In this article, I will show you how to find the IP origin hidden behind CloudFare or Tor. Security services like CloudFlare or any similar service do not completely hide the IP of the origin server. Small mistakes in service configuration can also expose IPs and will allow hackers to attack a website that uses CloudFlare (bypassing WAF, Rate Limits, DDoS Protection, etc.), or even know it the identity of the website owner on Tor. These mistakes depend on the type of service or technology you are using, not all of the methods below will work on every technology (e.g. MX records don’t work on Tor hidden services). ).
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

How to find the real IP origin hidden behind CloudFlare or Tor
1. SSL Certificate
1.1 Using a certain domain name
You are hosting a website full of drama on xyz123boot.com. Your origin server IP is 136.23.63.44. CloudFlare is providing you with DDoS Protection, Web Application Firewall and several other services to protect your project from bad guys. Your web server supports SSL and has a certificate, so the communication between CloudFlare and your server is encrypted just like the communication between your users and CloudFlare (i.e. no Flexible SSL). Everything starts here.
The problem is that you also expose the SSL certificate when connecting directly to your IP on port 443 (https://136.23.63.44:443). Hackers can scan 0.0.0.0/0, the whole internet, on port 443 for a valid certificate of xyz123boot.com to get your web server IP.
You can use Censys to scan the system. The only thing you need to do is enter the queries you want.
Certificate for xyz123boot.com: parsed.names: xyz123boot.com valid only if there is: tags.raw: trusted
Combining multiple parameters on Censys can be done using simple Boolean logic and.
Search terms: parsed.names: xyz123boot.com and tags.raw: trusted
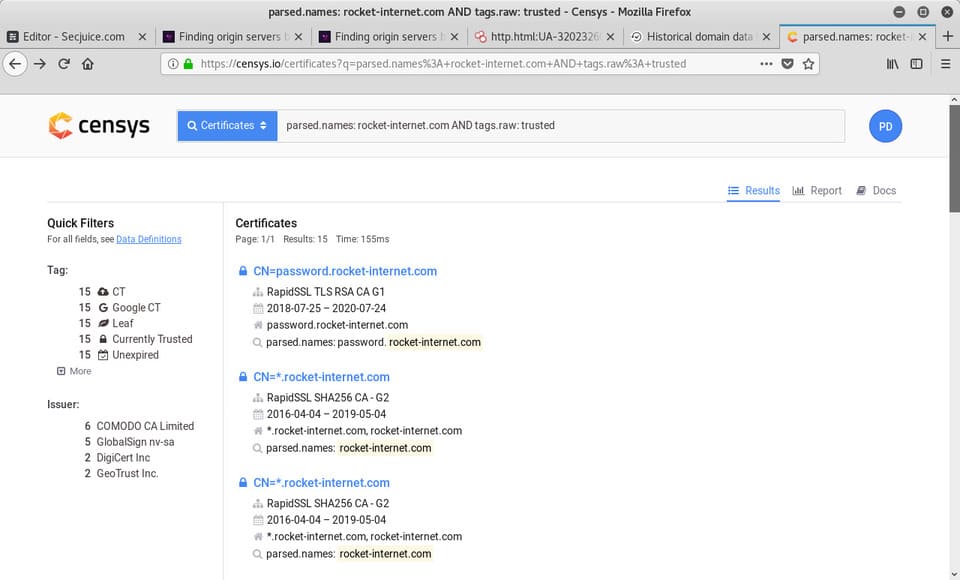
Censys will show you all the certificates that match your requirements.
Click on each search result, you can open a list of several tools by clicking “Explore” on the right side. Select What’s using this certificate? > IPv4 Hosts
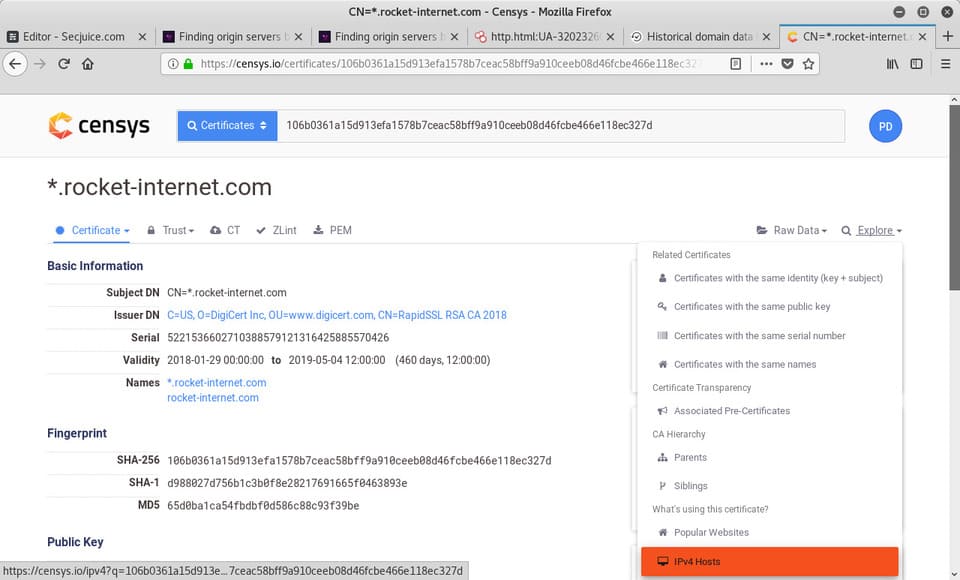
You will get a list of IPv4 Hosts certificates. One of them could be the original IP.
