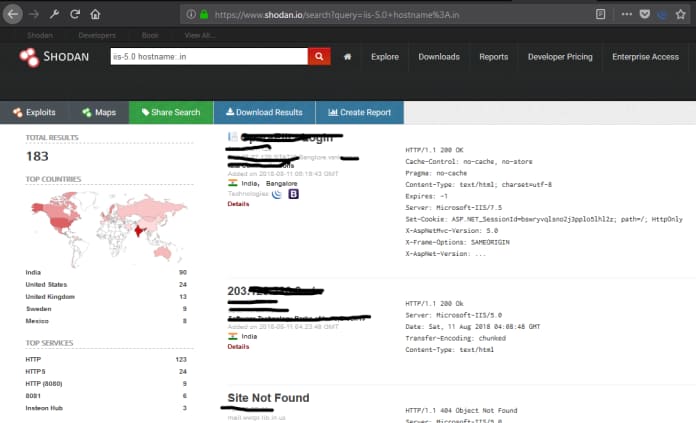
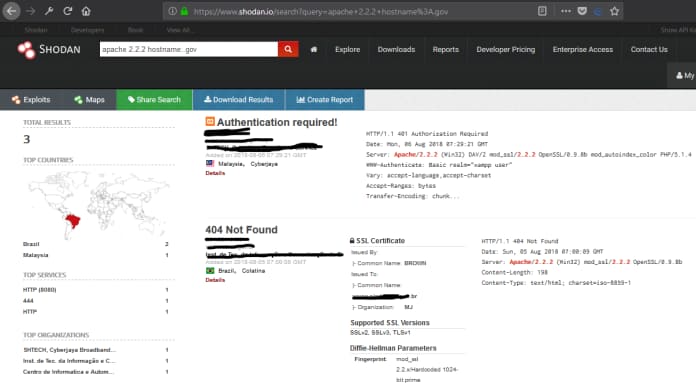
It would be helpful to check for any vulnerable versions of web servers on the internet.
Web application Firewalls
Explore the target’s web application firewall.
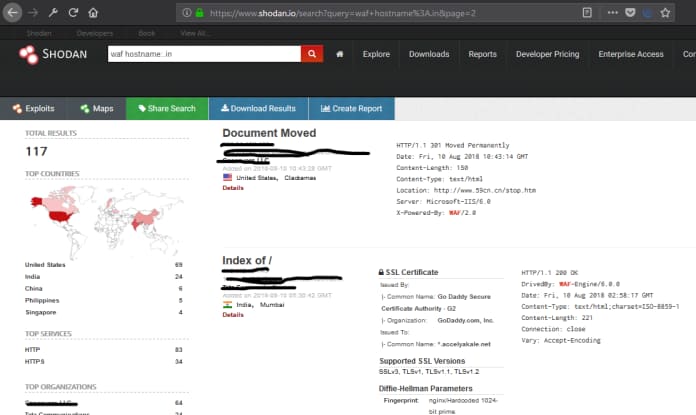
Router
Discover Cisco, Netgear and more vulnerable routers in your country.
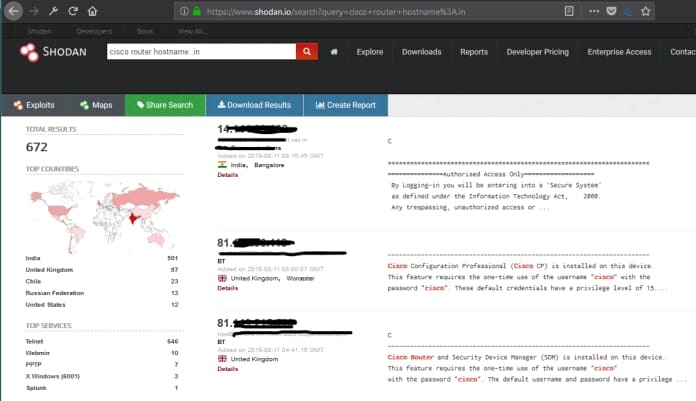
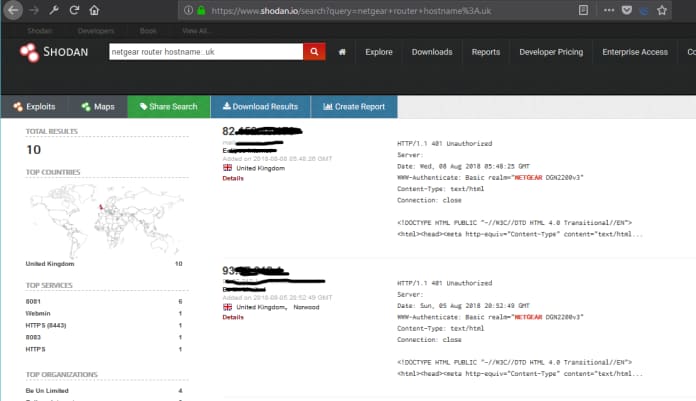
More than 65,000 vulnerable routers have been abused by the Universal Botnet Proxy.
