Website security is always a necessary issue before operating on the Internet. If you want to check if your Website has security holes, use OWASP ZAP – Zed Attack Proxy software to scan for errors.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
OWASP ZAP – Zed Attack Proxy is an open source tool that allows you to test the robustness of your application against security vulnerabilities. But what exactly is OWASP ZAP?
In a nutshell, this is a vulnerability testing tool that helps programmers and security professionals discover website vulnerabilities. You can perform a variety of tasks through OWASP ZAP, including scanning web requests, using dictionary lists to find files and folders on the web server, and crawling websites to find all the files and folders on the web server. link and URL. In addition, you can intercept, view, modify, and forward web requests between the browser and the web application using OWASP ZAP.
OWASP ZAP scanning can reveal problems related to SQL injectionbroken authentication, exposed sensitive data, broken access control, security misconfiguration, Cross-Site Scripting (XSS)insecure decryption, components with known vulnerabilities, and any missing security headers.
In this article, we will see how OWASP ZAP works, how to set up ZAP, how to create our own crawlers to scan for vulnerabilities.
How does OWASP ZAP work?
OWASP ZAP is a proxy server that scans all traffic running through it. This proxy server includes automated tools that allow you to block security holes on your website and generate reports from its findings. Here’s a quick diagram of how ZAP works.
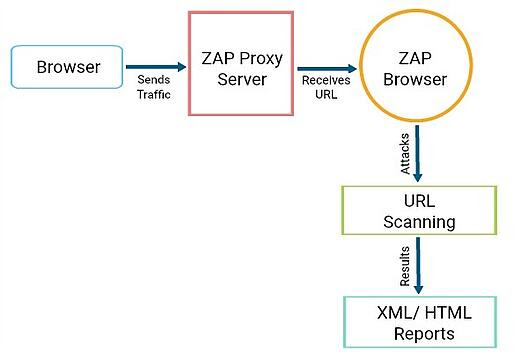
ZAP creates its attacks by running the ZAP browser on a URL. During this process, ZAP will use its crawlers to gather information about a target application, scan all available pages, and then run the active scanner on it. The active scanner will accurately identify any vulnerabilities using known attack methods on the targets it receives from the scan. Alerts will be issued if potential vulnerabilities are detected and flagged from high to low based on the level of risk.
Setting up ZAP – Zed Attack Proxy
Step 1: To set up OWASP ZAP, you need to install it first. You can access: zaproxy.org/download to select an installer that is compatible with your operating system.
Step 2: Once downloaded, run the installer.
Step 3: Read and accept the terms and conditions to continue.
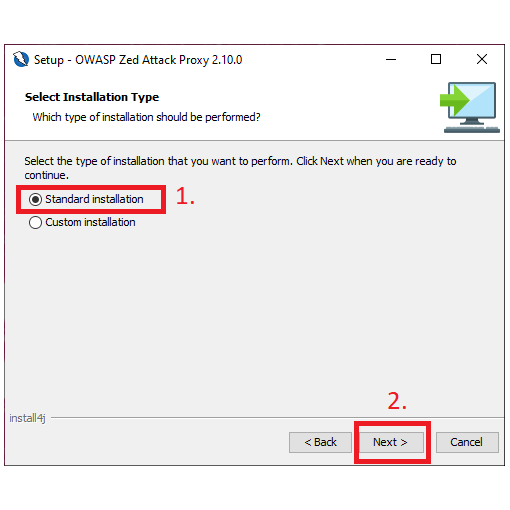
Step 4: Select ‘Standard installation’ and click ‘Next’.
Step 5: Click ‘Install’ to finish.

Step 6: Wait a moment for the program to finish installing.
Step 7: Once done, you will be directed to a screen that looks something like this.