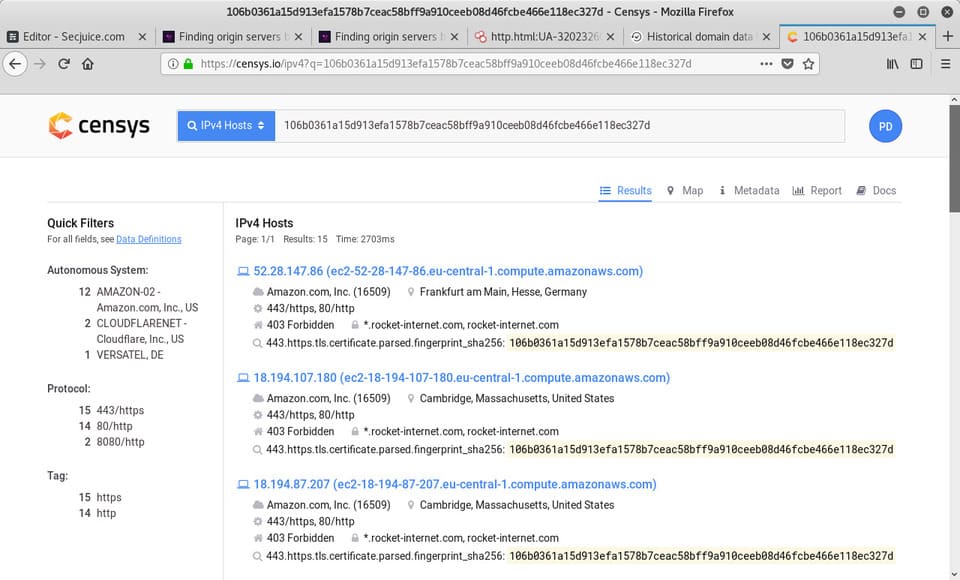
You can verify by accessing the IP addresses on port 443. Does it redirect to xyz123boot.com? Does it show the site directly on the IP?
1.2 Use certain SSL certificates
Let’s say you’re the FBI and want to shut down a hidden child porn service available under the domain cheesecp5vaogohv.onion. For that you need the root IP to be able to contact the host and also to trace the operator.
Finding an IPv4 server using the same certificate can be done by simply pasting its SHA1 reference file into the Censys IPv4 server search bar. This method can easily find a badly configured web server.
2. DNS records
After being attacked many times, you decide to start using CloudFlare. Data-driven services like Censys will find DNS records that contain record A point to your web server IP address.
One platform that can do exactly this is SecurityTrails. Just type the website domain name in the search bar and hit enter. You can find “Historical Data” in the left menu.
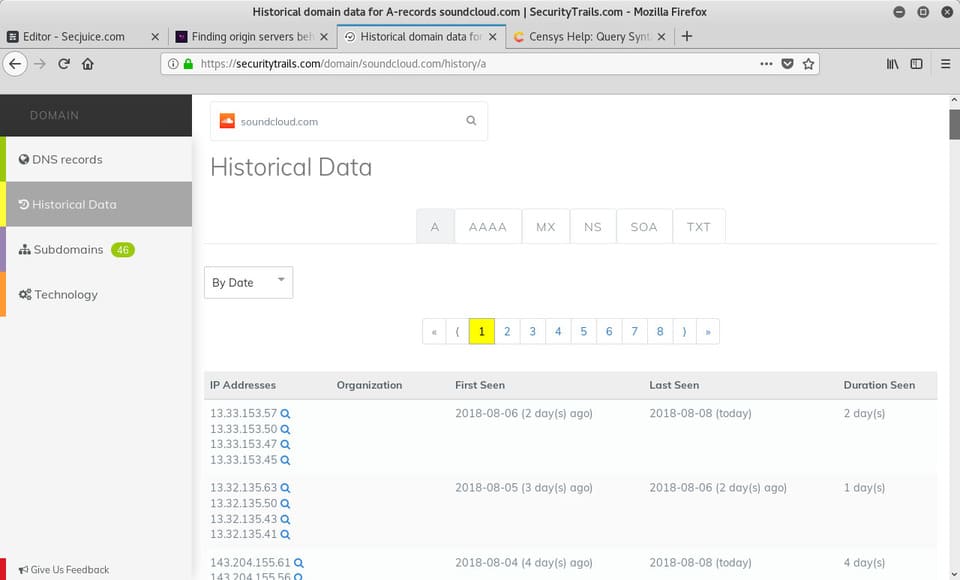
Besides the old A records, even the current DNS records can leak the IP of the origin server. For example, MX records are easy to find your IP. If the site is hosting its own mail server on the same server and IP as the web server, the origin server’s IP will be in the MX record.