Media & Entertainment
Discover satellite TV servers in different countries.
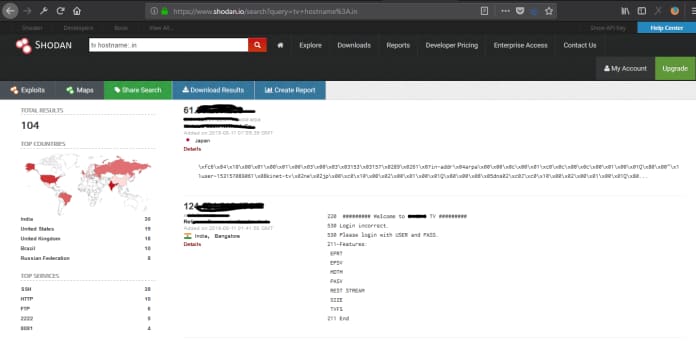
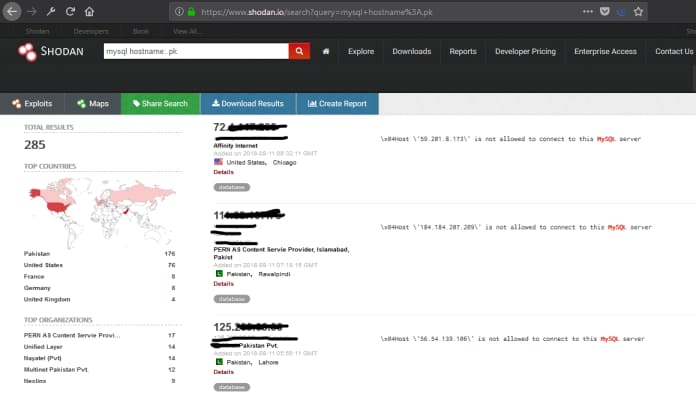
Database servers
Discovering the Database servers of any organization is possible with these search engines.
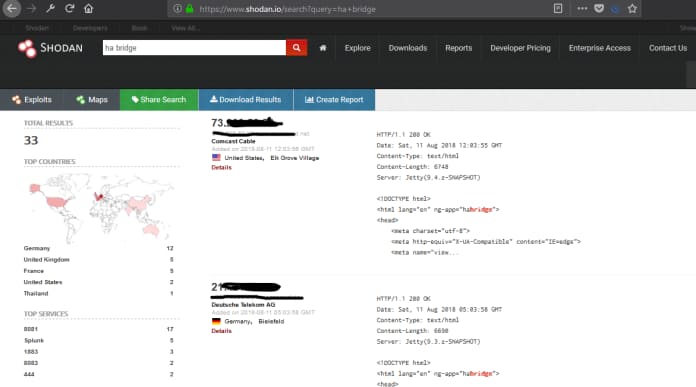
Home automation appliances
Search for HA bridge (Home Automation Gateway like Amazon Echo/Philips Hue).
Find an Amazon Echo/Google Home IoT device using Shodan.
