This article will explain what privilege escalation is and how we can upgrade our privileges using the SUID permissions file. You can use this knowledge to solve Christmas Advent of Cyber challenge number 8.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

What is privilege escalation?
Computer systems are designed to be used by many users, and privileges mean what users are allowed to do. Common privileges include viewing and editing files or modifying system files.
Privilege escalation is the act of exploiting a bug, design or configuration flaw in an operating system or software application to gain higher access to normally protected resources from an application or user. .
What is SUID?
SUID is a special type of file permission granted to a file. When a user runs a program, if they have the correct read/execute permissions, that program will run using their account privileges. SUID allows a user to run a program using the privileges of another user. To learn more about file perks, complete challenge 4 in the Christmas room or read the supporting material here.
In some cases, we can take advantage of running the file as another user, to execute mining commands. You might be thinking, why allow anyone to run the file as another user, right? However, we need to have certain binaries run as root by an unprivileged user.
For example, if we change our password on Linux, the program that does this needs permission to change the file system. You may not have write permission to the /etc/ directory, but root does. This is why the password binary has the SUID bit.
If a binary file has a SUID bit then it will have permissions S. If we check the permissions for the password binary, we can see the permissions -rwsr-xr-x.
![]()
The SUID bit is set on execute permission, which means that when a user runs this file, it will run as the file owner (as root).
In essence, SUID files execute with the permission of the file owner.
Make use of SUID files
Some administrators will manually set the SUID bit to allow certain programs to be run. Let’s say you are a system administrator and an unprivileged user wants to programmatically require the file to run with higher privileges. They can set the SUID bit, then unprivileged users can execute the program without any additional account permissions.
We can scan the entire file system to find all files with the SUID bit, with the following command:
find / -user root -perm -4000 -exec ls -ldb {} \;
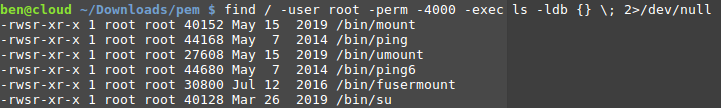
We can see some binaries running as root, which are legitimate programs with the right permissions set up to do the right task.
If a sysadmin has manually set the SUID bit on a binary file, the above command will find those files. You can take advantage of this command to elevate your privileges or run commands you wouldn’t normally be able to do.
Tips for the SUID challenge
A regular standard Linux binary (such as the find command), which can change the file owner and the SUID bit.
For example, if we want to know what user is running the find command, we can do the following:
touch foo
find foo -exec whoami \;This command will find the file foo (which we just created), then run the command with the -exec parameter.
If you find a file that looks suspicious? Try running it and see what you can do with it? Run the whoami command to see if the file is actually running as root.
If you are given the option to run the command as another user. Why not run /bin/bash to run bash (for the shell) as another user?
Also, you can check out Shodan.io readings on TryHackMe here.