With data-driven platforms that allow anyone to perform powerful searches on large amounts of data, origin servers can even be found by comparing HTTP headers.
Especially when there is a server header that has a lot of different software including subversions, it becomes much easier to find. This is also not limited to a single parameter. As mentioned in 1.1, you can combine search parameters on Censys. The likelihood of finding results increases with every title key you enter.
Let’s say you are sharing your server HTTP headers with 1500 other web servers, who are sending the same header key and value. You are also using the new PHP framework that sends a single HTTP header (e.g. X-Generated-Via: XYZ Framework). About 400 webmasters are using that framework in production. You can go through those headers manually to find the IP.
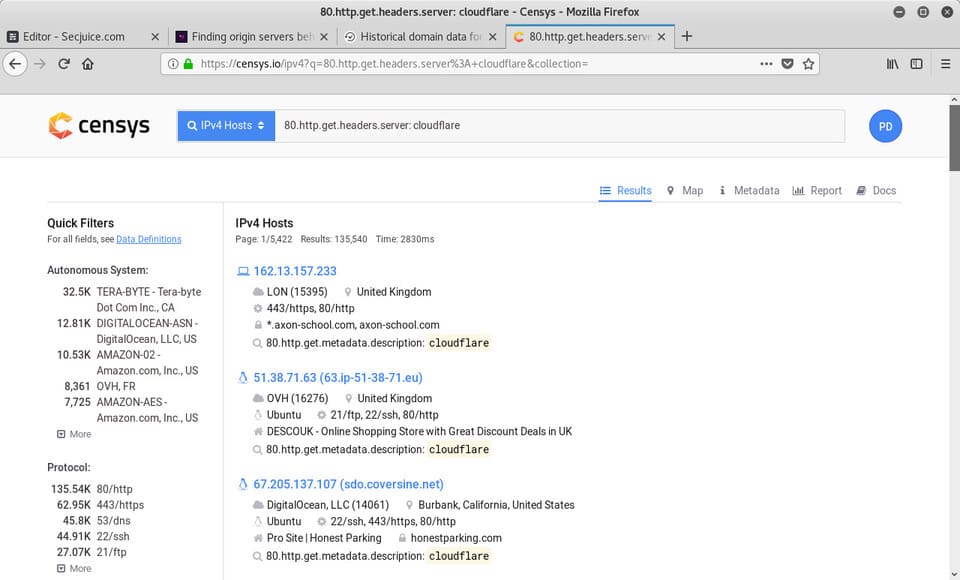
For example, the search parameter on Censys to match the host header is 80.http.get.headers.server :.
Search for sites powered by CloudFlare:
80.http.get.headers.server: cloudflare
4. Applications and Services
A Tor hidden service or a website offered through CloudFlare are both normal websites. A quick pentest process can also find IPs.
Headers such as the HTTP server header can be used to exploit the services and web version you are using. Once you have access to the server, you can easily find the IP.
You can also find the cases that cause the error. Error messages can also reveal sensitive information like your IP address or anything that can be used against you.
Running gobuster to find files and folders during the scouting phase should be done in every pentest. Things you can find are logs, database dump/backup, etc.
Also, the first thing to check is to find out if you can make the app feed the website to interact with other services. If you’re not the NSA, you might not be able to get the IP if they just use the API. But for example, you can put a profile picture on your website and provide the URL for the photo instead of uploading it. If they’re downloading the image from the origin server, you’ll have that server’s IP address in the logs.
5. Content
In case the IP of the origin server is also returning the content of the website, the huge amount of searchable data in that content will help you.
Browsing through the source code of web pages, you’ll find exploitable code. Third-party services (e.g. Google Analytics, reCAPTCHA) having an access key/identifier in JavaScript is a good sign.
