Metasploit is an automated vulnerability exploit software built into Kali Linux. However, you may not have heard of the Metasploit Pro version. This is an enhanced version with an interface and is a product of the famous security firm Rapid 7.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
Metasploit Pro Is one mining tool and vulnerability authentication security yes user interface helps you break down your Pentest (penetration testing) process into smaller and more manageable tasks. With Metasploit Pro, you can leverage the power of Metasploit Framework (built into Kali Linux, Parrot OS) and mining database available via web interface to perform security assessment and authentication gap.
Metasploit Pro allows you to automate the process of finding and exploiting vulnerabilities, and gives you the tools to experiment with attacks on vulnerable targets. You can use Metasploit Pro to scan open ports and services, exploit vulnerabilities, collect errors and generate test reports.
Metasploit Pro is also a tool for a team to work together, allowing you to share tasks and information with members of the penetration testing team. With team collaboration, you can assign each member to perform different tasks on how to exploit the target system. Team members can share goal data, view collected evidence, and create notes to share knowledge about a specific goal.
Finally, Metasploit Pro is a tool with a Web interface for you to identify a system’s vulnerability and take action based on it.
Supported Browsers
Since Metasploit Pro works on a Web interface, you need to install 1 of the browsers below
- Google Chrome 10+
- Mozilla Firefox 18+
- Internet Explorer 10+
- Iceweasel 18+
Metasploit Pro is quite expensive, but the company allows users to register for free 14 days using Business Email. After 14 days you can still use another email to continue to register for a 14-day trial. Proceed as follows:
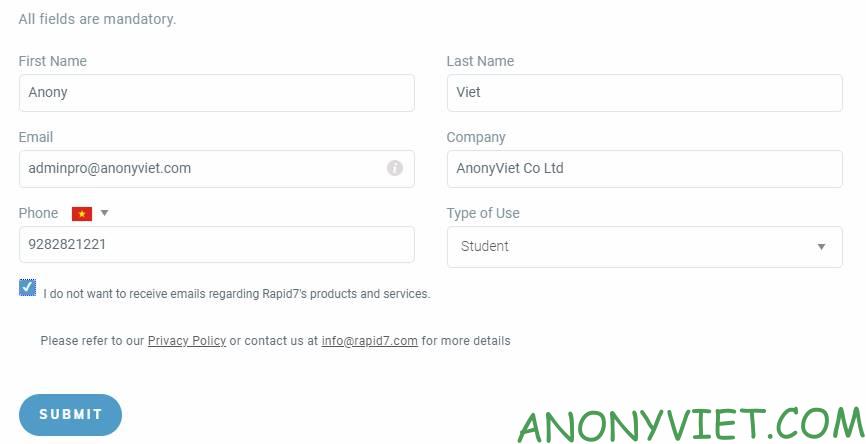
First you visit the page Sign up for a trial. Use temporary virtual mail to get Business Mail to register for an account.
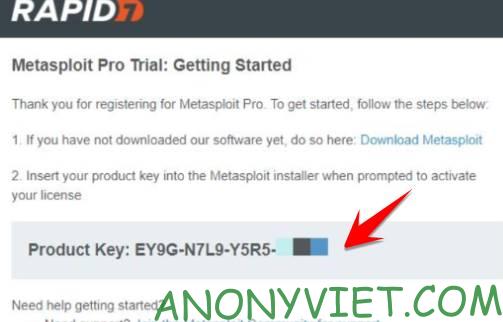
Wait for about 3-5 minutes, you will receive the Key in Email
Next, you access Download Metasploit Pro about and install. During the installation process, you need to note a few steps:
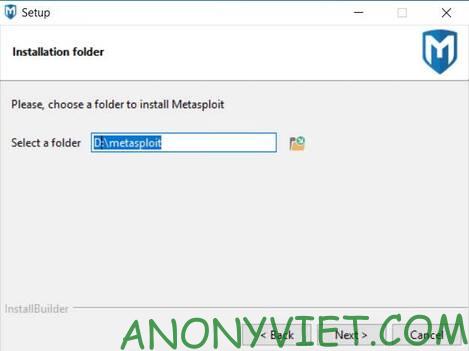
Select Metasploit Pro installation directory
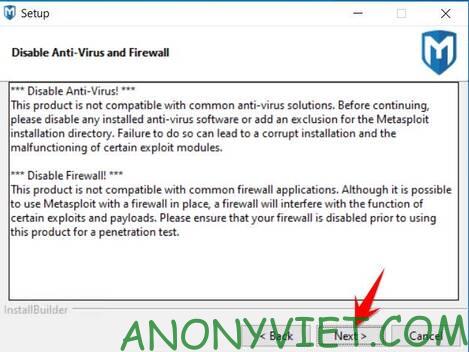
Disable Anti-Virus and Firewall on Windows. If you use Windows Defender, turn off Realtime-Protection scanning.
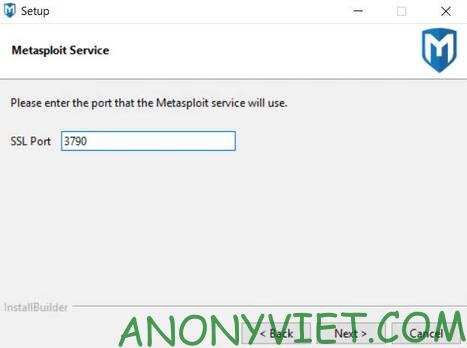
This is the step to set up the Port to start Metasploit Pro in the browser. It is best to leave the default as 3790and remember this Port to open the program half way.