Create ZAP Spider
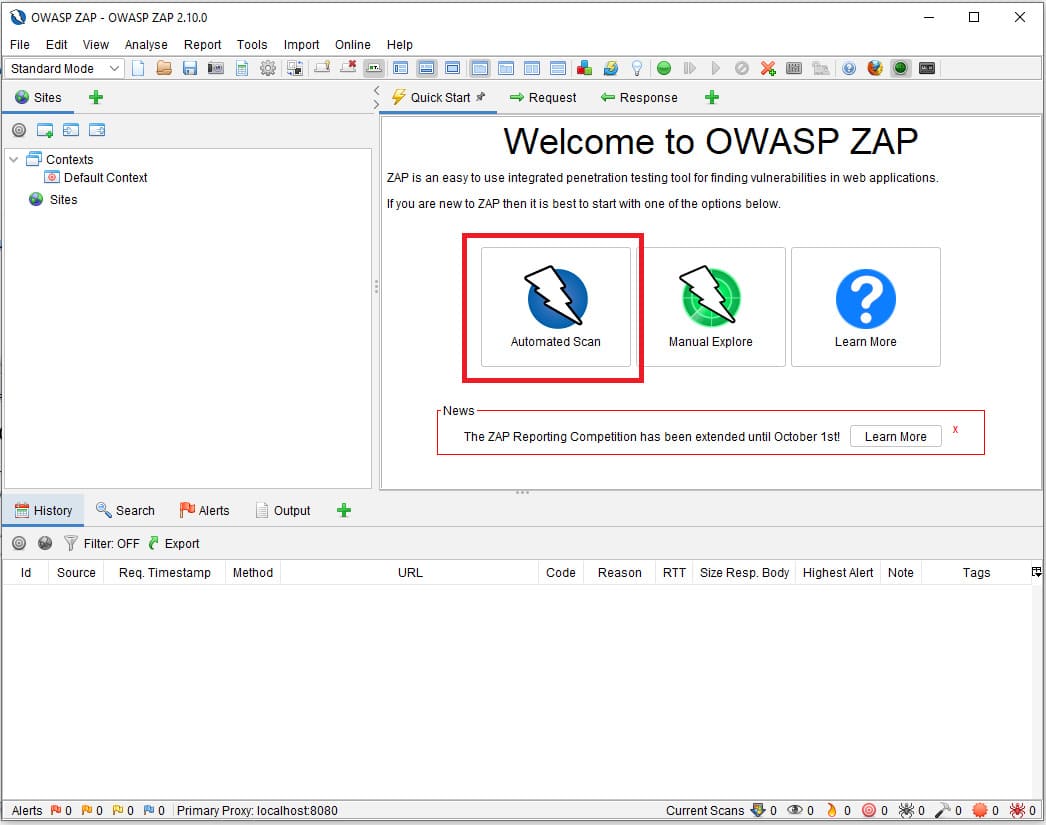
To run the first scan, run the newly installed OWASP ZAP. You will be greeted with a screen that looks like this:
Once the download is complete, you will get a screen that looks like the image below. In the main ‘Quick Start’ view, you can choose between ‘Automated Scan’ and ‘Manual Explore”. For this tutorial, select ‘Automated Scan’.
 This option will give you a page like the image below. You can run it on your application by pointing the destination URL to the localhost your application is currently running on.
This option will give you a page like the image below. You can run it on your application by pointing the destination URL to the localhost your application is currently running on.
This is an example of when in the scan phase.
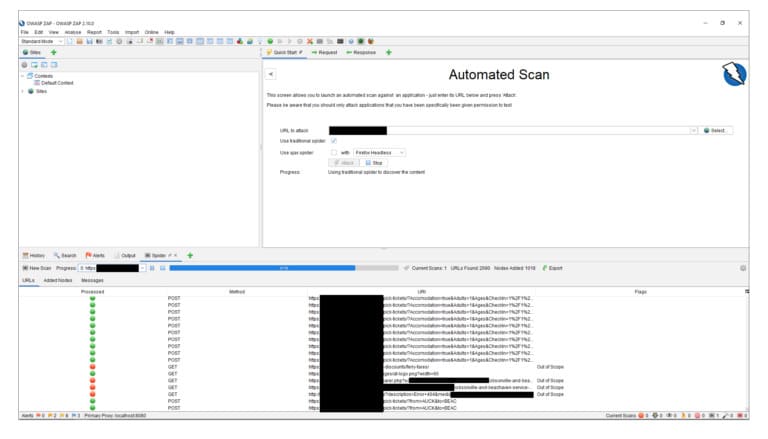
Once done, you can click on the ‘Alerts’ tab to see all the potential vulnerabilities.
