Security
Instructions to get someone else's IP by Email, QR Code, Word File, Excel, PDF,…
How to track anyone's IP using Canarytokens is a skill you should know if you are interested in cybersecurity. IP...
Read moreDetailsList of SQL Injection Payloads
In this article, I will explain what SQL injection is, some common examples, explain how to find and exploit different...
Read moreDetailsDOS ATTACK from inside the network to the DHCP server
You can trick a DHCP server into not providing IP addresses to devices, completely blocking new connections by performing a...
Read moreDetailsLatest Active Burp Suite Pro 2024 + BugBounty Pro guide
Many of you who work on web servers or work in the security field have probably heard of a software...
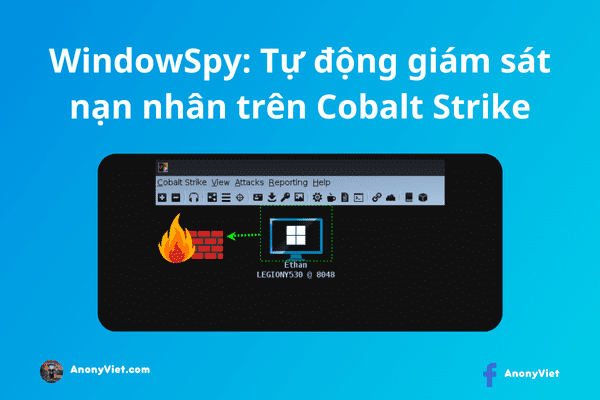
Read moreDetailsWindowSpy: Automatically monitor victims on Cobalt Strike
If you have learned about hacking tools like metasploit, nmap or brute force, you have probably heard about Cobalt Strike....
Read moreDetailsHow Hackers Bypass AV Infiltrate Windows with Autoit
In the age of digital technology, when network security becomes increasingly important, grasping the knowledge of how to attack and...
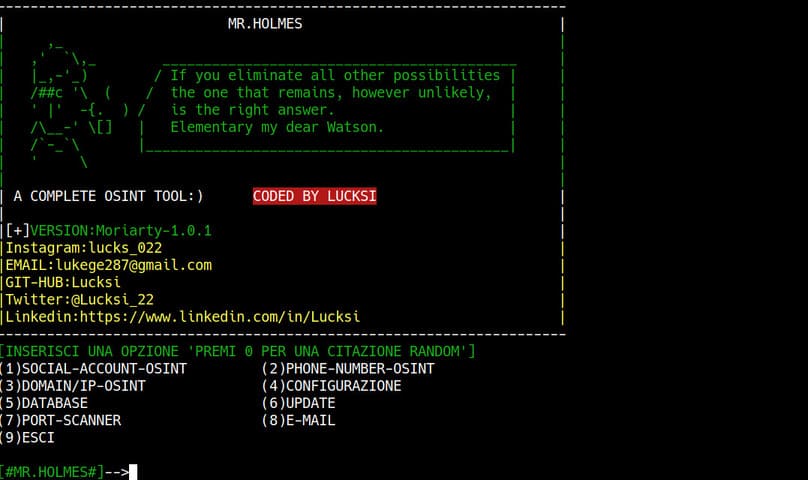
Read moreDetailsMr Holmes: Information gathering tool for OSINT people
Mr Holmes is an information gathering tool (OSINT). The main purpose of this tool is to get information about domain...
Read moreDetailsHow to use Hydra to attack Brute Force
In this article, we will talk about brute force tools Hydra. According to Wikipedia, Hydra is a parallel network login...
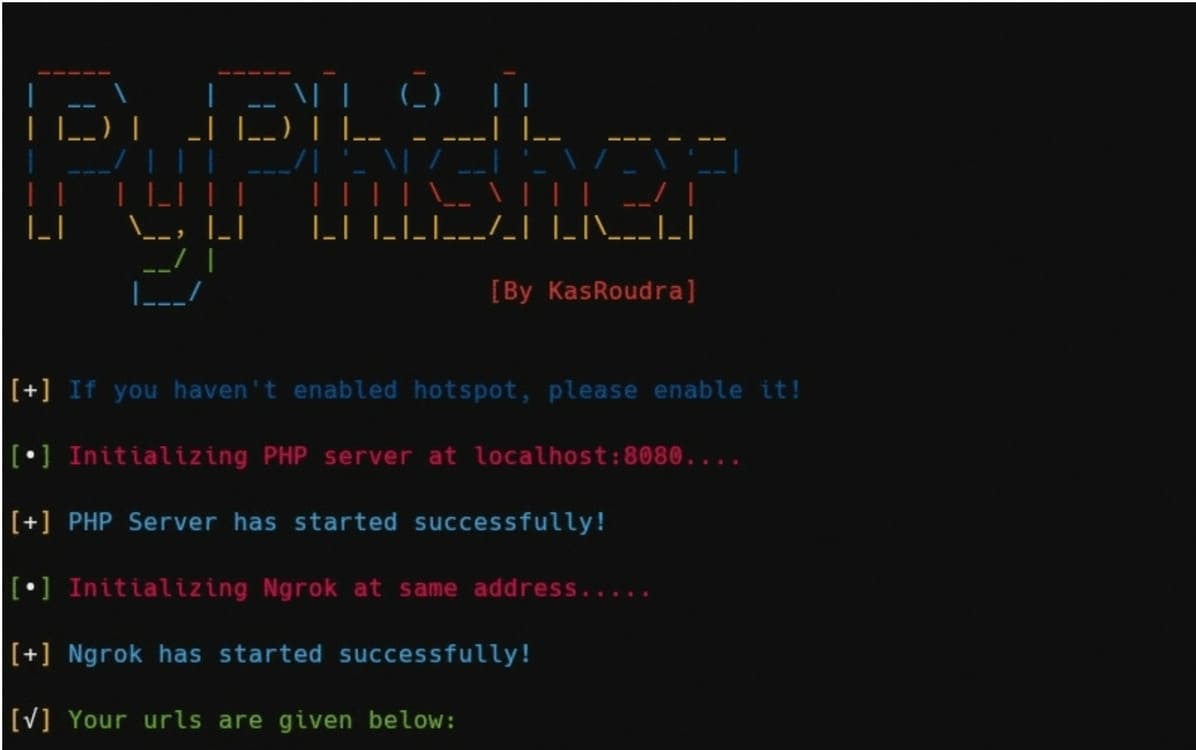
Read moreDetailsPyPhisher: Easy-to-use phishing tool with 65 available sites
PyPhisher is an ultimate phishing tool in python. Includes popular sites like Facebook, Twitter, Instagram, Github, Reddit, Gmail and many...
Read moreDetailsCareful! Keystroke sounds can reveal passwords to hackers
Do you know that Keystroke sounds can reveal passwords to hackers Are not? This is a serious problem that any...
Read moreDetails