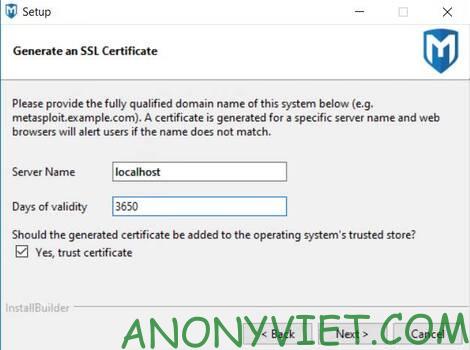
This is the step to create an SSL certificate for Metasploit Pro, you should also leave the default.
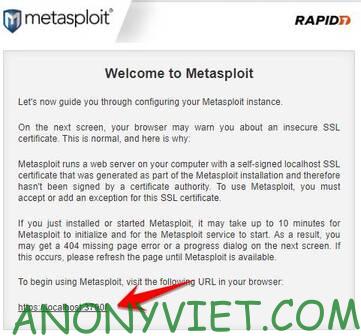
Now click Next and wait for the installation to complete. In the Welcome screen, click on the link https://localhost:3790. Here is also the link to access the Metasploit Pro interface
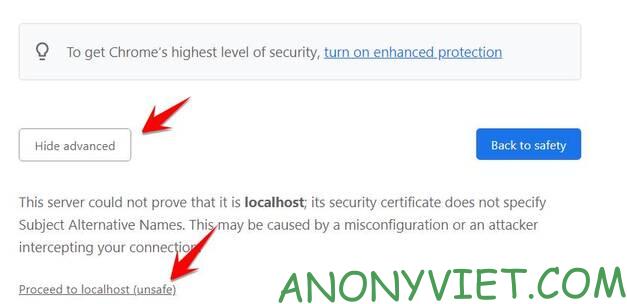
If your browser has an SSL error, just click on Proceed to localhost (unsafe)
Next you create a user/password to log into Metasploit Pro. This is only a Local account, you can order later, name and password are free.
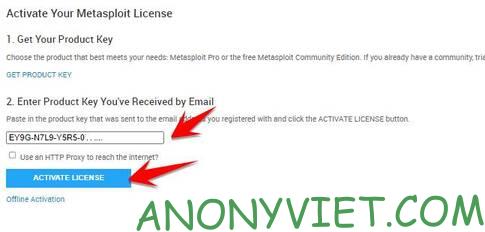
Next is to enter the Key sent in the mail, select the line Enter Product Key You’ve Received by Email and click Active License.
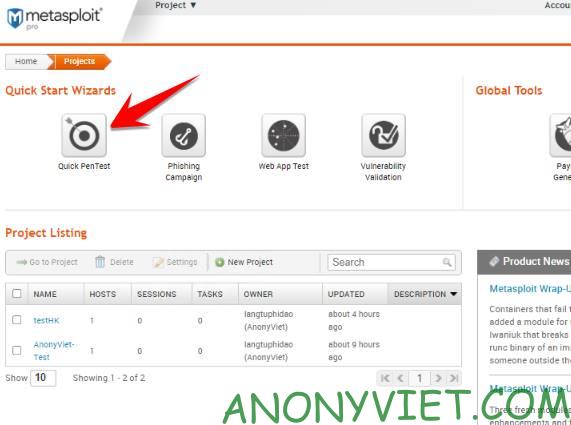
That’s it, you have activated the 14-day Key for Metasploit Pro for free. To test a target vulnerability scan, select Quick Pentest
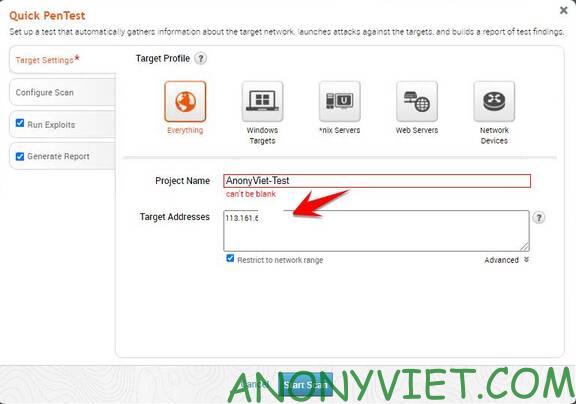
Next, name the Project, Enter the IP to be scanned in the box Target Address. Press Start Scan
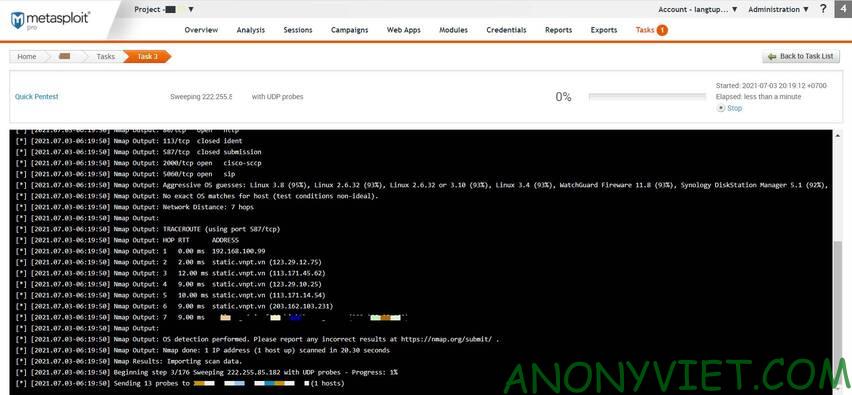
Now sit back and wait for the security hole scan. When there is a vulnerability, the program will automatically generate a report for you.
In addition, the program has built-in automatic exploitation feature when detecting vulnerabilities. I will write in the next part (if this part has many people interested).