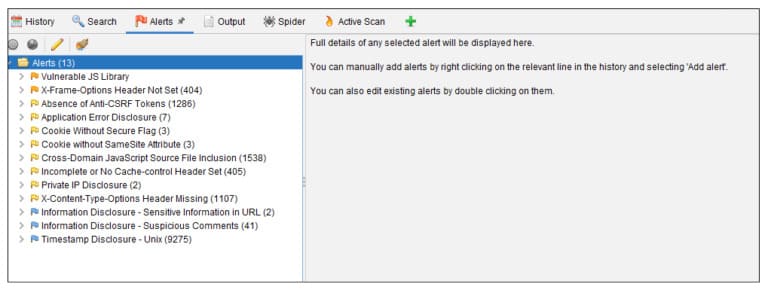
Based on the example and scan results above, we can see that the issues detected are not serious and can be easily remedied, such as X-Frame-Options and Anti-CSRF Tokens.
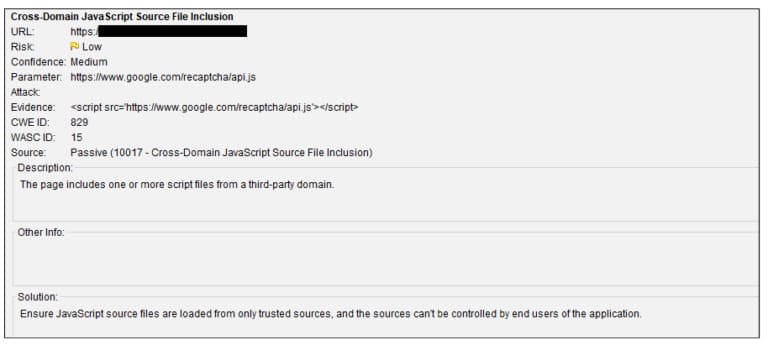
The impact of a vulnerability can be assessed by the number of specific alerts. For example, cross-domain JavaScript source file inclusion seems to be a bug of some sort. However, if we dig deeper, we find that the risk is classified as low because of the reliable source.
Here’s a screenshot of one of the flagged warnings and reports generated for the cross-domain JavaScript source file inclusion error. Right below is a solution on how to reduce this vulnerability based on this bug.
Conversely, if we want to start vulnerability testing based on severity, OWASP ZAP will automatically rank from highest to lowest in the ‘Alerts’ file list. The top warning on the list is ‘Vulnerable JS Library’. The report is marked as medium risk because the jQuery used is not the latest version.
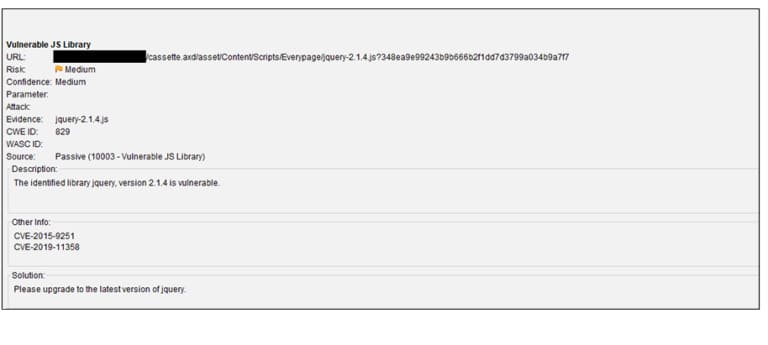
A little more digging into jquery-2.1.4 tells us that this target site is vulnerable to Cross-site Scripting (XSS) attacks via elements from untrusted sources. This is because in the JQuery version, DOM manipulation methods can execute untrusted code.
Conclusion
The Quick Scan function of OWASP ZAP – Zed Attack Proxy will not “hack” your Web. However, it will give you an overview of the security issues and vulnerabilities your website is facing.
Using OWASP ZAP during the programming phase can also help us improve our security processes by identifying problems before they grow too large over time. It is easier to fix a potential vulnerability when it is small than when it is large and affects the entire developed application.
One thing to keep in mind is that if you run OWASP ZAP on a more mature application with lots of legacy code, you may get a large number of warnings. This is normal, especially if security is not part of the growth mindset at first. As long as you prioritize your vulnerabilities and find ways to address them, it will increase the security of your application.
In addition to running the function Quick Scan manually every time, you can also automate it into your workflow via Docker Packaged Scans, GitHub Actions or automation frameworks.

