In fact, new online jobs are a lucrative goldmine for cybercriminals looking to take advantage of security gaps. When employees use private WiFi networks to access company resources remotely, this is a favorable condition for Hackers to attack your WIFI. Many people will unknowingly leave their WiFi exposed to hackers and this will pose a serious threat to your data.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

Hackers can easily access unsecured Wifi or you use a password that is too simple. Hackers only need a wireless network adapter (about 500k), open source software (free), like Airgeddon, to test wireless networks.
How Hackers Attack Your Wi-Fi?
Despite its many legitimate features, Airgeddon can be used to perform some simple but very effective attacks against WiFi networks. To be able to access Wifi using a weak password, hackers will use Airgeddon to kick users out of that WiFi, get WiFi “handshake”, which is a hashed version of the password. Hackers can use this handshake to perform a brute-force attack to find out the password – Wi-Fi with a simple password is easier and faster. Even with strong Wifi password will be hacked with social engineering.

To trick the Wifi owner into revealing the password, hackers can use Airgeddon to lure them into a phishing page (for example, pretending to be a network operator’s website). To do this, the hacker once again kicks the user out of the WiFi, and causes that WiFi to crash and become inaccessible. At this point, the hacker will broadcast a WiFi with the same name as the old WiFi. When the user, enter the password into this WiFi, then the hacker will know the password of the real WiFi.
When the user connects to the new WiFi, they will see a fake login page asking for their WiFi password to restart the router due to a problem or a new update. In fact, you just need to create a WiFi with the same name as the old one and set the password for that WiFi. When the user enters the password, more than 80% of the password is correct. As for the web, hackers can take the hashed password of the real WiFi and compare it with the password entered by the user. So the phishing site only accepts the correct password for the real WiFi. Note: the comparison here is a hash code, not a text password.
When the hacker has connected to the carrier WiFi. They can redirect users to other phishing websites to collect more data or access home devices such as smart speakers, light bulbs.
Hidden VPN and WiFi
To combat that, online employees can take a few simple steps to lock down WiFi networks to protect themselves, and their companies, from cybercriminals. First, they will block the feature to make it easier for them to access remotely. They can usually be disabled without affecting WiFi and it will prevent hackers from breaking into your home network. This feature includes WPS which, if enabled, makes WiFi vulnerable to brute-force PIN or WPS-Pixie.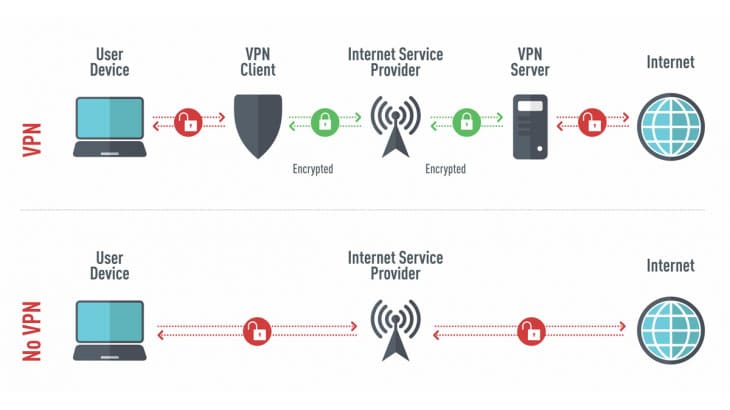
You can use a VPN to protect local WiFi traffic. Under the current WPA2 standard, an attacker can record all the data that goes through a WiFi network and decrypt it later if they get the password. VPNs make this more difficult by encrypting DNS requests and information that can be used for phishing.
Some users may think that creating a hidden network will protect their WiFi from hackers, but this will make devices like smartphones easier to track. A hidden WiFi network only broadcasts when there is a device connected to it: a device configured to continuously call out to the WiFi network to connect. This makes it easier for hackers to trick a configured device into connecting to a rogue access point or track it.
WIFI password
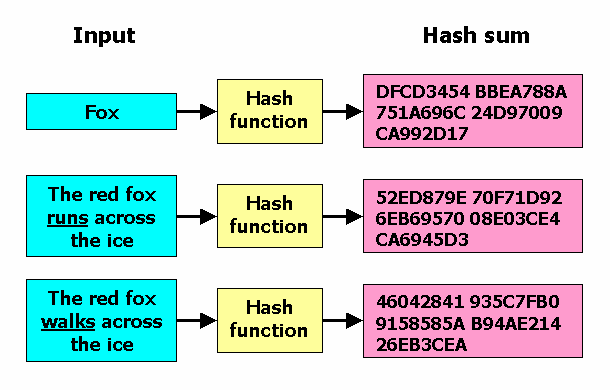
When the WiFi password is weak or already in use, hackers can easily bypass the hash using brute-force. All they need to do is put the hash in a tool like Hashcatit then compares with the list of existing passwords to see if any match. 
Employees working online should also know what their WiFi admin page looks like, because hackers may create another copy that looks exactly like the real one. Finally, the admin page only requires the admin password. Any website that asks for a Wifi password is potentially fraudulent to get information. Users should also raise awareness for their own safety.