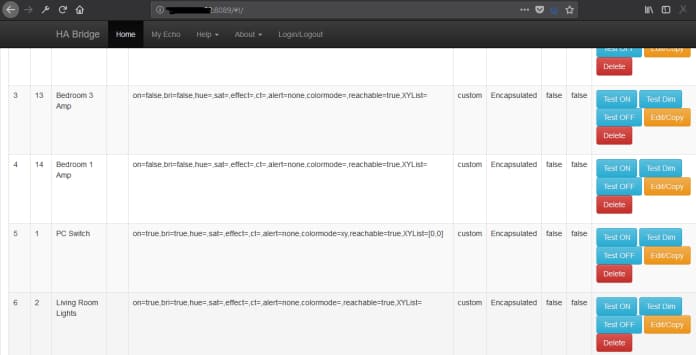
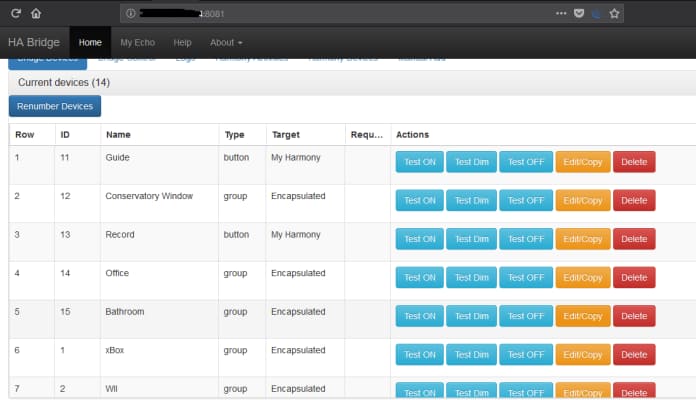
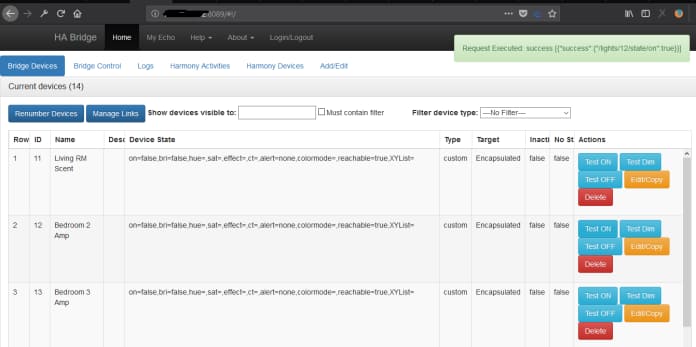
Discovered the remote access of bedroom lights, living room.
Remote commands such as “On”, “Off” command to turn off or on the light.
Industrial control systems – Industrial Control System
Search for ICS/SCADA (Industrial Control System/Supervisory Control and Data Acquisition) Equipment in your country.
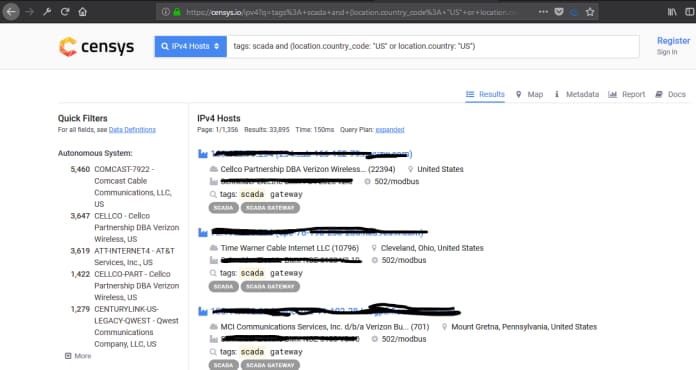
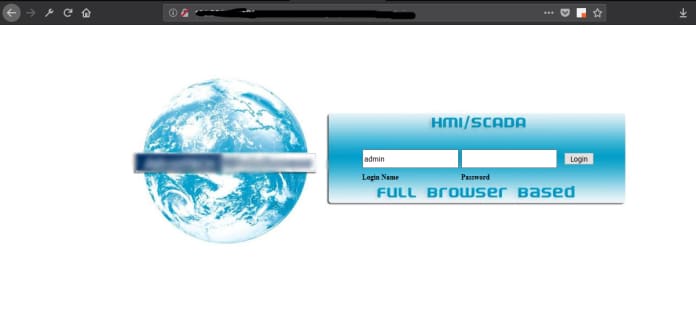
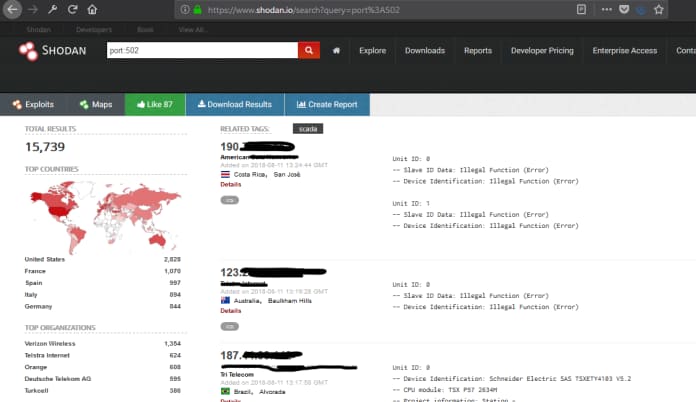
The images above illustrate that anyone on the internet can access agricultural devices and manipulate misconfigured SCADA devices.
‘s search engine Shodan Very powerful to find any vulnerable device on the internet. It can be part of your penetration test to make it easier to discover new things on the internet.