Google Analytics tracking code taken from HackTheBox website:
ga('create', 'UA-93577176-1', 'auto');
Filtering data from Censys by body/source can be done with the parameter: 80.http.get.body:.
But the free version has limitations. You can request research access at Censys to execute much more powerful queries through Google BigQuery.
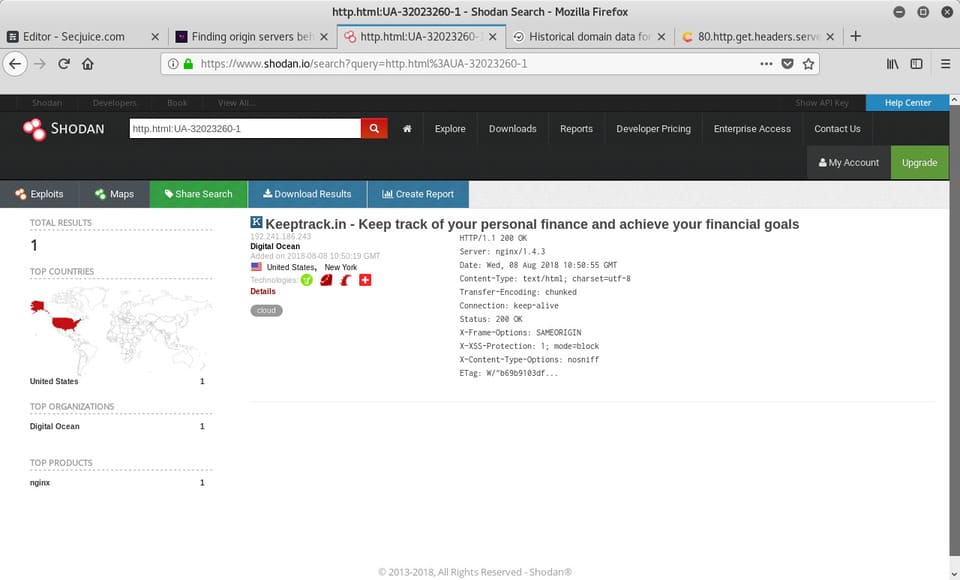
Shodana service similar to Censys, also provides the http.html search parameter.
Eg:
https://www.shodan.io/search?query=http.html%3AUA-32023260-1
6. Favicon Hash Matches
While not the entire content of a website can be the same as the public host, a logo image is often a good helper to associate a website with a project or at least some work. certain technology.
Shodan allows favicon hashes through http.favicon.hash. Use the hash to find the MurmurHash3 of the logo in base64.
You can use the following Python3 code to generate the hash:
import mmh3
import requests
import codecs
response = requests.get('https://<website>/<favicon path>')
favicon = codecs.encode(response.content, 'base64')
hash = mmh3.hash(favicon)
print(hash)
Hashcode example:
7. SSH key fingerprinting
Another very easy mistake to make is adding the hidden services server’s SSH server to /etc/tor/torrc for access via Tor, which does not protect the service from being accessed by the server IP. As seen with the web server.
Every time a service is transmitted through both servers, the SSH key can be compared with the servers in 0.0.0.0/0. In some specific cases, this can be very dangerous.
Provide a standard port SSH server as a hidden service at h5kfqine24owlbl2aboxjs4craefrnrazyw46zemnwgmpq5u6q52wnyd.onion, you can get SSH key fingerprinting using ssh-keycan.
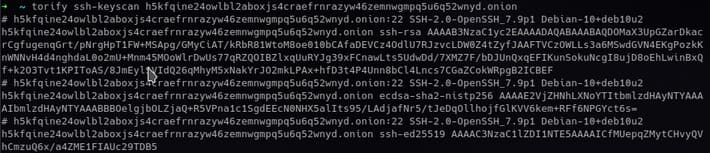
Compare the fingerprint with the IP server to discover the host.
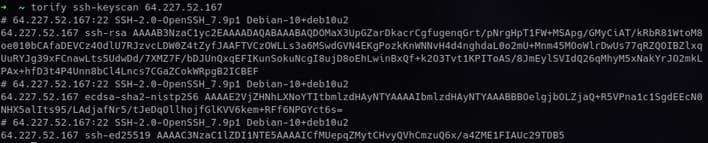
Certainly, the corresponding data has already been collected and aggregated on a large scale.
At Censys you can filter servers by ECDSA Y components with 22.ssh.v2.server_host_key.ecdsa_public_key.y.
Conclusion
Ultimately, figuring out the origin IP behind hidden services like Tor or reverse proxy services like CloudFlare mostly requires a certain amount of web knowledge.
The security site x0rz also explained its countermeasures against hackers exploiting the Tor hidden service. Also, do you know any other methods?